'Masque Attack' iOS Malware Is 'WireLurker' Enhanced, Can Steal Sensitive Information
It’s barely been a week since we learned about the WireLurker malware for iOS, and now we have new reports that an even more dangerous iOS malware called "Masque Attack" is in the wild.
"Masque Attack" works much like WireLurker in that it takes advantage of Apple’s enterprise provisioning to bypass other security checks on iOS. This proves that Apple’s banning of the infected WireLurker apps has been mostly ineffective, as expected, and until the company fixes this enterprise provisioning loophole, a whole new class of malware is going to invade iOS devices in the coming months or years.
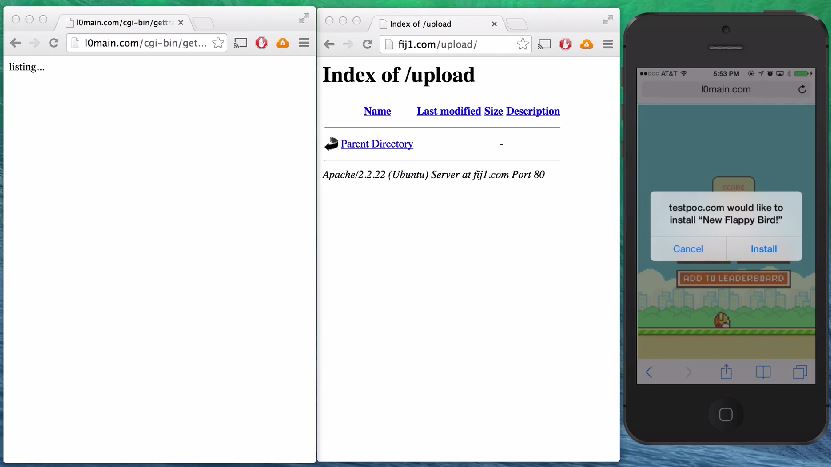
Unlike WireLurker, though, Masque Attack doesn’t even need to infect the user's PC and then have the user connect to the iOS devices through USB. Instead, it can just infect iPhones or iPads when the user visits a certain infected web page online; then, it prompts the user to install a new app. Once the user clicks to install it, the device is infected.
The new app can replace any application from the user’s device, other than the pre-installed Apple applications. That includes email, banking or any other type of third-party app. If the user introduces his or her login credentials in those apps, that information will be stolen by the malware’s creators. The apps will look identical to the ones they are replacing.
Although FireEye reported the malware to Apple months ago (July 26, to be exact), Apple doesn’t seem to have fixed the loophole yet, and even the latest iOS 8.1.1 beta is vulnerable to it. The researchers said that all iOS versions from iOS 7.0 to iOS 8.1.1 beta are vulnerable to this malware.
What they found surprising is that the infected apps could even get access to data from the original apps. Apple doesn’t seem to have any security measure that prevents other apps, even if similar, from accessing that data.
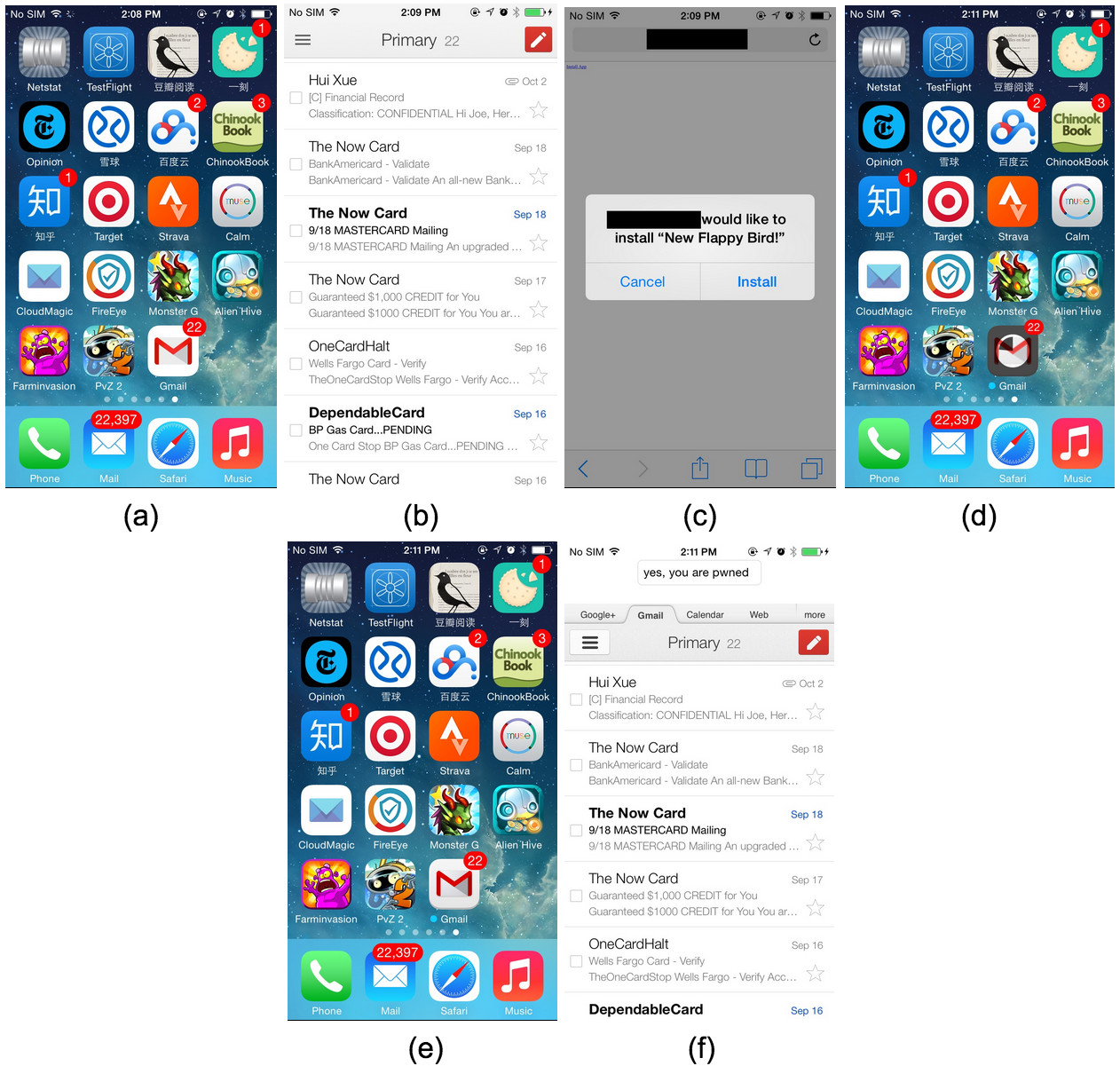
The FireEye researchers tested the malware themselves with a fake Gmail app that would prompt for a "New Flappy Bird" app, which would surely tempt quite a few users to press "install". No Flappy Bird app would be installed, but instead the Gmail app would be replaced by the fake and infected Gmail replica, which like the original has access to the user's emails.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to FireEye researchers, to protect yourself against this kind of malware, you need to:
Avoid installing apps that don’t come directly from Apple’s App StoreAvoid clicking “Install” or similar buttons from third-party web pagesUninstall apps for which you get an “Untrusted developer” iOS alert
Even if everyone reading these instructions will follow them religiously, there will still be many more people who don’t and then get infected with malware such as WireLurker or Masque Attack. Apple will need to either eliminate the enterprise provisioning from consumer iPhones and iPads or provide a much more secure interface for these enterprise feature so it becomes much more difficult for these infections to happen in the future.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Camel2021 I am guessing this is only a problem for Jailbroken phones. I am not aware of a way to install an app that is not on the Apple App Store without jail breaking the phone.Reply
It seems a little weird to blame Apple for users that are turning off a major security feature of the phone. -
David Moreau ReplyI am guessing this is only a problem for Jailbroken phones. I am not aware of a way to install an app that is not on the Apple App Store without jail breaking the phone.
No need to guess. You don't need to jailbreak:
It seems a little weird to blame Apple for users that are turning off a major security feature of the phone.
http://www.fireeye.com/blog/technical/cyber-exploits/2014/11/masque-attack-all-your-ios-apps-belong-to-us.html
You only have to allow installing from untrusted developer. This article links that to enterprise provisioning. It makes sense that enterprise users should be able to get updates without going through iTunes. You are not installing a new application according to the article. You are replacing an app with a fake version of that app. This is too subtle for many users to catch as most users are naive about security.
Before coming to the defense of a company, do the research. -
ptmmac There is no doubt that this is getting more and more dangerous for iOS. The only real defense here is having a user base that does not install apps directly from the web. It does not sound like it would be impossible for the makers of this malware to add a zero day flaw in iOS and make the installation silent so the user is unaware of the infection.Reply
The only risk to an iOS user at this point is if you are willing to install an app directly from the web. If you do use your phone this way then you are definitely vulnerable. This is a problem for that subset of iOS users who do this. I imagine the most likely people to fall for this are those that are new to iOS and unfamiliar with basic software safety. China seems to be the major place where this has propagated because of the willingness of customers to search for "free" software.
If stolen software or porn is what you are looking for then the likelihood that you will get infected by these types of malware is much greater. Otherwise you are not at much real risk.
The same would be true with a zero day upgrade to this malware. The real difference being how much more penetration the malware will make into the average user community on iOS. -
maddad Quote: You only have to allow installing from untrusted developer. This article links that to enterprise provisioning. It makes sense that enterprise users should be able to get updates without going through iTunes. You are not installing a new application according to the article. You are replacing an app with a fake version of that app. This is too subtle for many users to catch as most users are naive about security.Reply
Before coming to the defense of a company, do the research.
So you are saying if I bypass the Google Play store and add and Android App to my phone that is Googles' fault??? Use some common sense before you go blaming the company for the user doing something with the product that they have been warned not to do!!! -
SnakeV72 Avoid installing apps that don’t come directly from Apple’s App StoreReply
Avoid clicking “Install” or similar buttons from third-party web pages
Uninstall apps for which you get an “Untrusted developer” iOS alert
Sooo in other words, have common sense. Installing an app directly from a website is colossally stupid. You deserve to get infected if you do that.