MIT Finds Apple M1 Vulnerability, Demos PACMAN Attack (Update)
Chomping away at Arm chip security

Apple's M1 is fast and devastatingly power-efficient, but like all CPUs, it isn't bulletproof. MIT Computer Science & Artificial Intelligence Laboratory (CSAIL) scientists unveiled a new attack methodology that exploits a hardware vulnerability in the Apple M1 series of chips by using a new PACMAN technique to steal data. The team used an Apple M1 processor as the demo chip for the exploit and tells us that it hasn't replicated it with other Arm processors. The researchers claim the attack can even potentially access the core operating system kernel, thus giving attackers full control of a system through a combination of software and hardware attacks. However, the software portion of the attack does rely upon an existing memory corruption bug to work, so it isn't a silver bullet that will bypass all security.
Notably, the researchers tell Tom's Hardware that the exploit does not require physical access to the machine, so it can be exploited remotely. The researchers say the M1's hardware vulnerabilities can't be patched with software and the MIT team believes the vulnerability could impact future Arm mobile devices, and likely even future Arm desktop PCs, if it isn't mitigated in future architectures. "Any chip that uses speculative execution to evaluate and operate on pointer authentication signed pointers (and handles nested mispredicts eagerly) could potentially be vulnerable to PACMAN," said Joseph Ravichandran, a researcher with the MIT team. That means this could possibly impact chips from other Arm vendors that support pointer authentication, such as Qualcomm and Samsung, but those chips haven't been tested yet.
The attack targets Arm's Pointer Authentication feature through a side-channel attack on the chips' speculative execution engine. Pointer Authentication is normally used to verify software with cryptographic signatures called pointer authentication codes (PACs), thus preventing malicious attacks on the memory via software vulnerabilities. These software attacks usually consist of techniques that exploit memory corruption, like buffer overflows, to take full control of a program. As such, it relies upon an existing software bug that can read and write to memory.

The PACMAN technique comprises 'guessing' a value for the PAC while using a speculative execution attack, much like we see with Spectre and Meltdown, to leak the PAC verification results via microarchitectural side channels. As a reminder, a side channel attack allows data theft by observing or exploiting a secondary effect of an operation on a system. This allows the researchers to find the correct PAC value, thus sidestepping protection against software vulnerabilities. However, it requires an existing memory corruption bug in the software to work. "PACMAN can only take an existing bug that pointer authentication protects against, and unleash that bug's true potential for use in an attack by finding the correct PAC," said the researchers.
The researchers say the PACMAN attack works across privilege levels, "implying the feasibility of attacking a PA-enabled operating system kernel."
When asked about the data exfiltration rate (i.e., how fast data can be stolen), the team tells Tom's Hardware, "It's hard to say since data exfiltration with this attack will be very dependent on the exact gadget used. Our proof of concept exploit takes 2.69 milliseconds per PAC guess (so worst-case 2.94 minutes per pointer). This may be longer in a fully integrated end-to-end attack."
The researchers propose three methods to protect against the PACMAN attacks. One method is to modify the hardware or software to prevent PAC verification results from being used in the speculative execution process. However, the researchers warn that this approach could have a significant performance penalty. Another suggestion is to adapt previously-developed Spectre mitigation techniques to PACMAN. Finally, patching memory corruption vulnerabilities would also prevent the attacks.
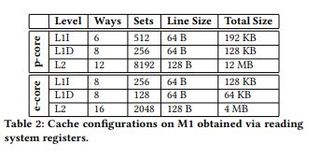
The report also documents the team's reverse-engineering of the Apple M1 processors' memory hierarchy, which in turn reveals many previously undisclosed details of the chip's architecture.
The MIT team was partly funded by the National Science Foundation (NSF) and the Air Force Office of Scientific Research (AFOSR). The MIT CSAIL team will present its PACMAN: Attacking ARM Pointer Authentication with Speculative Execution paper at the International Symposium on Computer Architecture on June 18, outlining its new attack methodology.
The team disclosed the vulnerability to Apple several months in advance, so it has engaged in responsible disclosure. However, the team hasn't filed a Common Vulnerabilities and Exposures (CVE) number but plans to file one soon.
EDIT — An Apple spokesperson has now provided us with a statement on the matter:
“We want to thank the researchers for their collaboration as this proof of concept advances our understanding of these techniques. Based on our analysis as well as the details shared with us by the researchers, we have concluded this issue does not pose an immediate risk to our users and is insufficient to bypass operating system security protections on its own.”
Apple's statement points out that the vulnerability "on its own" isn't a threat, but it is unclear if this refers to the hardware component of the attack or the software component. The attack explicitly leverages combined hardware+software vulnerabilities, so we're following up for clarification on the statement.
Update 6/10/2022 8:10am PT: Added additional details from the MIT team, which says this vulnerability is not proven to be present in other Arm chips.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.

Paul Alcorn is the Managing Editor: News and Emerging Tech for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
Title: "MIT Finds Apple M1 Vulnerability"Reply
Article: "MIT Computer Science & Artificial Intelligence Laboratory (CSAIL) scientists unveiled a new attack methodology that exploits a hardware vulnerability in Arm processors"
The bad faith is strong in this one. -
PaulAlcorn ReplyNolonar said:Title: "MIT Finds Apple M1 Vulnerability"
Article: "MIT Computer Science & Artificial Intelligence Laboratory (CSAIL) scientists unveiled a new attack methodology that exploits a hardware vulnerability in Arm processors"
The bad faith is strong in this one.
This was an error on my part. Out of an abundance of caution, I pointed out that this vulnerability should impact all newer Arm chips, as the pointer feature is in those versions. However, after speaking with the MIT researchers they emphasized that this is only proven to work on the Apple M1. I updated the text to reflect the new information. -
Elterrible So, no memory corruption and no issue? If it literally is that simple, then I wouldn't call it an unpatchable flaw, if it were, it wouldn't need a second exploit to be vulnerable.Reply -
PaulAlcorn ReplyElterrible said:So, no memory corruption and no issue? If it literally is that simple, then I wouldn't call it an unpatchable flaw, if it were, it wouldn't need a second exploit to be vulnerable.
The hardware vulnerabilities can't be patched in software. The PACMAN attack exploits a combination of both software and hardware vulnerabilities. -
InvalidError Reply
Practically every hardware exploit that isn't an outright data leak relies in code weaknesses to some degree, which is why every side-channel exploit can be mitigated by re-arranging code to whiten its signature (ex.: add dummy code to balance out performance and memory accesses between data-dependent code paths) at the expense of performance.PaulAlcorn said:The hardware vulnerabilities can't be patched in software. The PACMAN attack exploits a combination of both software and hardware vulnerabilities. -
jeremyj_83 Reply
The team used an Apple M1 processor as the demo chip for the exploit and tells us that it hasn't replicated it with other Arm processors.Nolonar said:Title: "MIT Finds Apple M1 Vulnerability"
Article: "MIT Computer Science & Artificial Intelligence Laboratory (CSAIL) scientists unveiled a new attack methodology that exploits a hardware vulnerability in Arm processors"
The bad faith is strong in this one. -
missingxtension Funny how i fist read about this on a mac site from google news and they specifically stated (mac site) that it can't be exploited remotely and was no concern. 🙉🙉Reply -
KyaraM So Apple is actively lying to their customers about the potential threat, especially if they claimed it cannot be exploited remotely. Good, one more reason to never buy their overpriced garbage. At least both Intel and AMD where honest about the severity of the issue back then.Reply
I really hope the issue turns out to be confined to them, though. Considering how many Qualcomm or Samsung ARM processors are on the market in smartphones today, this feels like it could become a second Meltdown/Spectre situation, though there was a lot of overblown scare there, imho. It was still undeniably an issue, just like this could become one.
Most Popular


