Pew: Americans Know They're Getting Hacked, Do Nothing About It

Pew released a study exploring how Americans view cybersecurity. The organization focused on a few key factors: How many people have been affected by data breaches, how do they attempt to defend themselves, and how much does the typical American worry about encryption and other protections?
One Nation, Under Attack
The study found that 64% of Americans have been affected by some kind of data breach. Roughly 41% have seen fraudulent charges on their credit cards; 35% were notified that sensitive information has been compromised; 16% have lost control of their email accounts; and 13% have had their social media accounts taken. Others have been told their Social Security numbers were compromised or that someone tried to steal their identities.
These figures show that many attacks or breaches aren't just hypothetical problems. There are real people who pay the price when a new batch of stolen credit cards, leaked passwords, or Social Security numbers are published online. Besides the obvious concerns about their private data and financial health, this truth has also eroded many people's trust in the organizations that hold this information, whether that's the government or tech companies.
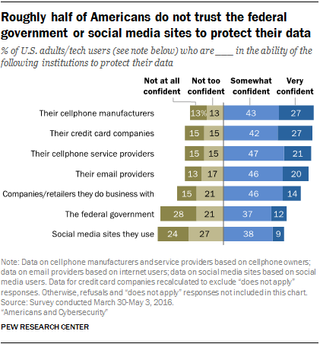
Indefensible
There are many ways for people to defend themselves if they don't trust others to do it for them. They could use secure communications tools, learn how to anonymize their web browsing, and limit what they share with tech companies. This isn't always easy--better protection often results in less convenience--but it shouldn't be nearly as daunting as it was a few years ago. So if people know they're at risk, they'll beef up their security, right?
Wrong. Pew found that roughly half of Americans don't take basic precautions. Some 54% of respondents use insecure Wi-Fi networks; 41% share their passwords with other people; 28% don't use screen locks to protect their smartphones; and 10% never update their operating system or mobile apps. People also use passwords across multiple sites and rely on simple, easily remembered passwords instead of more complicated (and secure) ones.
But all is not lost. Pew said that "majorities indicate that they do in fact take recommended steps such as utilizing different passwords from site to site or placing a security feature on their smartphones," and that 52% of respondents use two-factor authentication on at least some of their accounts. This led the research organization to describe the "way that users treat and manage their online passwords and their overall digital security" as "mixed at best."
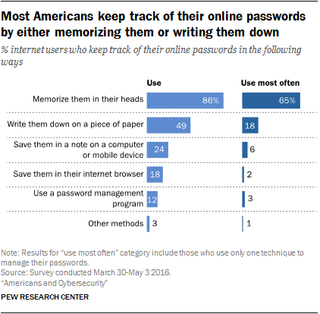
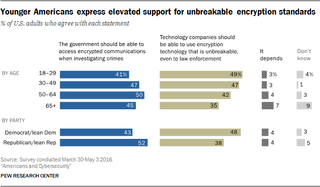
With Disinterest And Split Opinions From All
That split isn't restricted to how people defend themselves. They also can't agree on the encryption debate: 46% told Pew they want the government to be able to access "secure" communications while investigating crimes, and 44% said tech companies should be able to use encryption tools that even law enforcement can't access. (The remainder is comprised of people who don't know how they feel about the issue or think it depends on other factors.)
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Pew said Americans are also split on how much they're actually concerned about cybersecurity. That applies both to personal security--69% of adults said they don't care about the security of their passwords--and to matters of national security. People expect attacks on U.S. infrastructure (70%) or financial systems (66%) but also think the government can handle attacks on its agencies (69%) or critical infrastructure (62%) if they're attacked.
Another 61% think businesses could defend themselves. So even though many people don't think tech companies can protect their personal data, they think that businesses can keep their systems safe. At least they did--Pew said it's "worth noting that this survey was fielded prior to the revelations of some more recent, high-profile data breaches, including the hacking of the DNC email system and the breach of email accounts of Yahoo customers."
All this adds up to a jumbled mess. People know cybersecurity is a problem, because enough of them have been affected by hacks or cyber crimes, yet they don't take basic precautions. They don't think organizations can defend their personal data but also think they'd be able to handle attacks on critical infrastructure. And the encryption debate remains a virtual tie even as secure tools become more popular and easy to use. America, it seems, is divided.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
jdlech Theres really not a whole lot anybody can do to prevent being hacked. You install your firewall, your AV, your anti-malware, you back up regularly. Then you sit back and watch it happen anyway.Reply
One of the NSA memos that was on wikileaks says it all. When Congress ordered the NSA to help private industry create the strongest cyber security protocols possible back in the 1980s, the NSA immediately set about to sabotage all computer security. They deliberately sabotaged every security protocol since the 80s. And now we're supposed to think they're not responsible for all the security holes these days? They may not be doing all the hacking, but they sure had a hand in many of the holes hackers are using these days. You think they learned their lesson? You think they're not doing it anymore? Only a fool would trust anything the NSA says or does anymore.
For my part, I remain as anonymous as possible. I refuse to use social media and only give out throwaway email addresses. Yes, I use credit cards online, but they're prepaid throwaways and often depleted after two or three uses. I refuse to link accounts to one another. That cuts me off from posting at a lot of forums. But not getting targeted is more important than expressing myself. -
kittle Id say most people dont know HOW to protect themselves aside from just changing their online banking password.Reply
Add to that the pain in the backside it creates when you change a password, and then forget what you changed it to, and it becomes too much bother, so its skipped, pushed under the carpet and generally ignored.
At least until it REALLY starts to hurt: bank balance drained, car repossessed, home foreclosed on.. etc. but we dont hear much about those cases -
nutjob2 Reply19214205 said:Theres really not a whole lot anybody can do to prevent being hacked. You install your firewall, your AV, your anti-malware, you back up regularly. Then you sit back and watch it happen anyway.
One of the NSA memos that was on wikileaks says it all. When Congress ordered the NSA to help private industry create the strongest cyber security protocols possible back in the 1980s, the NSA immediately set about to sabotage all computer security. They deliberately sabotaged every security protocol since the 80s. And now we're supposed to think they're not responsible for all the security holes these days? They may not be doing all the hacking, but they sure had a hand in many of the holes hackers are using these days. You think they learned their lesson? You think they're not doing it anymore? Only a fool would trust anything the NSA says or does anymore.
For my part, I remain as anonymous as possible. I refuse to use social media and only give out throwaway email addresses. Yes, I use credit cards online, but they're prepaid throwaways and often depleted after two or three uses. I refuse to link accounts to one another. That cuts me off from posting at a lot of forums. But not getting targeted is more important than expressing myself.
Your tinfoil hat is on too tight. -
nutjob2 Why are stolen credit card numbers even mentioned? The fraudulent charges don't cost the card holders anything and it not the users who are losing control of credit card numbers, nor is it within their power to control them. The fact that banks have fought tooth and nail to delay chip cards and have still weakened them by not requiring pins and have created an online strategy for credit cards speaks loudly about the whole issue.Reply -
rantoc Bet the conclusion is password 123 is good and clicking on all links in suspicious mail is good right? The user is the weak link most of the time and if gullible its the perfect target.Reply -
velocityg4 People would take more steps to protect themselves. But it needs to be much easier. Websites should have a consistent method for logging in so password managers work 100% of the time. That they work consistently. To help password manager's websites should use a standardized login page, password update page and account creation page. So, password managers can always login and can always know to save a new user/password.Reply
Then the password managers need to keep working the same way all the time. If you have to, fire everyone in involved in the user interface. It should never change. You can change the technologies behind the scenes to make it more secure but the UI should always be the same. All the UI department should do is fix the UI when it breaks due to a change behind the scenes.
We are talking about people where you need to tell them to click on the beach ball (Chrome) not the blue E (Internet Explorer) for safer web browsing. If that beach ball disappears they think it is gone forever. Even if it is still installed they will never get it back.
These are people where you look in the downloads folder. Just about every file has been downloaded ten times. Either they finally realized it was downloaded or just gave up thinking the link was broken.
If you want them to improve security. You must make it easy for them to do so. Otherwise it will never happen. An inconsistent user experience makes a tool unusable. Most people have no grasp of what a computer is doing or how they are interacting with the software. They memorize a procedure. If that procedure changes, they are thrown for a loop. Which is why I stress the need for consistency.
There would have been no resistance to Windows Vista, 7, 8, 10, &c. If MS just stuck with the Windows XP interface. If they just updated all the security and technology behind the scenes but kept the GUI the same. Most people would have been happy.
As for their opinions on encryption. They don't know anything about it. Each of those pole question should also include the response choice of "I don't understand this computer stuff". In which case the answers would be 1% for strong encryption, 0.1% against, 98.9% doesn't understand. -
The Reebo "52% of respondents use two-factor authentication on at least some of their accounts"Reply
I can only assume that one of the following applies:
A) The people surveyed think that "Two-factor" means you have to give your email address AND your password
B) The survey is hopelessly skewed towards the high end of tech savvy.
I simply refuse to believe that 52% of Americans know what two-factor authentication is, let alone use it.
Most Popular

