Google Cloud Previews Crypto Malware Threat Detection
Bye-bye, crypto miners
Google Cloud revealed a new Virtual Machine Threat Detection feature that can warn customers when cryptocurrency-mining malware is running on their VMs. That could help the increasingly-common occurrence of cloud-based systems hijacked to run cryptomining workloads, like the hack that racked up $45,000 in charges for one unlucky AWS user.
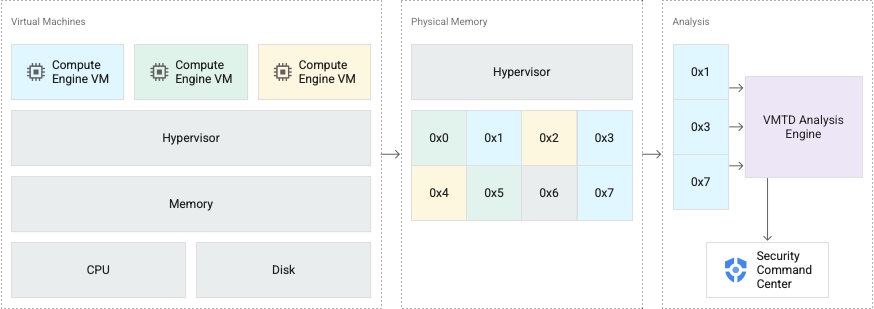
"VM Threat Detection is a managed service that scans enabled Compute Engine projects and VM instances to detect unwanted applications running inside VMs," Google said. "When you enable this service on a resource (an organization or project), scans are automatically configured and scheduled for that resource."
That suggests Google plans to defend against other malware via Virtual Machine Threat Detection in the future, but at least during this initial preview, the feature is limited to unwanted cryptocurrency miners, which Google said is "among the most common types of software installed in compromised cloud environments."
The problem isn't exclusive to Google Cloud. Trend Micro reported in November 2021 that Alibaba Cloud servers were being targeted by "cryptojacking" malware—and that it had detected similar attacks on other cloud service providers in the past. This kind of malware also targets everything from NAS products to M1 Macs.
Infecting a workstation with crypto-mining malware can lead to performance issues, additional strain on the system, and more energy usage. Infecting someone's cloud instance can lead to similar issues, of course, but the more pressing issue would probably be the increased operating costs incurred by the cryptojacking malware.
That's where Virtual Machine Threat Detection comes in. Google said that the feature would initially spot crypto-mining malware using three kinds of detections: matching hash values of currently running software against the hashes of known malware; matching against specific memory patterns associated with known malware; and so-called "combined detections" involving multiple signs of compromise.
The trick is offering these protections without creating additional problems for Google Cloud users. What's the point if the security offering can also disrupt services, use more power, or incur additional costs? (Beyond those associated with bumping up to the Security Command Center Premium subscription tier, that is.)
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
"Because VM Threat Detection operates from outside the guest VM instance, the service does not require guest agents or special configuration of the guest OS, and it is resistant to countermeasures used by sophisticated malware," Google said. "No CPU cycles are used inside the guest VM, and network connectivity isn't required. Security teams don't need to update signatures or manage the service."
Does that mean Virtual Machine Threat Detection will be foolproof? No. But it does seem that Google Cloud is trying to offer its customers a certain amount of additional security without requiring them to implement their own defenses against some of the more common—and more basic—attacks they might face.
More information about using Virtual Machine Threat Detection is available via Google Cloud's documentation.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.