'Chrysaor' Surveillance Malware Found On Android Devices By Lookout And Google
The NSO Group, an Israeli firm that sells malware and exploits to governments and law enforcement agencies, created a sophisticated piece of malware called "Pegasus" to compromise iOS devices. Lookout researchers have now discovered a version of Pegasus for Android, which they dubbed "Chrysaor," after the malware infected a few dozen targets. Google was made aware of the threat and has taken steps to protect Android users.
Pegasus Surveillance Malware
Lookout and Citizen Lab--an organization within the University of Toronto's Munk School of Global Affairs--discovered Pegasus in August 2016 after it tried to infect human rights activists and journalists. The malware used three zero-day exploits in iOS (dubbed Trident by the researchers) to serve as a "one-click jailbreaking tool" that could take over iPhones. All the attacker had to do was trick you into clicking a malicious link.
Once an iPhone was compromised, Pegasus could be used to steal target information from chat applications and social media accounts. The malware could also persist on the device even if the vulnerabilities it was exploiting were patched, and could be remotely updated to exploit new cracks in iOS' defenses.
Chrysaor
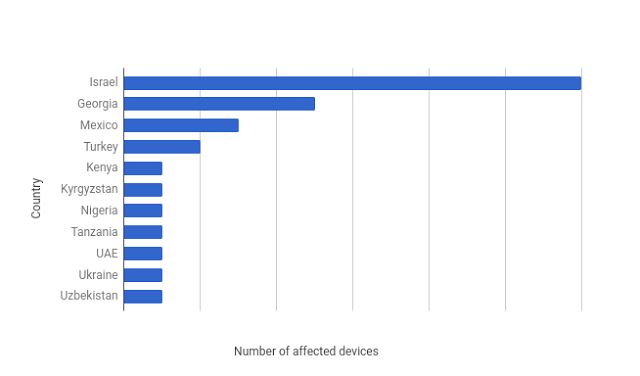
Chrysaor is a piece of Android malware closely related to Pegasus, according to Google security researchers. Google learned about it when Lookout submitted a list of suspicious packages to Google for analysis. That’s when Google discovered that a few dozen smartphones had malware on them that was similar to Pegasus. Google’s team said the packages were never in the Play Store, but that they could be downloaded from elsewhere.
The small number of infections may be surprising, but that’s probably because it was intentional. As a company specializing in creating exploit tools for governments, NSO’s solutions are likely tailored for the targets in question. Because national governments pay for those exploits, it also means that even if Chrysaor or some other piece of malware only infects one target, the company could still be paid handsomely for it.
NSO likely doesn’t want its malware to spread to as many devices as possible, either, as that would increase the chances of it being discovered and blocked.
How Chrysaor Works
Once Chrysaor is installed on a target’s device, a remote operator is able to track phone and SMS activities, as well as leverage the microphone and camera to spy on the target.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
In Android 4.3 or earlier, the Chrysaor exploit would use framaroot (an Android rooting tool) to escalate privileges and break out of Android’s application sandbox. If the target device is not vulnerable to these exploits, then the app attempts to elevate privileges with a superuser binary.
The malware uses six techniques to collect data:
- It repeats commands, such as requesting GPS location, at certain intervals
- It makes the /data/data directories where data from chat and social media application is usually stored world readable, so it can be easily collected
- It uses Android’s ContentObserver framework to observe changes in SMS, Calendar, Contacts, and chat applications
- It collects screenshots of what’s on the phone’s screen
- It does keylogging to record all inputs
- It silently answers a telephone call in the background, which makes it possible for the attacker to hear nearby conversations
Chrysaor can be removed via a remote command or it can be automatically deleted if it hasn’t contacted the attacker’s server in 60 days.
Protecting Against Android Malware
Android’s security situation could be much more dire than it actually is, considering how few devices receive updates on time. However, Google’s Verify Apps service usually does a good job against most of the malware out there that’s trying to exploit known vulnerabilities that haven’t been fixed in most Android devices. This is why it’s a good idea to keep Verify Apps enabled.
However, Verify Apps is typically effective only against malware that is known to Google. In Chrysaor's case, it wasn’t the Verify Apps service that alerted Google about the malware, but Lookout, which in turnlearned about it from Citizen Lab and a human rights activist. Google’s Verify Apps only entered the scene after the Pegasus malware was proven to be active, which meant Google could develop defense capabilities against it.
Those who may be targets of software developed by companies such as NSO Group may want to have a phone that receives security patches on time, because that's usually the best protection you can expect from a device. It’s also a good idea not to click on links from strange messages or download applications from places outside of the Play Store, as that exposes you to unnecessary risks.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.