EFF, Lookout Discover Nation State Mobile Espionage On Global Scale
The EFF and mobile security company Lookout uncovered a global espionage campaign targeting primarily mobile users that downloaded fake secure messaging applications. The EFF and Lookout traced the “Dark Caracal” malware to a building belonging to the Lebanese General Security Directorate in Beirut.
EFF Director of Cybersecurity Eva Galperin said that:
People in the U.S., Canada, Germany, Lebanon, and France have been hit by Dark Caracal. Targets include military personnel, activists, journalists, and lawyers, and the types of stolen data range from call records and audio recordings to documents and photos. This is a very large, global campaign, focused on mobile devices. Mobile is the future of spying, because phones are full of so much data about a person’s day-to-day life.
Mike Murray, Vice President of Security Intelligence at Lookout, also noted that Dark Caracal is one of the first Advanced Persistent Threat (APT) campaigns they’ve uncovered for mobile, and also that nation-state actors seem to be making mobile the primary platform target for which they develop cyber espionage malware.
Dark Caracal’s targets are typical for threats presumably carried out by nation-states, including military personnel, enterprises, medical professionals, activists, journalists, lawyers, and educational institutions.
A Multi-Nation State Espionage Infrastructure
The joint collaboration between Lookout and the EFF started when the EFF released its “Operation Manul” report in 2016, in which the nonprofit discovered that dissidents being critical of President Nursultan Nazarbayev’s regime in Kazakhstan were being targeted by the campaign.
This report, along with further investigation, is how the researchers concluded that multiple nation-state actors were using the same cyber espionage infrastructure. Dark Caracal either uses or manages the same infrastructure used by a number of other cyber espionage campaigns.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
How Dark Caracal Works
EFF Staff Technologist Cooper Quintin also noted that one of the interesting things about Dark Caracal is that it doesn’t need sophisticated exploits to infect devices. Instead, all Dark Caracal needed was for users to give the infected apps the necessary permissions during installation.
Once the malware was loaded on a mobile device, it was able to steal SMS messages, including personal texts, two-factor authentication and one-time password codes, receipts and airline reservations, and company communications. It could also steal contact lists, call logs, names of installed applications, browsing history, names of Wi-Fi access points, login credentials for certain apps, documents, audio recordings, and photos.
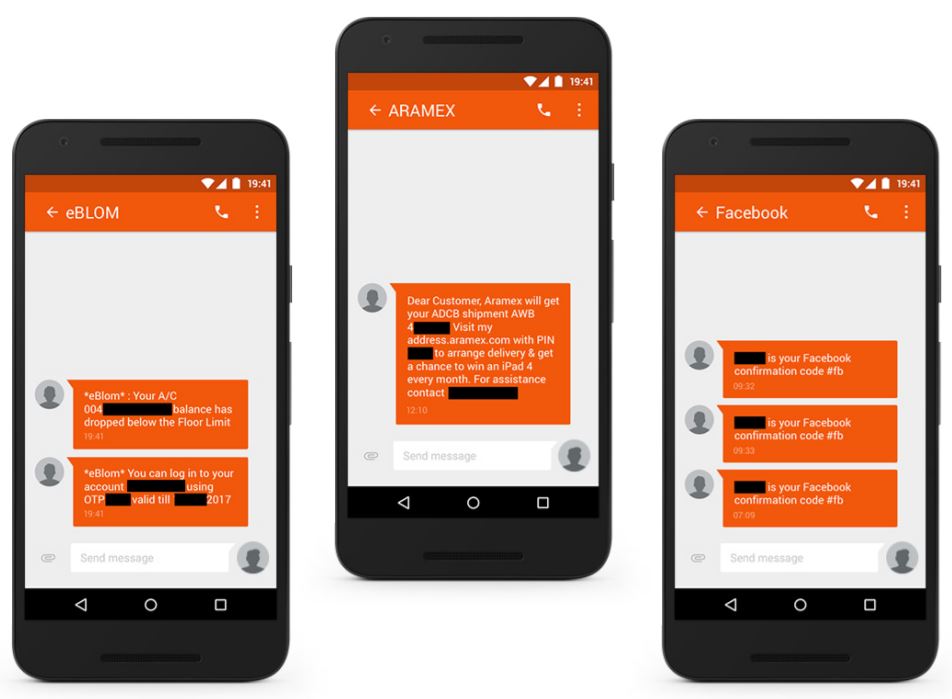
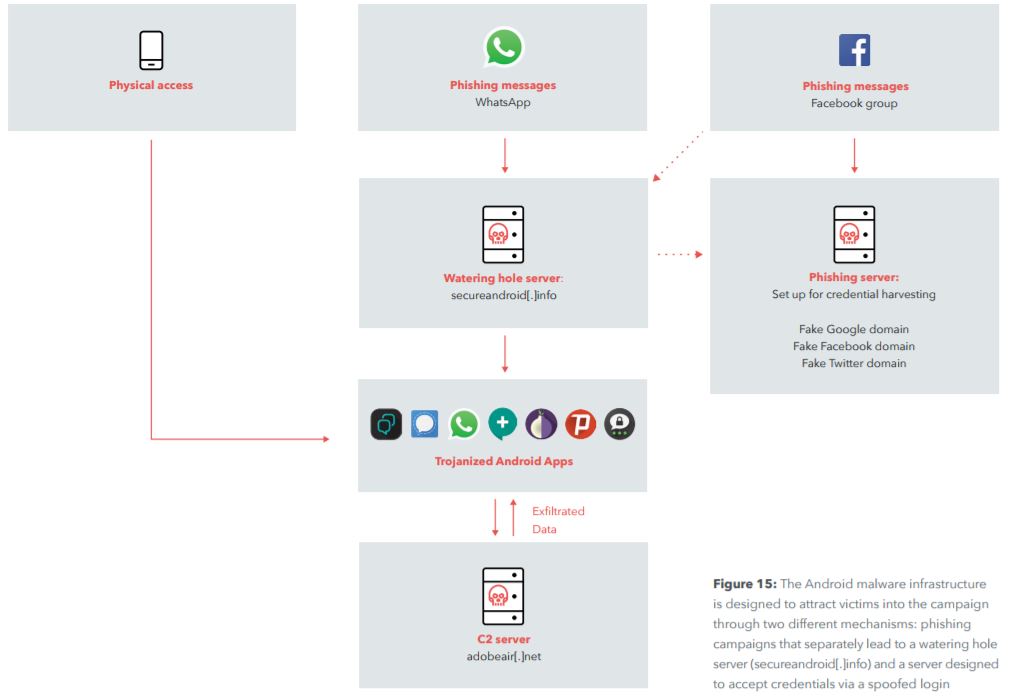
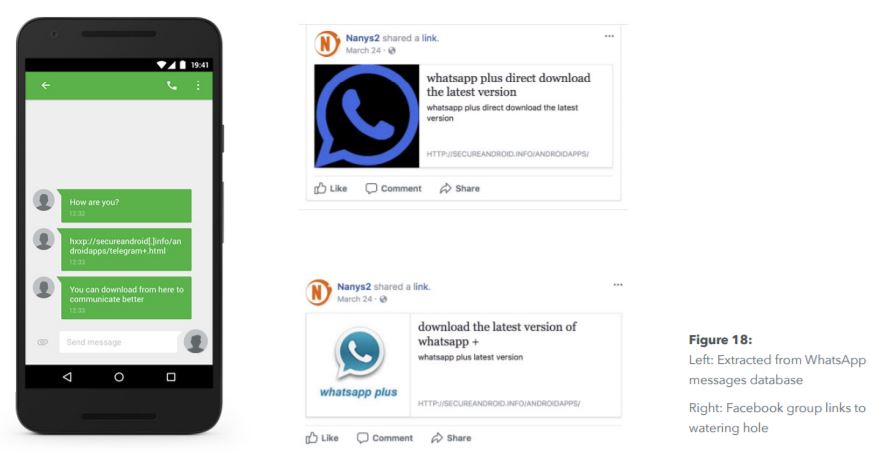
The group behind the Dark Caracal campaign would use WhatsApp and Facebook groups to send phishing messages to mobile users, then direct them to its own website (secureandroid[.]info) from which they encouraged users to download backdoored “secure” applications.
The infected apps would behave the same as the original counterparts, so it would be difficult for users to spot suspicious activity once the apps were installed and granted all the permissions they needed.
The phishing messages that would be posted on Facebook groups would also contain links to political stories that might entice the targets to click on them. Additionally, the researchers found that four Facebook profiles were “liking” the Facebook messages containing those phishing messages.
After working with Lookout and EFF researchers, Google also issued a statement on the matter:
Google has identified the apps associated with this actor, none of the apps were on the Google Play Store. Google Play Protect has been updated to protect user devices from these apps and is in the process of removing them from all affected devices.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.