Massive privacy concern: over 40,000 security cameras are streaming unsecured footage worldwide
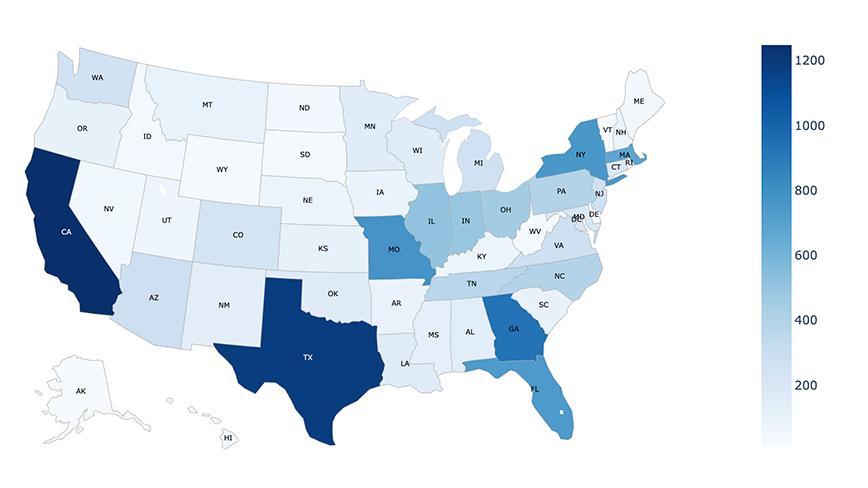
14,000 vulnerable feeds found in the U.S.

A major privacy concern involving more than 40,000 security cameras worldwide has been revealed by Cybersecurity firm Bitsight. According to the company's TRACE research division, these cameras are live-streaming video feeds that are fully exposed to the internet — meaning that one can gain access without needing any sort of authentication, encryption, or even a basic password. In most cases, a person can access real-time footage from these exposed cameras simply by knowing their IP address.
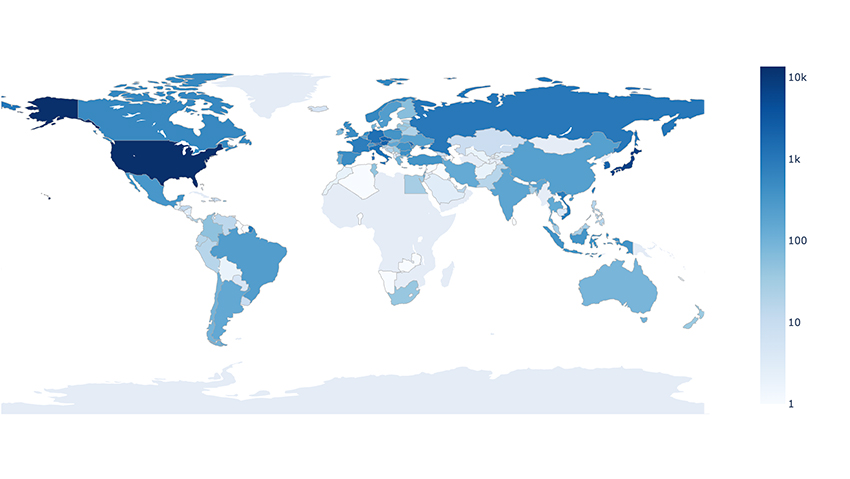
Bitsight initially flagged the issue back in 2023, but recent research suggests that the situation “hasn’t gotten any better.” According to the latest research, these vulnerable cameras are not limited to one region or industry. The United States has close to 14,000 cameras that are potentially exposed, with states like California, Texas, Georgia, and New York having the highest numbers. Next on the list is Japan, with 7,000 exposed cameras, followed by Austria, Czechia, and South Korea, each of which have close to 2,000 vulnerable devices.
It is true that not every camera hooked up to the internet is a cause for concern, and some livestreams are set up intentionally to showcase scenes, like a beach or a birdhouse, for public viewing. However, some of these vulnerable cameras have been found in more private environments — including residential setups monitoring front doors, backyards, and even living rooms.
Cameras in office spaces, factories, as well as public transportation systems were also found. Bitsight researchers were able to observe sensitive spaces, monitor foot traffic, and, in some cases, even see details written on whiteboards — all in real time. The majority of the exposed devices are said to be using HTTP, while the rest stream through RTSP (Real-Time Streaming Protocol), which is a common protocol for controlling and managing streaming media over IP networks.
In addition to raising privacy and surveillance concerns, these exposed devices pose serious security risks. Information collected by Bitsight’s Cyber Threat Intelligence team suggests that users are openly discussing the feeds on dark web forums, where users are sharing tools and techniques to gain unauthorized access, and even selling access, to unprotected video streams.
Users and organizations are advised to double-check on how their cameras are configured: Disable remote access if not in use, update to the latest firmware, and make sure the device is protected behind a firewall or connected to a secure network. A simple way to check whether your camera is exposed or not is by accessing it from outside your home network. If you are able to view the camera feed without logging into a secure app or using a VPN (Virtual Private Network), it’s likely open to anyone on the internet. Additionally, one should replace any default usernames and passwords as many camera devices ship with a default set of credentials that are easy to crack.
Follow Tom's Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Kunal Khullar is a contributing writer at Tom’s Hardware. He is a long time technology journalist and reviewer specializing in PC components and peripherals, and welcomes any and every question around building a PC.
-
TechieTwo It makes you wonder if the hardware suppliers/users are that security oblivious or if the intent is to make consumers vulnerable? This ain't rocket science for sure.Reply -
punkncat This isn't exactly unknown. Can't think of the site, perhaps even linked in the article but it basically shows all the cameras it can find still using the out of box security settings. At one point there was literally no telling what you would see. They did apparently put some filters in place a few years ago.Reply -
ezst036 40,000 is chicken scratch. That's not even barely a rounding error. Many of these cameras are out in public, pointed at open yard areas, streets, etc.Reply
The millions and billions who get spied on by Google through their personal Android device. That's a concern.
The millions and billions who get spied on by Microsoft through their personal computer. That's also a concern.
The number of 40,000, that is just a rounding error. -
Alvar "Miles" Udell I bet there are far more than that considering all the low price cameras from questionable companies like "DEKCO", "REOLINK", and "HISEEU", to name three on Amazon, just like for decades audio baby monitors transmit over unsecured radio frequencies and can be eavesdropped on.Reply
But yeah, I also bet that most of these 40,000 security cameras are local or government cameras set in places like highways, parks, and rivers that are intended for anyone to easily access over the internet and pose little risk unless the organization has zero brain cells and doesn't do things like change access passwords. -
Christopher_115 Reply
shodanpunkncat said:This isn't exactly unknown. Can't think of the site, perhaps even linked in the article but it basically shows all the cameras it can find still using the out of box security settings. At one point there was literally no telling what you would see. They did apparently put some filters in place a few years ago. -
das_stig Reply
When you make a statement like that about Google or Microsoft, proof is expected.ezst036 said:40,000 is chicken scratch. That's not even barely a rounding error. Many of these cameras are out in public, pointed at open yard areas, streets, etc.
The millions and billions who get spied on by Google through their personal Android device. That's a concern.
The millions and billions who get spied on by Microsoft through their personal computer. That's also a concern.
The number of 40,000, that is just a rounding error. -
heffeque Reply
Quick search:das_stig said:When you make a statement like that about Google or Microsoft, proof is expected.
Facebook: https://techreport.com/news/meta-yandex-android-spying-localhost-privacy-crisis/Google: https://dailysecurityreview.com/cyber-security/google-settles-5-billion-lawsuit/Microsoft: https://www.pcworld.com/article/2379675/ways-windows-11-collects-your-data-and-what-you-can-do-about-it.html
Do you want me to search for more examples? -
passivecool IOT risks are indeed not to be underestimated.Reply
40k cameras is indeed a tiny amount of the globally installed surveillance. To assume these are in public spaces and professionally administered seems far-fetched to me.
The referenced Bitsight article is so vague, that i cannot take it seriously. No proof, no offenders named. Or is it again mostly users who misconfigure the webcam watching the home pool?
Sure you can add a bunch of spying IOT devices to your home network. You can also cut off a few fingers with the table saw. There is only a certain extent to which we can be protected from our own stupid mistakes.
People everywhere make bad decisions with hardware that looks easy to use but is, actually, NOT.
Idiots who do not secure their corporate AWS buckets have i believe proven by far the bigger problem than a hand full of cameras. -
SomeoneElse23 Reply
Have you ever used AWS? There's nothing simple or straightforward about it. It's got better over the years, but it's still overly complex and certainly not user friendly.passivecool said:Idiots who do not secure their corporate AWS buckets have i believe proven by far the bigger problem than a hand full of cameras.