Popular VPN extension for Google Chrome is a security nightmare, screenshots every page users visit and sends them to anonymous developer — FreeVPN.One flagged over enormous privacy concerns
Maybe uninstall FreeVPN.One
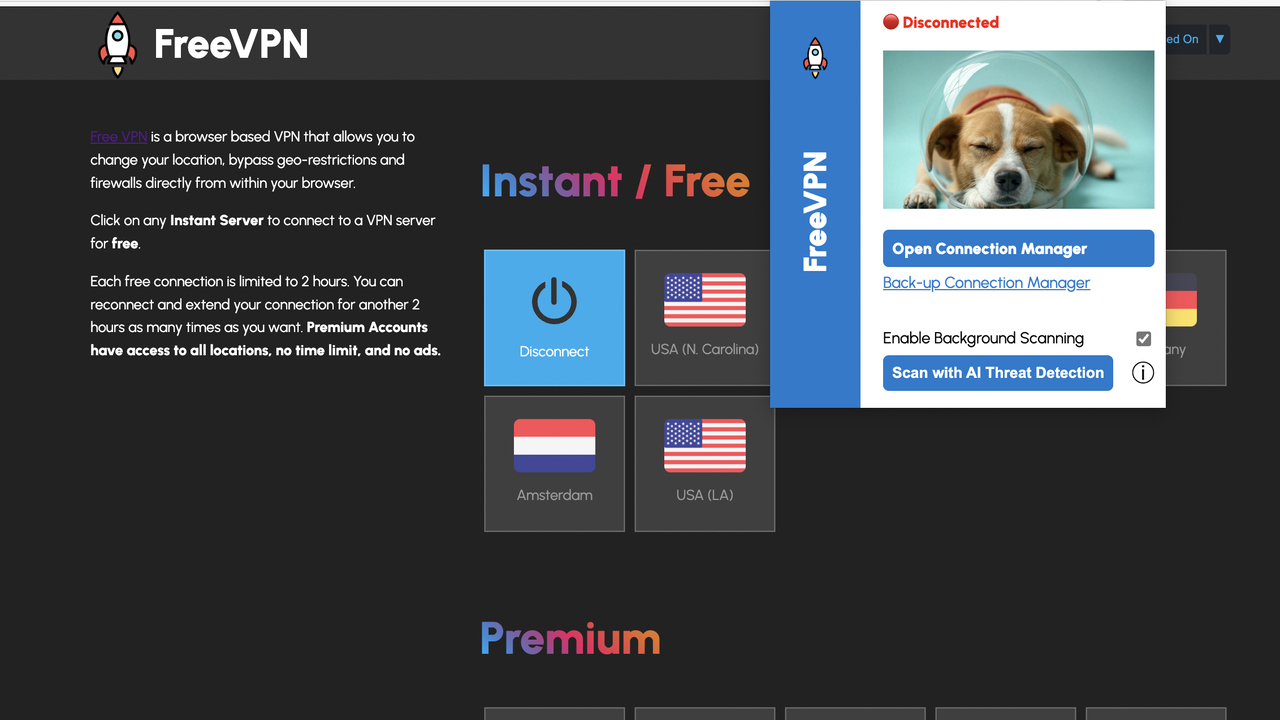
Koi Security has revealed that a popular Google Chrome extension with more than 100,000 installs has been taking screenshots of every website its users visit and sending them to a domain controlled by the software's anonymous developer.
The extension in question, FreeVPN.One, claims to be "the fastest free VPN for Chrome [sic]" and boasts a "Featured" badge that Google awards to extensions that "follow our technical best practices and meet a high standard of user experience and design." But it turns out FreeVPN.One has been undermining its users' privacy for months.
"While VPN extensions legitimately need permissions like proxy and storage for core functionality," Koi Security said, "this one asks for more permissions that enable broad data collection." The company identified a trio of permissions—tabs, and scripting—that allow FreeVPN to inject a script into every website its users visit. "Seconds after any page loads, a background trigger grabs a screenshot and sends it to aitd[.]one/brange.php, bundled with the page URL, tab ID, and a unique user identifier," the report explains. "No user action, no UI hint, the screenshots are taken in the background without you ever knowing."
FreeVPN.One's privacy policy does acknowledge that it can take screenshots of the pages its users visit, but it's only supposed to do so if users enable the so-called AI Threat Detection Feature, through which "a snapshot (screenshot) and related page information (such as the URL and visible page content) are transmitted from your browser to our secure servers and, if applicable, to our vetted analysis partners."
That suggests FreeVPN.One only enables its data collection features if users opt-in to the AI Threat Detection Feature... but the developer says in another paragraph that they "use anonymized usage data to build our threat intelligence database, whether or not AI Protection is enabled," which aligns with Koi Security's findings.
The policy has also changed recently. A copy of the policy from June 20 is missing the section about anonymized usage data, as well as the line "This system is in beta and provided 'as is' without warranties or guarantees of any kind, express or implied, including but not limited to accuracy, reliability, or fitness for a particular purpose."
It's also missing the header stating that FreeVPN.One is operated by a company called CMO Ltd. There's no mention of who operates the extension at all; in fact, the only clue comes via the email Google provides for contacting the developer. The domain associated with that email redirects to a page for Phoenix Software Solutions with the URL "https://domain146.wixsite.com/phoenixsoftsol." Not exactly confidence-inspiring.
Koi Security's report includes a breakdown of FreeVPN.One's slow transition from a seemingly innocuous VPN to a privacy-invading extension between April and July, as well as a summary of the company's interactions with the software's developer. (Who apparently stopped responding to the researchers' inquiries as soon as they asked for "evidence of legitimacy, such as a company profile, GitHub account, or LinkedIn page.")
VPN providers often make ludicrous claims about the privacy and security benefits of using their services. It's worth remembering that using those services requires a significant amount of trust in the organizations providing them; such trust would almost certainly be better placed somewhere other than in a free Chrome extension operated by an unknown developer that screenshots every page its users visit.
Follow Tom's Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
SonoraTechnical Crazy. Folks use VPN for perceived lack of traceability.... software captures everywhere they go... What a betrayal.Reply -
ezst036 Little tech doing this sort of thing is being normalized by big tech doing this sort of thing. The whole tech industry is going crazy.Reply
The Google model.
Which was duplicated and taken in different directions by Microsoft. One of the features that people despised the most about Recall was the screen capturing functionality. But guess what Microsoft crammed Recall into people's lives anyways.
FreeVPN, too, didn't begin its life as spyware. That was added in later as the report notes.
However, contrary to what the security report states:
In practice, we saw screenshots being captured on trusted services like Google Sheets and Google Photos, domains that cannot be considered suspicious.
Yes, Google Sheets and Google Photos are both suspicious. Though I suppose the report intended to say suspicious in the context of the VPN. But really anything Google is clearly sus.