MacOS Malware Targets Swiss Bank Customers Via Phishing Emails
Trend Micro, a Japanese security software company, has detected a new piece of malware for the macOS platform that seems to be targeting Swiss bank users. The malware, which Trend Micro called OSX_DOK, spread via a phishing campaign.
How The Infection Began
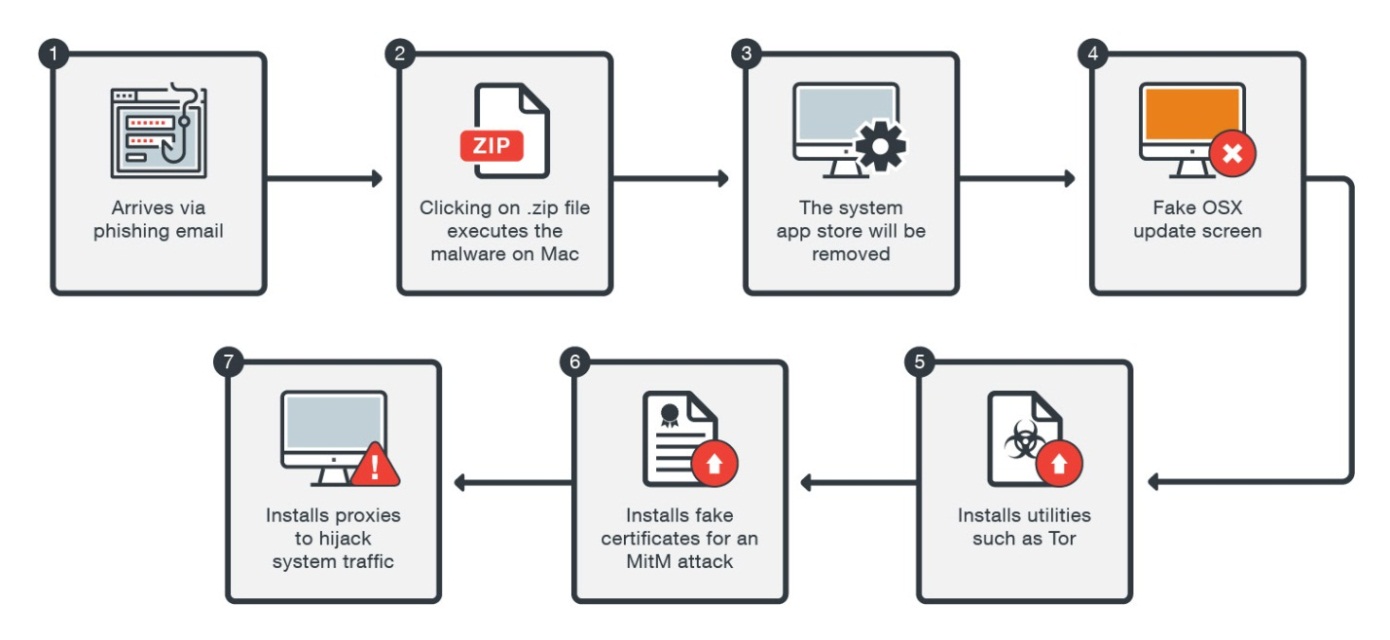
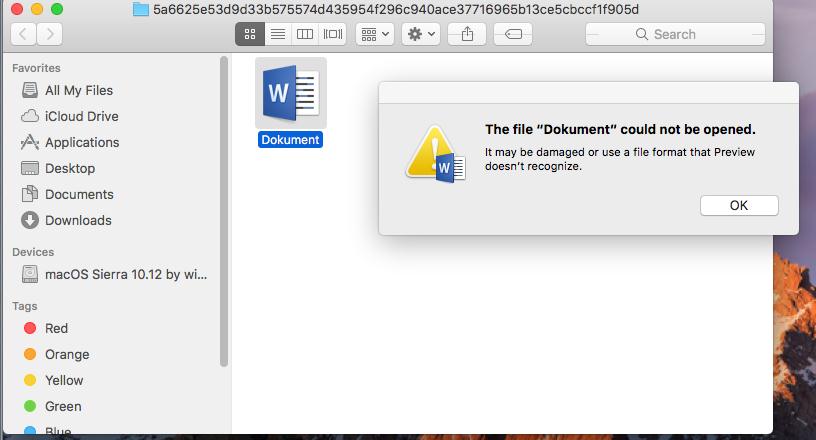
The malware authors would first send the victims a phishing email that contained either .zip or .docx files that were infected with the malware. When the users clicked on the file, a warning window would appear claiming that the file couldn’t be opened.
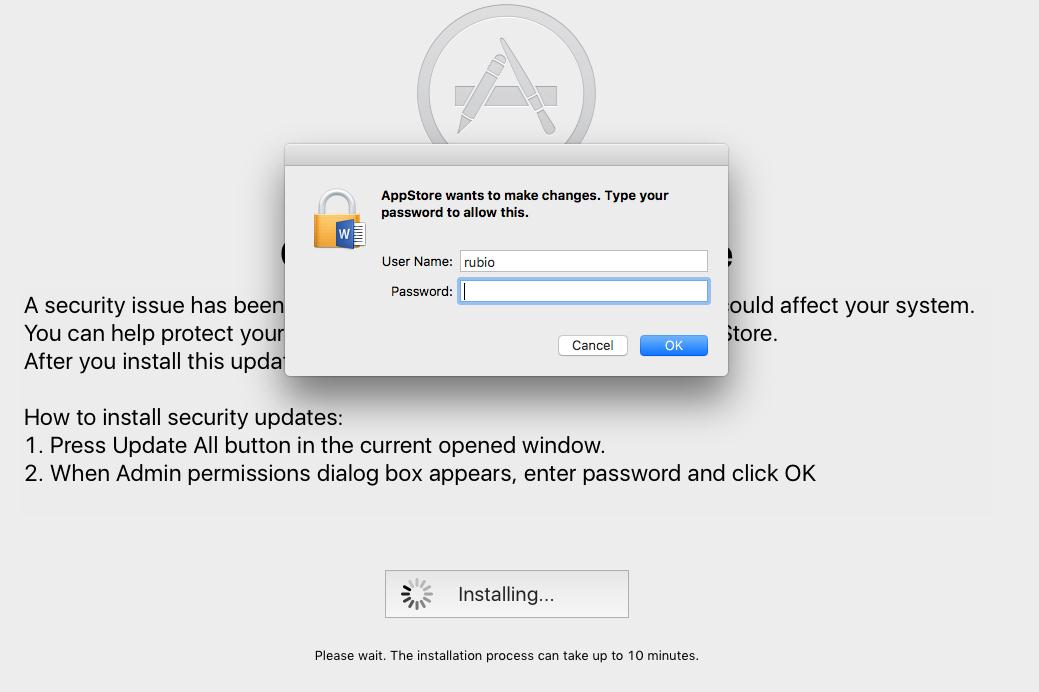
The malware would then delete the App Store on the system and prompt a fake macOS update screen. Afterward, it would ask for a password, typically required for macOS updates, so it can run its own commands as root.
Once it has root privileges, the malware can begin downloading other utilities, such as fake certificates, which it installs on the system in order to perform man-in-the-middle attacks against the victims’ internet traffic.
Bypassing MacOS Security Protections
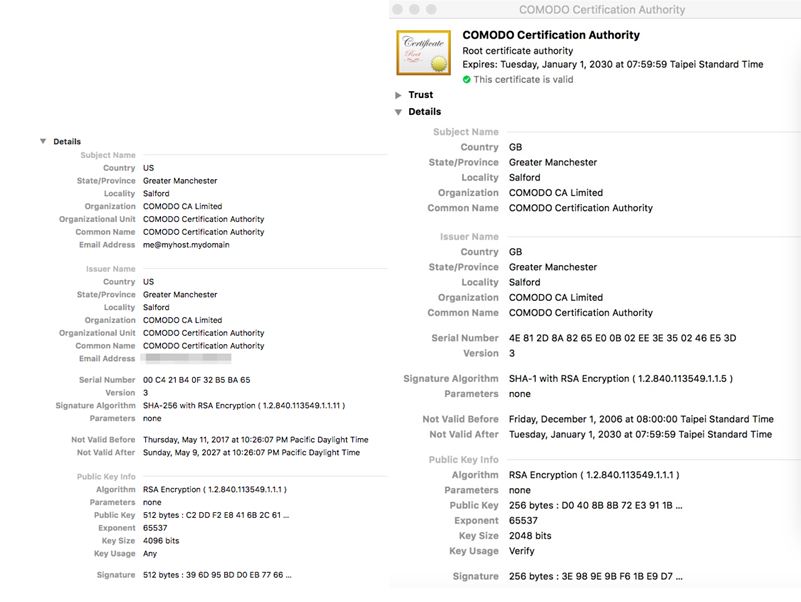
By default, macOS will allow applications to run if they’ve been signed by a “developer,” which in this case may have been a dummy account or an account stolen from a real Mac App Store developer. According to Trend Micro, the time stamp on the certificate is new, which could mean that it was obtained specifically for the attack.
The fake certificate imitates Comodo root certificates, but it doesn’t contain a Comodo Certificate Authority seal that would certify its validity, as seen in the comparison below.
The malware didn’t work in the Chrome and Firefox browsers, because both of them use their own root certificates. Of the major browsers, only Safari uses macOS' root certificate system.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Capturing Banking Credentials
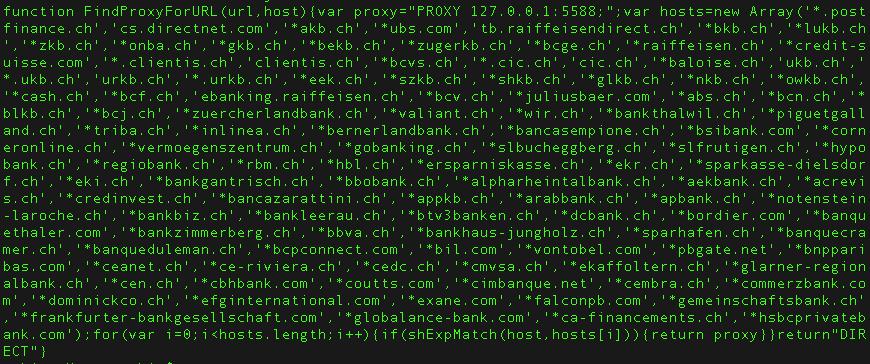
The malware would also install two proxies running on local host port 5555 and 5588, as well as a Tor utility through which it would redirect the intercepted traffic. However, it would first verify whether or not the users’ IPs corresponding to Switzerland, and would only intercept the traffic of those Swiss users.
After deobfuscating the malware’s code, Trend Micro discovered that a list of target domains of Swiss banks were hardcoded into it. When the victims would try to visit those banking websites, they would be redirected to an e-banking login web page that was hosted on a Tor hidden service. That means the location of the server is anonymous. The attacker would steal users’ banking credentials this way, and it would also fingerprint the user’s browser and system information.
WERDLOD And "Operation Emmental"
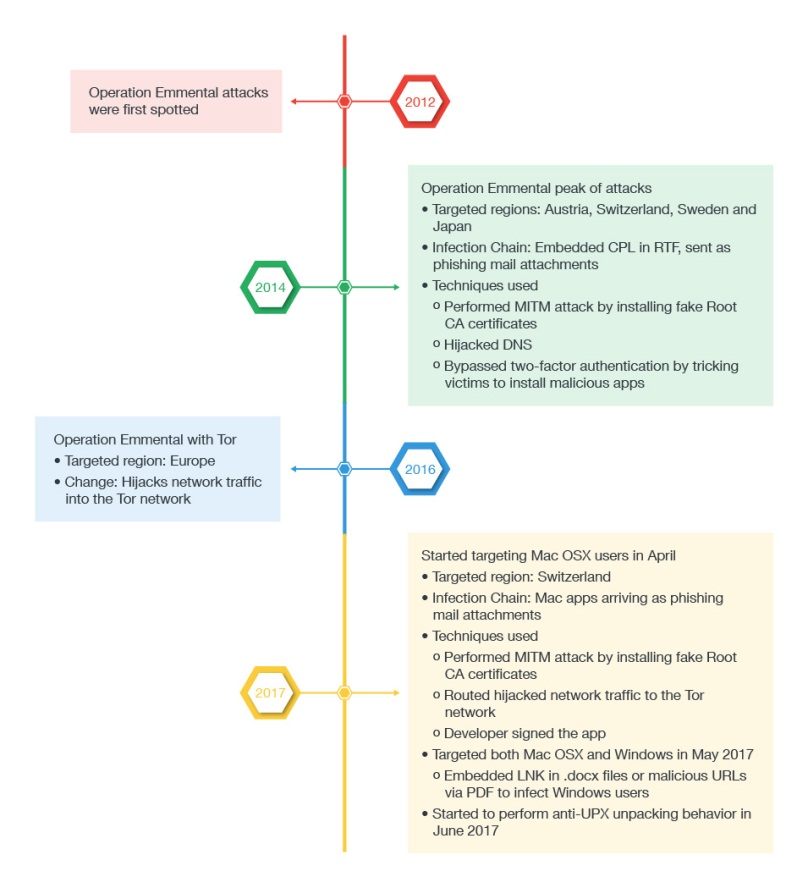
Trend Micro believes that OSX.DOK mode of operation is very similar to that of a Windows malware called WERDLOD, which has also targeted bank customers in Switzerland, Austria, Sweden, and Japan as part of “Operation Emmental.”
Operation Emmental would also intercept users’ SMS-based banking tokens by tricking users into installing a fake Android app. Then app would then capture the SMS tokens as they were automatically sent by the banks when the users tried to login to the online banking services. This type of attack was not observed with the OSX_DOK malware.
MacOS Can Be Malware Victims, Too
MacOS wasn't targeted all that much by malware makers until recently, largely because it didn’t have enough market share to justify the effort. However, as the Mac user base has continued to grow, attackers now see it as a more appealing target platform, especially if all they need to do is repurpose much of their Windows malware for macOS.
Trend Micro security researchers recommended users to refrain from downloading file attachments unless they trust the people that sent them.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
hellwig Fake, self-signed, unknown or untrusted certs should always raise a warning making it very clear you should be safe and not open/interact with the faulty cert unless you are absolutely certain you trust it.Reply
Yes, many people will continue anyway, but it doesn't sound like this warning was even raised with Safari.
I mean, if you can just fake the cert, what good is the cert system to begin with? -
firefoxx04 Reply19925977 said:Fake, self-signed, unknown or untrusted certs should always raise a warning making it very clear you should be safe and not open/interact with the faulty cert unless you are absolutely certain you trust it.
Yes, many people will continue anyway, but it doesn't sound like this warning was even raised with Safari.
I mean, if you can just fake the cert, what good is the cert system to begin with?
The cert is trusted because the malware installs its own Certificate authority onto the system. This will always work.
-
Jayson_15 "Trend Micro security researchers recommended users to refrain from downloading file attachments unless they trust the people that sent them." That isn't great advice. Most phising emails are spoofed to appear that they came from a contact or other trusted source.Reply