Kaspersky Discovers Stealth Virus "Red October"
Security software firm Kaspersky has unveiled detailed about a stealth virus that has been deployed at least since May 2007 and served as espionage tool.
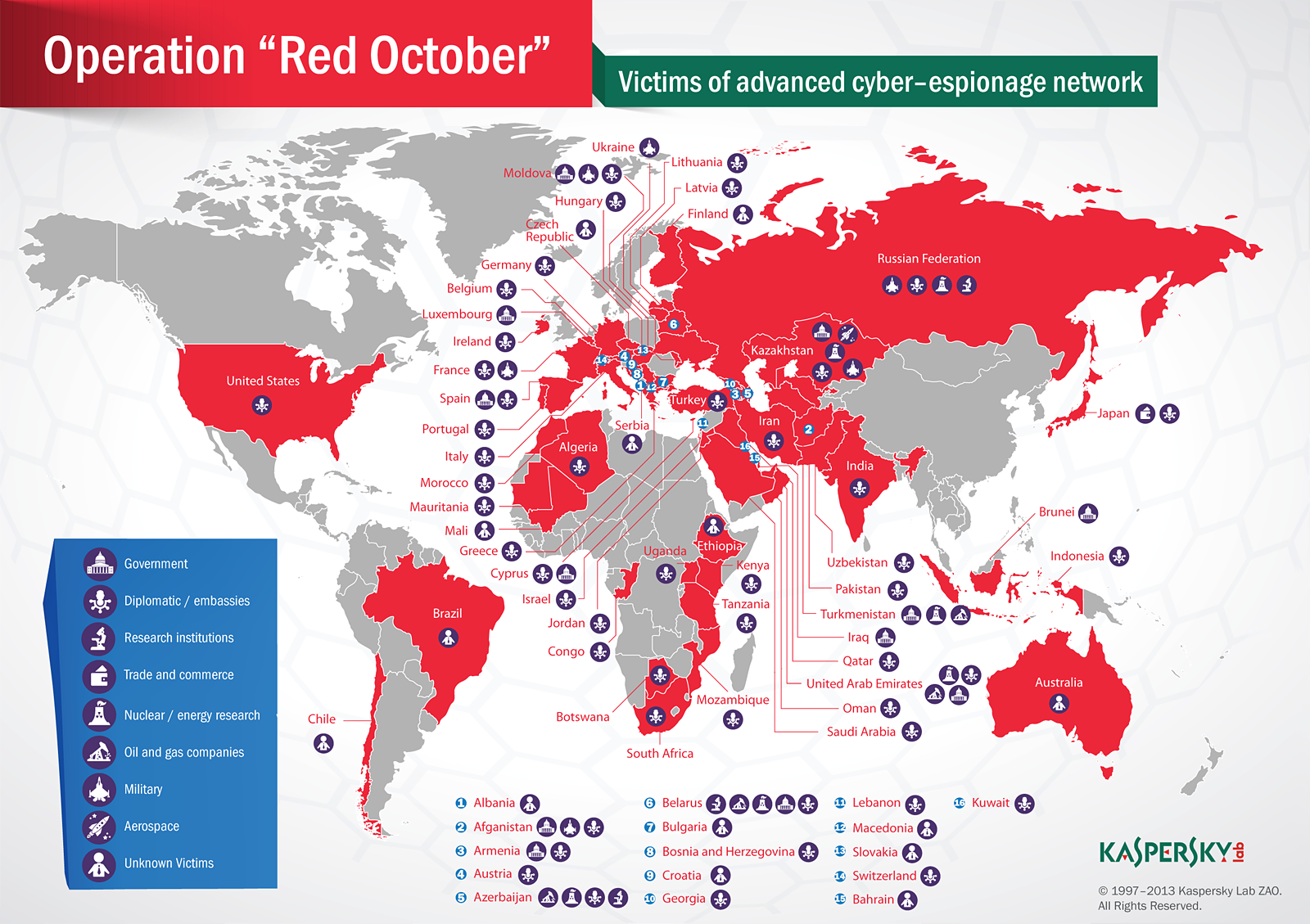
Called "Rocra", short for "Red October", which refers to the silent submarine at the center of Tom Clancy's 1984 novel "The Hunt for Red October", the malware is the front line of an espionage work that targeted government, research, nuclear energy, military, aerospace, oil and gas as well as trade and commerce institutions primarily in countries of the former Soviet Union, Eastern Europe, as well as Central Asia.
Kaspersky, which said that it has found first evidence of the existence of Red October, whose complexity and sophistication it compares with the Flame malware, identified more than "60 domain names and several server hosting locations in different countries (mainly Germany and Russia)" as a command and control infrastructure , which is set up as "a chain of servers working as proxies and hiding the location of the true -mothership- command and control server".
According to the security researchers, Red October not only attacks PCs, but also smartphones, including iPhone, Nokia-branded phones and Windows Mobile devices, and can dump Cisco enterprise network equipment configurations, hijack files from removable disk drives, including deleted files via its own data recovery capability, steal e-mail databases from local Outlook storage or a remote POP/IMAP server and pull files from local network FTP servers. It appears that the software is mainly based on the exploitation of three Microsoft vulnerabilities, CVE-2009-3129 (Excel), CVE-2010-3333 (Word) and CVE-2012-0158 (Word).
Kaspersky did not say how many computers may be infected by Red October, but mentioned that it found most systems in the area of Russia (35), followed by Kazakhstan (21), Azerbaijan (15), Belgium (15) and India (15). Six infected systems were found in the U.S. The company said that the exploits used by Red October have been developed most likely by Chinese hackers, while malware modules appear to have been created by Russian hackers.
Contact Us for News Tips, Corrections and Feedback
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Wolfgang Gruener is an experienced professional in digital strategy and content, specializing in web strategy, content architecture, user experience, and applying AI in content operations within the insurtech industry. His previous roles include Director, Digital Strategy and Content Experience at American Eagle, Managing Editor at TG Daily, and contributing to publications like Tom's Guide and Tom's Hardware.
-
Parsian So the Flame was so sophisticated must of required government agency funding, and if this is as sophisticated, why couldnt be a government agency product?Reply
either way, this stuff fascinating despite their destructive nature and intends. -
mavroxur The Greater GoodGive me a ping, Vasili. One ping only, please.Reply
Everyone knows that they read this in Sean Connery's voice. -
stingstang And my Chief of Staff just came in saying how important drones are to the future of warfare. Should have asked about this, though. Why is so much focus going in to drones when we still have such a huge vulnerability in the cyberspace sector?Reply -
groundrat Drones are ops. Ops is boots on the ground, and that is very important. We ARE doing the cyber thing, but unless you have the clearance and the need to know, you won't. Suffice it to say, if your only hearing about what the Chinese teams are doing, the US DOD is doing its job well.Reply -
DRosencraft stingstangAnd my Chief of Staff just came in saying how important drones are to the future of warfare. Should have asked about this, though. Why is so much focus going in to drones when we still have such a huge vulnerability in the cyberspace sector?Reply
Unfortunately any time a mention is even made about trying to drill down on crackers, it gets washed in with discussion on hackers, and you get a flare up from sectors of the free-internet crowd not unlike the flare up from sectors of the NRA crowd every time the words "gun control" are mentioned. -
TeraMedia Anyone notice that a lot of the infection focus was on diplomatic / embassy equipment or "unknown victims"? In the US, it was all dipl/embassy. In Brazil, Chile, and Australia, it was all "unknown victims". Whereas in Russia it hit military, research, and nuclear in addition to diplomatic.Reply
Either this is a KGB program looking for moles, or else this would seem to point to an origin in the Western world somewhere. -
jisamaniac mavroxurEveryone knows that they read this in Sean Connery's voice.Reply
I thought this was from the Princess Bride, so I read in the Giant's voice...