BadRAM attack breaches AMD secure VMs using a Raspberry Pi Pico, DDR socket, and a 9V battery
AMD has now issued firmware updates for cloud providers.
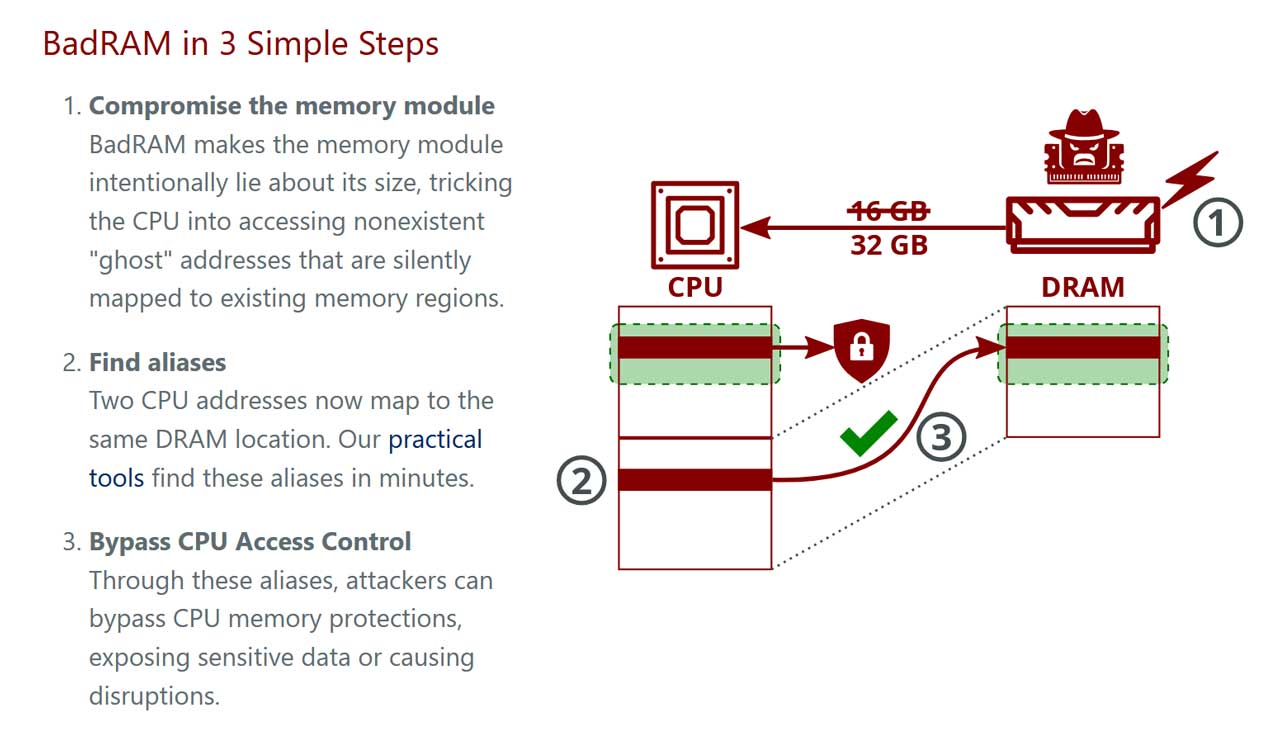
Researchers have described the BadRAM attack, which is claimed to facilitate the breaching of processor security “via rogue memory modules” (h/t The Register). Specifically, the research team has outlined a successful attack on AMD’s cutting-edge Secure Encrypted Virtualization (SEV) using a $5 Raspberry Pi Pico connected to a DDR socket and powered by a 9V battery. That’s just $10 of hardware required to “erode trust in the cloud.”
The name BadRAM provides a sizable hint at the angle of attack used by the team of researchers from KU Leuven in Belgium, the University of Lübeck in Germany, and the University of Birmingham in the UK. On the succinct yet informative website set up to spread awareness of BadRAM, the team highlights how ‘rogue memory’ is a security threat that has been largely ignored, at least by AMD.
For their BadRAM shenanigans, the team created “rogue memory modules that deliberately provide false information to the processor during startup,” and were then able to tinker with a system to bypass cloud server virtualization protections.
Earlier we mentioned AMD SEV, and this modern technology is designed to “protect privacy and trust in cloud computing by encrypting a virtual machine's (VM's) memory and isolating it from advanced attackers.” It even works when bad actors have access to critical infrastructure like the virtual machine manager or firmware. However, BadRAM bypasses SEV, including AMD’s latest SEV-SNP (Secure Nested Paging) tech using just $10 of hardware.
Leveraging the BadRAM attack, the researchers could go on to “completely compromise the AMD SEV ecosystem, faking remote attestation reports and inserting backdoors into any SEV-protected VM.” To do this they needed access to the SPD chip on server DIMMs, which they explained could be done by an insider in a cloud environment. Alternatively, software-based attacks could work, where the SPD chip wasn’t locked by the manufacturer.
To help explain the BadRAM attack and what it can do, the researchers have provided an infographic (above) and an example video (below).
Put your Raspberry Pi Pico, DDR socket and 9V battery away – AMD has issued a patch
AMD has now issued firmware updates to cloud providers so systems will securely validate memory modules and configurations during boot. BadRAM can't be bad on these updated systems.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
It should also be mentioned that the equivalent Trusted Execution Environments (TEEs) like Intel SGX and Arm CCA already have countermeasures against attacks like BadRAM in place, so no patching has been required to fortify their security.

Mark Tyson is a news editor at Tom's Hardware. He enjoys covering the full breadth of PC tech; from business and semiconductor design to products approaching the edge of reason.
-
abufrejoval I can't help thinking that none of this broad attention on security issues would have happend without Edward Snoden and his disclosures!Reply
Thanks Ed!
Wish you could come home! -
DS426 Incredibly difficult attack to pull off; when physical security fails, ALL security fails. One of the Ten Immutable Laws of Security. Nevertheless, great that AMD has already released an update to fix this by validating memory modules. After all, expectations are high on confidential computing platforms, rightly-so.Reply -
Notton so long as the patch doesn't cause performance issues, sure...Reply
but this level of direct physical attack is ridiculous. ludicrous even.
Like, what's next? a patch against a raspi5, soldering iron, and paper clips? -
Kamen Rider Blade Once "Physical Security" has been compromised with your machine, all bets are off.Reply -
NinoPino ReplyDS426 said:Incredibly difficult attack to pull off; when physical security fails, ALL security fails. One of the Ten Immutable Laws of Security. Nevertheless, great that AMD has already released an update to fix this by validating memory modules. After all, expectations are high on confidential computing platforms, rightly-so.
Notton said:so long as the patch doesn't cause performance issues, sure...
but this level of direct physical attack is ridiculous. ludicrous even.
Like, what's next? a patch against a raspi5, soldering iron, and paper clips?
Agree with all of you, but the memory encryption is specifically aimed to prevent also this type of attack. So is absolutely due, that AMD and all the security related actors takes this type of vulnerabilities with maximum priority.Kamen Rider Blade said:Once "Physical Security" has been compromised with your machine, all bets are off. -
Kamen Rider Blade Reply
Ergo, AMD releasing the security patches.NinoPino said:Agree with all of you, but the memory encryption is specifically aimed to prevent also this type of attack. So is absolutely due, that AMD and all the security related actors takes this type of vulnerabilities with maximum priorità. -
Findecanor State actors have been able to pull off physical security attacks by intercepting shipments and putting their own stuff in them. Or sometimes cooperated with the actual manufacturer.Reply
Just because an attack is unlikely is by itself no reason not to have safeguards against it.
Proper risk analysis takes into account both the attack's likelihood and amount of damage it could cause. -
hotaru251 Reply
this.DS426 said:Incredibly difficult attack to pull off; when physical security fails, ALL security fails.
If the criminal actor has access to the actual server you are pretty much boned anyways. -
artk2219 Reply
Thats what i was thinking of, if you have access to the shipment or are the "supplier", you can ship whatever you want, then your target will take care of installing or using it themselves. Israel's recent beeper, burner phone, and walkie-talkie, lets call them "special operations" comes to mind. There is no reason a near peer couldn't do the same, only instead of commo equipment with a loud report, its compromised computer hardware.Findecanor said:State actors have been able to pull off physical security attacks by intercepting shipments and putting their own stuff in them. Or sometimes cooperated with the actual manufacturer.
Just because an attack is unlikely is by itself no reason not to have safeguards against it.
Proper risk analysis takes into account both the attack's likelihood and amount of damage it could cause.