Old x86 Processor Design Flaw Vulnerability Disclosed At Black Hat: What You Need To Know

Computer security conferences such as Black Hat don't often reveal exciting news we didn't already know: Much of our technology is extremely vulnerable to a seemingly endless array of malicious attacks and exploits being discovered and created on a daily basis. The newest attacks and mitigation techniques are usually the hot ticket at these events. However, Christopher Domas, a security researcher with the Battelle Memorial Institute, revealed an exploit that points to a design flaw in the x86 architecture that has been around since 1997 and affects numerous processor architectures still in use today.
What Is It?
The vulnerability, called "The Memory Sinkhole," exploits the lowest, most privileged "rings" of execution in the x86 processor architecture by forcibly penetrating the System Management Mode (SMM) through a remapping of the Local Advanced Programmable Interrupt Controller (APIC) over the SMRAM range during critical execution states, causing memory accesses that should be sent to the MCH to be prematurely accepted by the APIC instead, permitting malicious ring 0 code influence over the SMM.
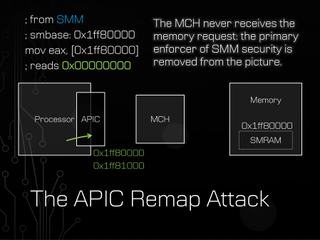
The level of firmware affected by successfully executed "sinkhole" attacks causes the vulnerability to persist through operating system and hardware reinstallations. This exploit can bypass Trusted Execution Technology and grant SMM execution privilege to more malicious code outside of the SMRAM, which can unlock hardware, disable cryptographic checks, install additional rootkits and even disable your system.
Engage Panic Mode
This news sent a wave of panic rippling across the Internet, as a slew of technical terminology like the previous paragraphs can scare the living daylights out of security-minded PC users who don't know exactly what it all means.
Several reports had inaccurately claimed that this vulnerability affects every x86 processor that Intel and AMD have released since 1997. If the headlines were any indication, this was the mother of all exploits, and no one was safe.
We took some time to read the full report by Domas in detail, and to find official statements from Intel and AMD concerning this vulnerability. The good news is that the "memory sinkhole" isn't as all-consuming as it sounds, despite its potentially destructive capabilities.
Simmer Down Now
The exploit was presented as a proof-of-concept demonstration, and in itself is a very complicated attack to pull off. "The course granularity of the APIC position, combined with the inability to effectively control the APIC data, makes the vulnerability extremely difficult, but not impossible, to apply in practice," stated the two-page report. Essentially, it is possible to get infected, but not very probable. The attack still requires administrator or root level permissions in order to inject, so properly hardened systems are even less likely to be affected. Furthermore, it doesn't seem to plague as many processor models as many believed.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Intel Responds
The vulnerability was validated using select Intel processor models. Intel was apparently made aware of the issue ahead of time and released a security report on its website prior to Domas's presentation at Black Hat, addressing the issue in an official capacity and discrediting some of the sensationalist reporting that pegged Intel's entire processor line as a source of unsecured system nightmares.
"An issue was disclosed to Intel which leverages architectural differences in processors prior to second generation Intel Core processors to gain access to System Management Mode (SMM)," stated the security briefing. "Intel is releasing mitigations for [the] privilege escalation issue."
These mitigations included several updates for server motherboards supporting the Westmere architecture, and Domas indicated in his presentation that Intel will continue patching Nehalem and Westmere architectures (and possibly older ones) in addition to working with board vendors and other OEMs to deliver patches to a wider array of products in the field.
This, of course, will take a considerable amount of time, not to mention the cooperation and willingness of OEMs to patch hardware that is mostly unsupported. It seems more likely that the majority of the vendors will opt out in favor of selling more new motherboards. The good news is that users with a Sandybridge processor or newer can rest easy, because Intel seems confident this vulnerability only affects its predecessors.
AMD Remains Tight-Lipped
AMD has no official statement on the matter, but according to Domas, it's still analyzing the threat's potential impact and mitigations in its product line. The vulnerability is inherent in x86 architectures, but if Intel's later product lines aren't affected, then the differences in AMD's architectures could also grant immunity to the malicious exploit.
However, without official word from the company, there is no telling which (if any) products from the Red Team are susceptible to the attack. We reached out to AMD for some clarification, and we will update this article pending further information. There is no greater fear than that of the unknown, so hopefully AMD will address this issue soon and have a plan to patch any affected products.
Time To Upgrade?
In the meantime, Intel users clinging to their aging and unsupported chipsets, and AMD users cowering in fear, are both now likely seriously considering a new system purchase. Intel's affected Nehalem and Westmere users should receive the promised patches in time, and it is somewhat comforting to know that AMD is at least apparently aware of and working on the potential problem, but those who can't take the anxiety of feeling insecure may want to check out our Z170 roundup and Skylake review for potential upgrades. You know, for safety's sake.
I'll Get You Next Time!
It should be noted that although the specific exploit demonstrated at Black Hat doesn't possess the long-reaching destructive force some made it out to have, Domas concluded we are "just beginning to scratch the surface" of these types of architectural exploit attacks, reminding me of Dr. Claw shaking his silver-handed fist at Inspector Gadget as he flew away stroking his cat, poised to strike another day, another way.
The concept of forcibly taking control of the lowest level of firmware in the x86 architecture has been proven at Black Hat, and it may only be a matter of time before these types of attacks become commonplace in the endless onslaught of vulnerabilities that seem to always promise that they will get us next time, Gadget. Next time.
Follow Derek Forrest @TheDerekForrest. Follow us @tomshardware, on Facebook and on Google+.
-
TechyInAZ Wow, very interesting. Thankfully it will hopefully be patched soon.Reply
However, the best security tip I can give that works the best is to have an offsite backup that is NOT connect to the internet... -
Wisecracker Nice drive-by slam of AMD (rolling eyes). Try doing some actual reporting next time, and avoid your obvious bias.Reply
The deterioration of THG continues ...
-
littleleo ReplyNice drive-by slam of AMD (rolling eyes). Try doing some actual reporting next time, and avoid your obvious bias.
The deterioration of THG continues ...
I'm sorry I missed the AMD dive-by perhaps you could spell it out for us non-conspiracy people. Was it the:
it is somewhat comforting to know that AMD is at least apparently aware of and working on the potential problem
or is it the?
hopefully AMD will address this issue soon and have a plan to patch any affected products
Yep your right what blatant slam of AMD how do these people sleep at night! -
palladin9479 This isn't nearly as big a deal. In order to do this exploit you already need root level privileges, which means you can already do all that bad stuff. At least Tom's isn't getting too sensational with it.Reply -
a1r Wonder when OEMs will start to be held legally liable for not patching or issuing workaround advice for their products when they've been notified of security problems, after a suitable time for addressing the problem and releasing said information. In my mind as a computer tech, that's long past over due.Reply -
BG-52 Read the article, read the article again, still a lot of it went over my head. From what I understand this newly discovered exploit only affects processors based on x86 technology, which I assumed everyone has evolved past.Reply
Most Popular




