Hackers Use CAPTCHA to Launch Phishing Campaign
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Security company Cofense has discovered a new phishing campaign that has been using CAPTCHA boxes to hide a fake Microsoft login page from secure email gateways (SEGs).
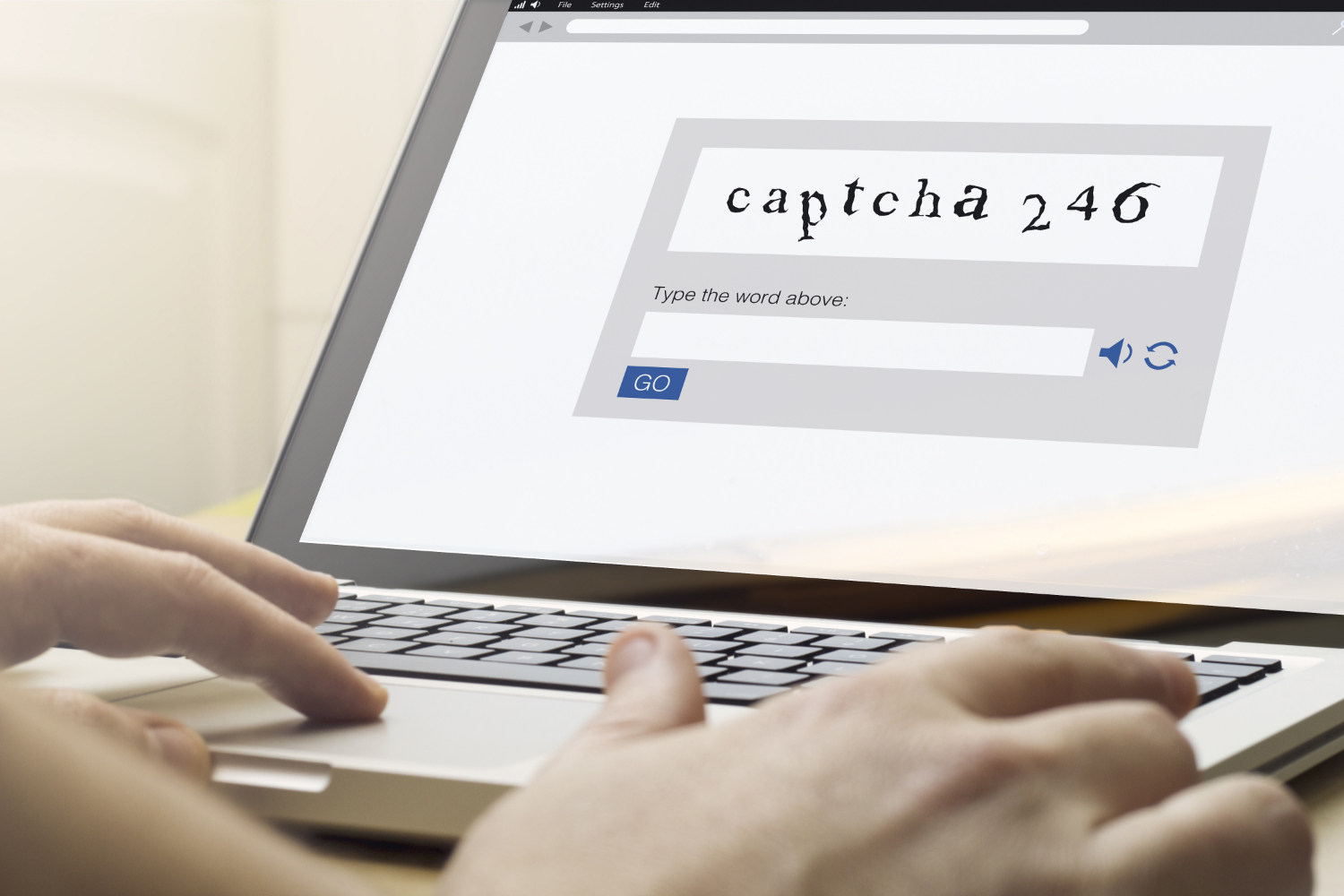
CAPTCHA systems create challenges, such as having to identify a blurred word or an object in an image, that you have to complete before you can go on to the next page. These systems are meant to block malicious automated bots from visiting a page by only allowing humans to bypass them.
However, the group behind this latest phishing campaign has turned the typical anti-bot usage of CAPTCHA on its head and is using CAPTCHA to stop malware scanners from checking if a web page was built to steal user credentials.
Many businesses use SEGs to scan incoming emails for malware or phishing attempts. However, SEGs are not sophisticated enough to pass CAPTCHA systems. As CAPTCHA systems weren’t typically used by malicious actors, the vendors of SEGs seem to have been caught off-guard in this case, as their malware scanner were unprepared to meet a CAPTCHA challenge.
"The SEG cannot proceed to and scan the malicious page, only the CAPTCHA code site. This webpage doesn’t contain any malicious items, thus leading the SEG to mark it as safe and allow the user through.," the Cofense researchers said.
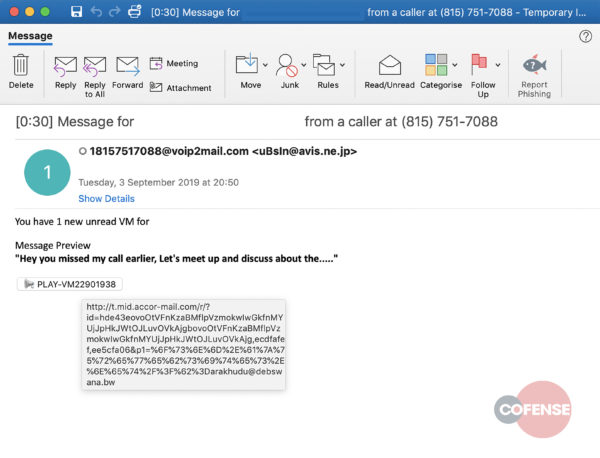
After the email receivers pass the CAPTCHA test, they are served with a fake Microsoft login page meant to capture their Microsoft account credentials.
The email delivering the malicious phishing link comes from a hijacked email account from avis.ne.jp and pretends to be a notification for a voicemail message. Ironically, both the CAPTCHA and the phishing page are hosted on Microsoft’s cloud servers.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
However, the attackers aren’t doing this just to spite Microsoft, but to make it more difficult for either humans or automated scanners to be able to tell that the page isn’t legitimate. SEGs typically look at the domain reputation of the links found in emails, so when the malware is hosted on Microsoft’s own public cloud servers, it passes the reputation test with flying colors.
Attackers are evolving their techniques and are continuing to integrate tools that would normally be used against them to deploy their own malware. Things such as cryptographic signatures, HTTPS encryption and now CAPTCHA systems are now increasingly used to bypass or prevent automated scanners from identifying malware. Even AI-powered anti-malware systems aren’t safe from this technique.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Hackers and hackers everywhere. I guess the web isn't a safe place/haven anymore. But I digress....Reply