'Spy Banker Telax' Trojan Stealing Banking Credentials Through Facebook And Google Cloud Servers
Security researchers from Zscaler, a company that offers security solutions to other organizations, uncovered a new malware campaign that uses the Spy Banker banking malware. Its main targets seem to be Portuguese-speaking people from Brazil.
The Spy Banker malware was first detected in 2009, but it has since evolved to take advantage of social media and get people to click on bit.ly URLs that promise things such as coupons for certain products or free downloads for apps such as Whatsapp or the Avast antivirus. Some victims have also been infected by drive-by downloads.
The attackers have been using Google Cloud Servers to host a PHP file that does a 302 redirect to download the initial Spy Banker Downloader Trojan, which is responsible for downloading the Spy Banker Trojan Telax.
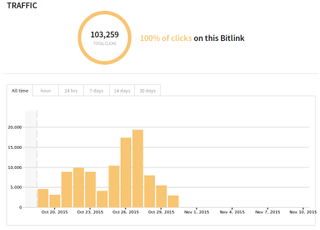
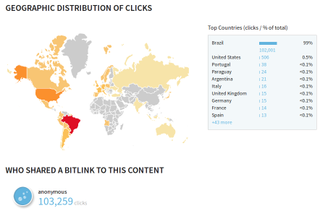
In a particular case being analyzed by Zscaler researchers, the bit.ly link pointing to an “receitanet.com” executable file was clicked more than 103,000 times, of which 102,000 clicks happened on Facebook. The receitanet.com executable was posing as Brazil’s federal revenue online tax returns service.
The final payload, Spy Banker Trojan Telax, is capable of stealing the banking credentials of users. The payload also checks for the existence of virtual environments such as VMWare or VirtualBox and includes 32-bit and 64-bit rootkits, which can obtain more persistence on users’ machines. Zscaler researchers said that the Spy Banker Telax trojan uses no vulnerability exploits, instead relying only on social engineering to infect users.
Google has apparently already cleaned its servers of the uncovered malware:
“It is important to note that Google has already cleaned up the cloud servers being currently redirected by these two active sites and hence the infection cycle will fail with a 404 Not Found message,” Zscaler said.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
______________________________________________________________________

Lucian Armasu joined Tom’s Hardware in early 2014. He writes news stories on mobile, chipsets, security, privacy, and anything else that might be of interest to him from the technology world. Outside of Tom’s Hardware, he dreams of becoming an entrepreneur.
You can follow him at @lucian_armasu. Follow us on Facebook, Google+, RSS, Twitter and YouTube.
-
f-14 i actually noticed this one back around june when dealing with a client, i installed alot of ad blocker software that blocks the 3rd party links over their network first before studying the actual problem figuring it was just the amount of people using porn sites. yes the porn sites are infected also for example youporn, but those were redirecting to other porn sites for the most part, and fishing for email for the most part; and weren't where my trace routes were leading to.Reply
i know for a fact the 404 not found errors didn't start until mid to late september FME while i kept investigating as my site black list was causing discord amongst the ranks in their workplace, which i did not count on due to the prevalence of mobile device alternatives. security is still a work in progress in brazil as employers are learning the hard way about employee's leaching internet via their mobile phones.
p.s. blocking skype altogether for organizations outside of europe or north america will probably lose your contract. (i was just covering the bases)
Most Popular




