Kaspersky Says 'The Equation Group' Is A Unique And Dangerous Threat
Kaspersky Lab discussed a threat that has been in operation for nearly two decades. According to the firm, the cyber threat known as "The Equation Group" is unlike anything it has dealt with over its 60 years of work in the security business.
"They use tools that are very complicated and expensive to develop, in order to infect victims, retrieve data hide activity in an outstandingly professional way, and utilize classic spying techniques to deliver malicious payloads to the victims," said Kaspersky.
Included in this arsenal of tools employed by The Equation Group is an advanced program that can rewrite the firmware on hard drives, and this is what makes The Equation Group so dangerous. By being able to reprogram the firmware on hard drives, a malicious code can be stored inside of the device and would survive virus scans, and even survive reformatting the hard drive.
This means the virus cannot be removed without flashing the hard drive's firmware, which no one outside of the manufacturer is setup to do, or replacing the hard drive. Given that this is a new type of threat, it's likely that even hardware experts would never figure out how the virus kept coming back.
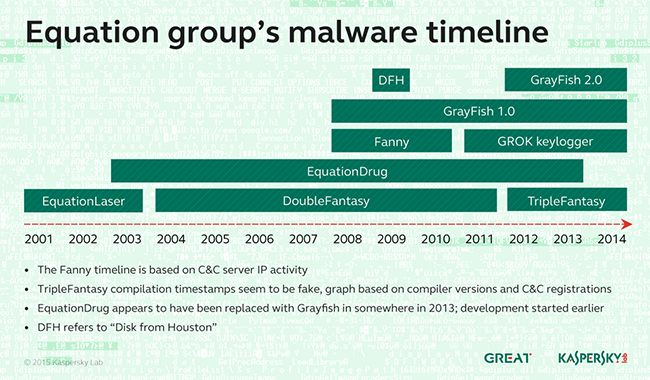
The Equation Group has other tools available, too. To date, the group has been responsible for the distribution of several threats such as DoubleFantasy, Fanny and EquationDrug. What is more concerning is the way in which these threats manage to start and spread.
Many of the threats were initially spread without using the Internet. DoubleFantasy is one such example; after a scientific conference in Houston, Texas, the attending members of the conference were given a copy of the conference materials on an optical disk. The DoubleFantasy software was installed onto the disks and infected systems when used.
Fanny is another threat developed by The Equation Group that spreads in a unique way, by infecting USB devices to gain access to systems not connected to the network. The software does this by determining when it is connected to a system that lacks an Internet connection, and then it uses the USB devices and another computer with an Internet connection to transport data to and from the non-networked system.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
With so many advanced ways to attack users, The Equation Group stands as a severe threat to cybersecurity.
Follow us @tomshardware, on Facebook and on Google+.
-
brandonjclark You call this news? You mention the "Equation Group" like they are some unknown hacker group.Reply
IT'S THE NSA!
http://www.stuff.co.nz/technology/digital-living/66279485/nsa-hiding-equation-spy-program-on-hard-drives -
brandonjclark The US National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world's computers, according to cyber researchers and former operatives.Reply
That long-sought and closely guarded ability was part of a cluster of spying programs discovered by Kaspersky Lab, the Moscow-based security software maker that has exposed a series of Western cyberespionage operations.
Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists, Kaspersky said. -
thor220 I see this is making the rounds. If anyone takes the time to read the source article, Kaspersky doesn't actually provide any evidence to back up their claim that this actually exists and who it's linked to.Reply
They merely provide a stat sheet about it listing how it infects, what it does, ect. It's very easy for a company to make this sort of thing up if your in the anti-virus business.
Do remember that Kaspersky is a Russian company and that Russia's relations with the USA aren't good at all.
-
agnickolov Here's a far better written article on the subject from Ars Technica:Reply
http://arstechnica.com/security/2015/02/how-omnipotent-hackers-tied-to-the-nsa-hid-for-14-years-and-were-found-at-last/
-
BobDDDD Someone needs to invent an Enigma machine for computers, whereby a random challenge code is issued before every .exe file is launched, requiring a binary response that is randomly changed every 13ms.Reply -
rokit NSA being responsible(in one form or another) is obvious. But Kaspersky can't be trusted because they're screaming on another wolf while pretending to be a sheep.Reply -
PepiX 60 years of work in the security business? Is this translated from russian? Isn't it 16 years?Reply -
Christopher1 ReplyNSA being responsible(in one form or another) is obvious. But Kaspersky can't be trusted because they're screaming on another wolf while pretending to be a sheep.
Kaspersky is not a sheep, but they are not a wolf either. They are more the shepherd trying to protect the sheep armed only with a shepherd's crook, while the wolves are using invisibility suits to get close to and steal the sheep. -
Impulseman45 Ah, consumers can't upgrade the firmware on hard drives my ass. We have been able to this for years. All the major OEMs and Hard Drive manufacturers have utilities that do this very thing because sometimes the firmware they ship is buggy or not as fine tuned as it could be and they make a new one. Just go to HP Support and find drivers for just about any computer and you will see Hard Drive firmware updates and even firmware updates for CD,DVD drives as well. Where the hell has Kaspersky Labs been the last decade or more, under a rock? And we are suppose to trust a company that comes out of left field with remarks like this. Hey guys is the 21st century now its time to have a look at the internet and see things as they really are.Reply