
AMD has detailed its intentions to replace AGESA (AMD Generic Encapsulated Software Architecture) firmware at the 2023 OCP Regional Summit held recently in Prague. The plan is to transition from AGESA to openSIL (Open-Source Silicon Initialization Library) on AMD server and client processors by 2026.
If you're an AMD processor owner, AGESA is probably an acronym you hear about once every few months. Think of AGESA as a library of procedures to initialize the different aspects of your platform, such as the processor cores, chipset, or memory. That's why every time a new AMD chip launches or a new format of memory arrives, such as non-binary 24GB and 48GB DIMMs, AMD deploys a new AGESA firmware to usher in support for the new hardware. The firmware also helps solve bugs and other issues, like the recent Ryzen 7000 burnouts.
Firmware is essential in today's systems, putting a target on its back for cybercriminals. The downside is that platform users have limited access to inspect the firmware running on their system. It's why AMD has proposed opening the Silicon Initialization Firmware architecture, development, and validation to the open-source community. The chipmaker believes such a move is the correct direction toward more secure firmware and transparency. Firmware vendors, including 9elements and AMI, are already on board with AMD's openSIL initiative and demoed openSIL with coreboot and openSIL with UEFI (Unified Extensible Firmware Interface) at the event.
AMD has always supported the open-source community, whether software or drivers. AMD openSIL is an open-source solution that aims to be lightweight, simple, transparent but secure, and easy to scale, unlike AGESA. It isn't limited to AMD silicon, either. AMD openSIL is open to other silicon vendors, and the chipmaker has invited them to participate in the venture.
It's important to highlight that AMD openSIL doesn't replace UEFI. Instead, it integrates with other host firmware, including coreboot, oreboot, FortiBIOS, and Project µ. Furthermore, AMD programmed openSIL in standard industry language, and as a result, vendors can statically link it to the host firmware, bypassing any host firmware protocols. According to the presentation, openSIL is based on the Agnostic 3 Static Library, written in C17, the most recent version of the C programming language.
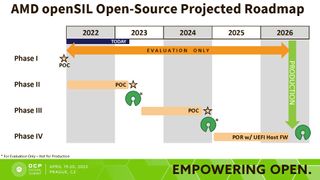
"Since OCP is primarily focused on servers, I'm not showing that roadmap for the client. So, if you remember, I talked about that it needs to be, you know, scaling to both servers and client. This does that as well. So we do plan to intercept all client and server platforms by 2026 timeframe," said Raj Kapoor, AMD Fellow and Chief Firmware Architect, during AMD's presentation at the 2023 OCP Regional Summit.
AMD openSIL is currently in the Proof-of-Concept (POC) phase and initially supports AMD's 4th-generation EPYC (Genoa) processors and accompanying platforms. The chipmaker will share the POC source code for EPYC Genoa soon. The forthcoming 5th-generation EPYC (Turin) chips will be POC as well. However, AMD will make openSIL a POR in 2026 for the 6th-generation EPYC lineup.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
"So the client will happen. Is that what your question is? You bet. 2026, all products. AGESA will be end of life. openSIL will replace it," responded Kapoor during the short Q&A session.
AMD admitted that openSIL still has a long road ahead but confirmed that openSIL is very close to parity with AGESA. However, AMD's last roadmap shows Zen 5 for 2024, and openSIL won't be ready until 2026. Coincidentally, AMD will support the AM5 socket until 2026. Therefore, we're looking at Zen 6 or even Zen 7 before seeing a finished product. Sadly, AMD didn't share a projected roadmap for openSIL on the client side. But one thing is certain. AMD will eventually replace AGESA on all its products with openSIL.

Zhiye Liu is a Freelance News Writer at Tom’s Hardware US. Although he loves everything that’s hardware, he has a soft spot for CPUs, GPUs, and RAM.
-
Alvar "Miles" Udell So basically when Socket AM5 and current server sockets are replaced by new ones. Think AMD just inadvertently confirmed Socket AM5's end of life.Reply -
Kamen Rider Blade I think this is the right direction for AMD to go down.Reply
Open-Source & Transparency FTW! -
Metal Messiah. It looks like AMD will use the "Agnostic 3 Static Library" solution written in standard C-17/18 programming language for the silicon, platform & utilities.Reply -
RedBear87 Reply
Sure, meanwhile the Platform Security Platform remains and will remain a blackbox and its exact functioning is known only to AMD and the US security bureaus, even though this approach doesn't make it inherently more secure.Kamen Rider Blade said:I think this is the right direction for AMD to go down.
Open-Source & Transparency FTW! -
Kamen Rider Blade Reply
Platform Security Platform?RedBear87 said:Sure, meanwhile the Platform Security Platform remains and will remain a blackbox and its exact functioning is known only to AMD and the US security bureaus, even though this approach doesn't make it inherently more secure.
Do you mean "Microsoft's Pluton Security Processor" that AMD implemented at the behest of Microsoft? -
Vanderlindemedia ReplyAlvar Miles Udell said:So basically when Socket AM5 and current server sockets are replaced by new ones. Think AMD just inadvertently confirmed Socket AM5's end of life.
Servers are something completely different then consumer versions.
Every socket has a expected life cycle. AM4 was longest. -
Amdlova If prioritary can make S. Think with open standards... Amd right now is ship of garbage looking only for money.Reply -
RedBear87 Reply
I meant AMD's own Platform Security Processor, which was used on every AMD's CPU/APU since Zen 1; but yeah, Pluton is an additional recent example of AMD's opacity and lack of interest in open source solutions.Kamen Rider Blade said:Platform Security Platform?
Do you mean "Microsoft's Pluton Security Processor" that AMD implemented at the behest of Microsoft? -
RichardtST As a security professional deep into the depths of it all for over 40 years, I can tell you unequivocally that Open Source is NEVER more secure and is always and invariably a bad idea. It will only add more complexity, more unreliability, and more 0days. Never give up control of important software to the Open Source crowd. That's where code goes to die.Reply -
Kamen Rider Blade Reply
So what is the optimum solution?RichardtST said:As a security professional deep into the depths of it all for over 40 years, I can tell you unequivocally that Open Source is NEVER more secure and is always and invariably a bad idea. It will only add more complexity, more unreliability, and more 0days. Never give up control of important software to the Open Source crowd. That's where code goes to die.
Closed Source Only?
Most Popular

