AMD TPM Exploit: faulTPM Attack Defeats BitLocker and TPM-Based Security (Updated)
Zen 2 and Zen 3 are vulnerable to voltage glitching.
Update, 3:15pm PT: AMD shared a comment on the new vulnerability disclosure, which we've added below.
Original Article, 9:16am PT : A new paper released by security researchers at the Technical University of Berlin reveals that AMD's firmware-based Trusted Platform Module (fTPM / TPM) can be fully compromised via a voltage fault injection attack, thus allowing full access to the cryptographic data held inside the fTPM in an attack called 'faulTPM.' Ultimately this allows an attacker to fully compromise any application or encryption, like BitLocker, that relies solely upon TPM-based security.
The researchers accomplished this feat using off-the-shelf componentry that cost roughly $200 to attack AMD's Platform Security Processor (PSP) present in Zen 2 and Zen 3 chips. The report does not specify if Zen 4 CPUs are vulnerable, and the attack does require physical access to the machine for 'several hours.' The researchers have also shared the code used for the attack on GitHub and a list of the inexpensive hardware used for the attack.
The report is especially pertinent now that Microsoft has added TPMs to its system requirements for Windows 11, a move met with resistance due to its deleterious impact on gaming performance even when it works correctly, and severe stuttering issues when it does not. Yes, the TPM requirement is easily circumvented. Still, Microsoft's push for the feature has increased the number of applications relying solely on TPM 2.0 for security features, thus increasing the cross-section of applications vulnerable to the new faulTPM hack.
We reached out to AMD for comment, and the company issued the following statement to Tom's Hardware:
“AMD is aware of the research report attacking our firmware trusted platform module which appears to leverage related vulnerabilities previously discussed at ACM CCS 2021. This includes attacks carried out through physical means, typically outside the scope of processor architecture security mitigations. We are continually innovating new hardware-based protections in future products to limit the efficacy of these techniques. Specific to this paper, we are working to understand potential new threats and will update our customers and end-users as needed.” — AMD spokesperson to Tom's Hardware.
To our understanding, the papers released at ACM CCS 2021 centered around a glitching attack, but did not use the attack vector to compromise the TPM. Instead, the attack was used to defeat Secure Encrypted Virtualization. As such, this new research reveals a novel method whereby AMD's fTPM can be fully compromised.
As a reminder, discrete TPMs plug into a motherboard and communicate with the processor to provide security, but the external bus between the CPU and TPM has proven to be hackable with multiple different approaches. As such, the firmware TPM, or fTPM, was created to embed the functionality inside of the chip, thus providing TPM 2.0-class security without an easily-hackable interface exposed to attackers.
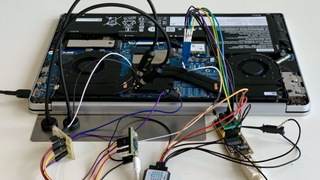
The faulTPM attack centers on attacking the fTPM, which, to our knowledge, hasn't been possible before. As you can see from the above picture of the Lenovo Ideapad 5 Pro system the researchers used to execute the attack, this isn't a simple endeavor and will require a few hours of physical access to the machine. In the case of nation-states or the highest-end levels of espionage or corporate espionage, this is fairly easy to accomplish, though.
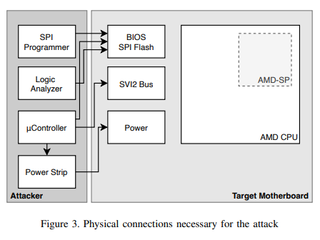
Here we can see the multiple connections to the power supply, BIOS SPI chip, and SVI2 bus (a power management interface) the researchers used on the Lenovo test subject. These connections are used to execute a voltage fault injection attack against the PSP present in Zen 2 and Zen 3 CPUs, thus acquiring the chip-unique secret that allows the decryption of the objects stored within the TPM. Here's the step-by-step method of attack:
- Backup the BIOS flash image using an SPI flash programmer
- Connect the fault injection hardware and determine the attack parameters (4.1)
- Compile & deploy the payload extracting the key derivation secret (4.3)
- Start the logic analyzer to capture the extracted key derivation secrets via SPI
- Start the attack cycle on the target machine until the payload was executed successfully
- Parse & decrypt the NVRAM using the BIOS ROM backup and payload output with amd-nv-tool
- Extract and decrypt TPM objects protected by this fTPM with amd ftpm unseal
The researchers successfully gained full access to the TPM and the data sealed within, thus allowing them to compromise the BitLocker Full Disk Encryption (FDE) on the device. As one would imagine, this would lead to full access and control of the device, and all of the data contained therein, in relatively short order.
By default, BitLocker uses a TPM-only mechanism to store the keys, but users can manually enable a PIN setting that allows the user to assign a PIN code that works in tandem with the TPM-based mechanisms. However, these PIN codes aren't enabled by default and are vulnerable to brute-force attack methods. Simple numerical PINs are relatively easy to break, but more rigorous text-based passphrases are harder to crack.
As mentioned, this attack also exposes applications that only use TPM-based security, while applications with multiple layers of security will be more secure.
The researchers contend that this attack vector isn't easy to mitigate due to the voltage fault injection, so the earliest intercept point for AMD to fix the issue would presumably be with its next-gen CPU microarchitectures. According to the researchers, Intel's Converged Security and Manageability Engine (CSME) prevents these types of attacks.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.

Paul Alcorn is the Managing Editor: News and Emerging Tech for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
lightofhonor I would be more concerned with someone having access to my disassembled PC for several hours than the risk of this attack.Reply -
PEnns "The attack does require physical access to the machine for 'several hours.'"Reply
Seriously?? If somebody has access to your PC that long, that "hack" is the least of your problems.
This pathetic story is typical of the anti-AMD BS articles that get posted here lately. Wouldn't surprise me in the least if it turns out that Intel funded the whole pathetic "hack"! -
drivinfast247 Crap! Just yesterday some dweeb with glasses and a pocket protector came to my door and asked to see my PC for a bit! Why would I have thought anything bad would come of it!?Reply -
JamesJones44 Reply
Please, if this were an Apple attack it would be front page of every news outlet on the planet. This isn't just an AMD smear article, you see these articles about about "hacks" for physical hardware all the time. I read one just the other day about compromising Samsung Exynos CPU security with a physical hack. Google's project zero puts out reports like these monthly.PEnns said:"The attack does require physical access to the machine for 'several hours.'"
Seriously?? If somebody has access to your PC that long, that "hack" is the least of your problems.
This pathetic story is typical of the anti-AMD BS articles that get posted here lately. Wouldn't me surprise me in the least if it turns out that Intel funded the whole pathetic "hack"! -
ralfthedog Replylightofhonor said:I would be more concerned with someone having access to my disassembled PC for several hours than the risk of this attack.
If the data on your system is very valuable, there is a risk that people will break into your offices and walk off with your hardware. If the data is highly encrypted, this is much less of a threat. The key is to use both full disk hardware encryption and high bit depth encryption at the file level. If you wish to add software based file system encryption, that is also an option.PEnns said:"The attack does require physical access to the machine for 'several hours.'"
Seriously?? If somebody has access to your PC that long, that "hack" is the least of your problems.
This pathetic story is typical of the anti-AMD BS articles that get posted here lately. Wouldn't me surprise me in the least if it turns out that Intel funded the whole pathetic "hack"!
Remember, corporations are not worried about the loss of the hardware, they are worried about the loss of the data on the hardware. -
Dr3ams As an average user, I could care less about this article. Also...a company or government agency that works with highly sensitive data is going to have more than hardware and software security to protect their property.Reply -
FlyingBuzz This type of attack might be harmful for game console business. Since access is suppose to be locked and keys are suppose to be hidden.Reply
Other than that, I dont think we have to worry.. -
Vanderlindemedia It's a hack that, cant really be a danger in the wild. You'll need a couple of hours physical access to a already stripped machine.Reply
It would be dangerous if there was a hack that was able from user space to read it's TPM. -
hotaru.hino Any vulnerability, no matter what the requirements are, may lead to finding other vectors of attack that could be easier or more convenient now that they're aware of a weak spot. If you dismiss every "requires physical access" vulnerability as a non-problem, you'll be blindsided by someone who found a way to remove that requirement. Or lowered the bar enough to make it convenient to do.Reply
As an aside, speedrunners thought a lot of strats were tool-assisted (TAS) only; i.e., humanly impossible. But they used what the TAS did as a starting point to find a vector into doing something like RNG manipulation or arbitrary code execution that could be done by sufficiently skilled humans. -
Charogne I heard there is a hack on windows that, if you give access to a evil russian hacker for several hours, with all your passwords, he can do lot of stuff on your pc.Reply
Most Popular




