How Secure Is Your Favorite Messaging App? EFF Aims To Find Out
The Electronic Frontier Foundation (EFF), together with Julia Angwin at ProPublica and Joseph Bonneau at the Princeton Center for Information Technology Policy, joined forces to create a campaign for using secure messaging apps and tools.
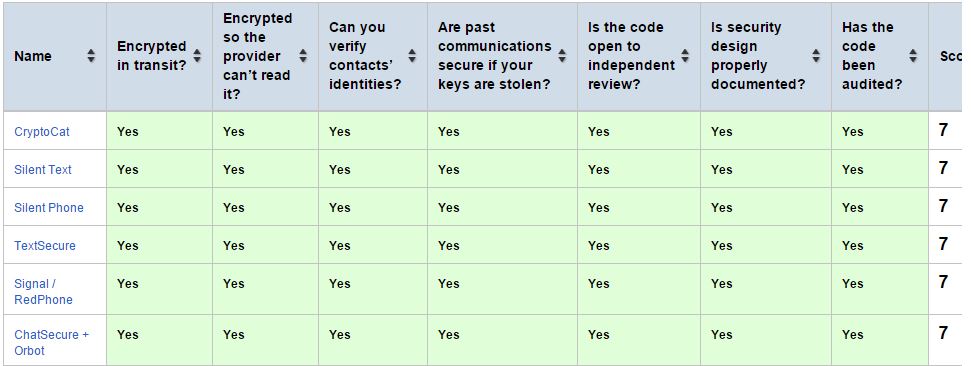
The group researched many messaging applications on multiple platforms and created a scorecard based on seven criteria that these apps must fulfill:
Is your communication encrypted in transit? Is your communication encrypted with a key the provider doesn't have access to? Can you independently verify your correspondent's identity?Are past communications secure if your keys are stolen?Is the code open to independent review? Is the crypto design well-documented? Has there been an independent security audit? (in the past 12 months)
The apps the group found to fulfill all of these criteria and be the most secure are OpenWhisper Systems' TextSecure SMS/chat application and its encrypted-voice Signal/RedPhone applications (one is for iOS, the other for Android), the OTR-based ChatSecure and Cryptocat, and Silent Circle's "Silent Text" and "Silent Phone" apps.
Signal/RedPhone and Silent Phone both use Phil Zimmerman's (who is part of Silent Circle) ZRTP protocol, with some modifications. Silent Text, TextSecure and CryptoCat/ChatSecure all use different protocols. Cryptocat and ChatSecure use the older OTR protocol, Silent Text uses SCIMP, and TextSecure is based on the Axolotl protocol, which is meant to be an improvement in security over both OTR and SCIMP while also being an asynchronous messaging system. With OTR and SCIMP, the user has to be online to receive the messages. TextSecure users can get them even if they were online when receiving the message.
One advantage TextSecure and the OTR-based ChatSecure and CryptoCat have over Silent Text is that they are open source, so the code can be easily reviewed by anyone, making it harder for backdoors to be introduced in their code bases. Being open source, they are also both free of charge. Silent Text is part of the Silent Circle package that starts at $12.95 per month.
The apps that came very close to being in the group of winners, but failed in one of the criteria, include the OTR plugin for Pidgin and Adium chat applications, because the plugin hasn't been audited in the past year by an independent security team. Retroshare, a P2P application, suffers from the same issue.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Mailvelope is one of the easiest PGP tools out there for Chrome and has been audited, but because it's using PGP, conversations can be encrypted with only one key; if stolen, it can be used to decrypt all past conversations. Therefore, it fails to meet one of the research group's main criteria.
Mxit and QQ, a South African social network and an IM client, got zero points on the scorecard because they don't even encrypt the data in transit (TLS). Popular apps such as Yahoo Messenger, Blackberry Messenger, AIM, Hushmail, Kik and Secret do have TLS encryption, but fail on all of the other criteria.
TLS encryption means the data is still accessible by the provider and anyone who might hack the provider's servers. TLS is also not one of the most solid ways to encrypt data, and it can often be bypassed, especially by sophisticated or well-funded attackers. Despite all of its problems, though, it's the easiest for service providers to implement. It also gives said providers the ability to data-mine the conversations to serve target ads or for other purposes.
Whatsapp, Facebook Chat, Google Hangouts, Snapchat and Skype are slightly better, scoring two points each. The first four get a point for being audited in the past year, while Skype doesn't. However, Skype gets one for "provider can't read the data" criteria. Considering there have been many reports of Microsoft building "legal intercept" technology for Skype (strangely enough, years before it acquired the chat service) and complying with authorities for Skype data, that point is probably not deserved.
Skype used to have much more secure peer-to-peer technology to the point where NSA wanted to pay as much as billions of dollars for a wiretap solution for the service, but fortunately for the NSA (and unfortunately for us), when Microsoft acquired Skype, the company changed its infrastructure into a much more centralized one, supposedly to improve battery efficiency on mobile devices. That move, however, made Skype much easier to wiretap.
Skype's scoring isn't the only one that's slightly inaccurate, though. The group gives Threema and Telegram a point for the same "provider can't read the data" category. However, in reality Threema only uses Perfect Forward Secrecy (to rotate the keys) in transit, but the messages use the same key when they are encrypted client-side. Telegram uses end-to-end encryption (called "Secret Chats"), but it's not enabled by default, which means the vast majority of its users won't benefit from it in most cases. Just like Threema, it also only uses forward secrecy server-side.
Although EFF's scorecard isn't perfect, it's still helpful to get a rough idea which of the many chat apps out there are truly secure. For now, OTR remains the standard protocol for secure chat applications, with the benefit of being cross-platform. TextSecure is the state-of-the-art protocol for secure messaging, but it's only available on Android right now. Fortunately, there are plans to make both an iOS and a desktop version soon.
As for secure email, the standard secure protocol remains PGP for now, despite the fact that it has the major weakness of keeping the same key for all conversations and generally being hard to set up by most users. The good news is that there are security engineers working on secure protocols for email that are both more secure and easier to use than PGP.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Christopher1 Changing Skype to a centralized infrastructure did make it easier to wiretap and the "This will improve battery life for mobiles!" thing was a LoC.Reply
I believe that Microsoft was either threatened by the feds or given a big payout to centralize their infrastructure and make it easier to wiretap Skype calls.