PDF Problems: Digital Signatures Successfully Faked in Most PDF Readers
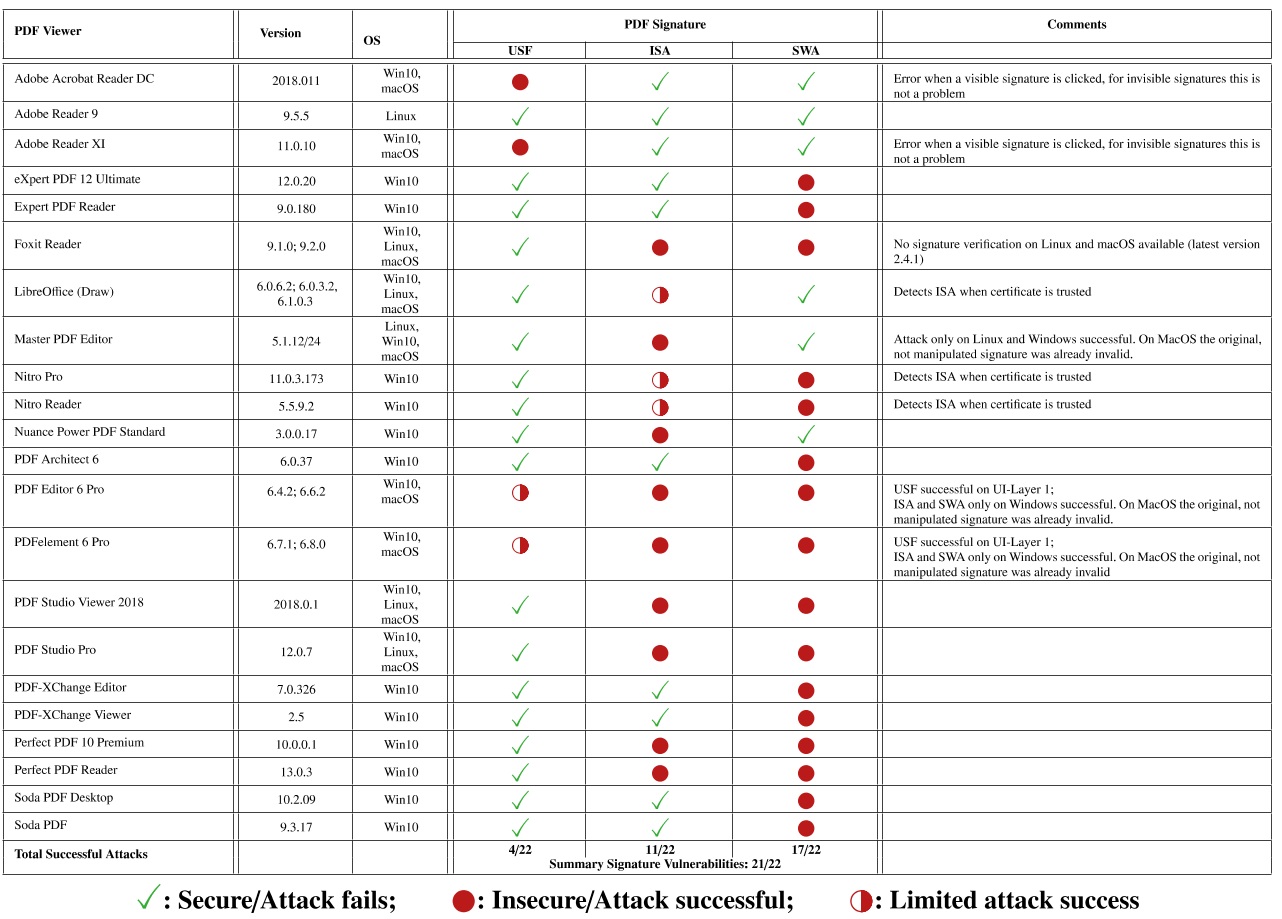
Researchers from the Ruhr-University Bochum in Germany were able to break the digital signatures on 21 out of 22 desktop reader PDF programs they’ve tested. Once the signatures were broken, the researchers were also able to spoof signatures in order to create fake documents. The researchers also found that six of the eight online validation services were also vulnerable.
One year ago, the German researchers started looking into how exactly PDF signatures worked, commencing their journey which led to the discovery of all the vulnerable PDF readers. The researchers have uncovered three class of vulnerabilities affecting the digital signature implementations on all of the tested PDF applications and have been working with Germany's Computer Emergency Response Team (BSI-CERT) to notify developers.
In many countries, including Germany and other members of the European Union, digitally signed documents are legally binding and can be admissible in court as evidence. Therefore, it’s of vital importance that those signatures can’t be spoofed to create fake documents.
Novel Attacks Against PDF Reader Signature Schemes
The German researchers found three types of vulnerabilities affecting the PDF applications.
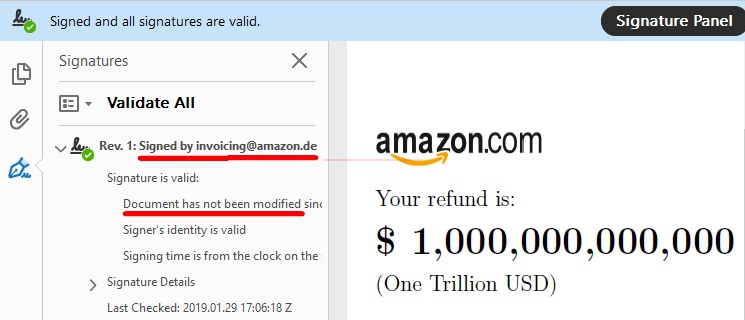
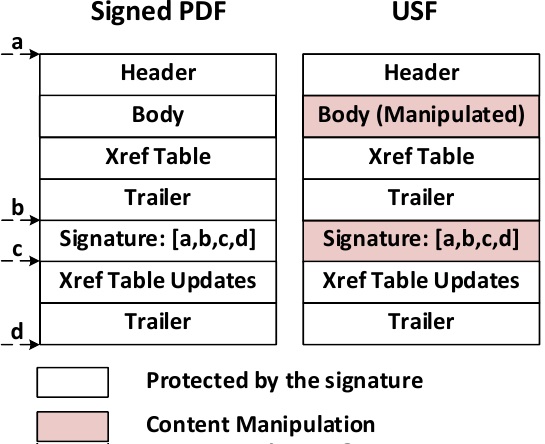
The first type, called a Universal Signature Forgery (USF), can show invalid signatures that don’t have all the required meta data for validation as valid despite that lack of information. The issue here is that PDF readers were supposed to show an error when information for the validation was lacking, but almost none did.
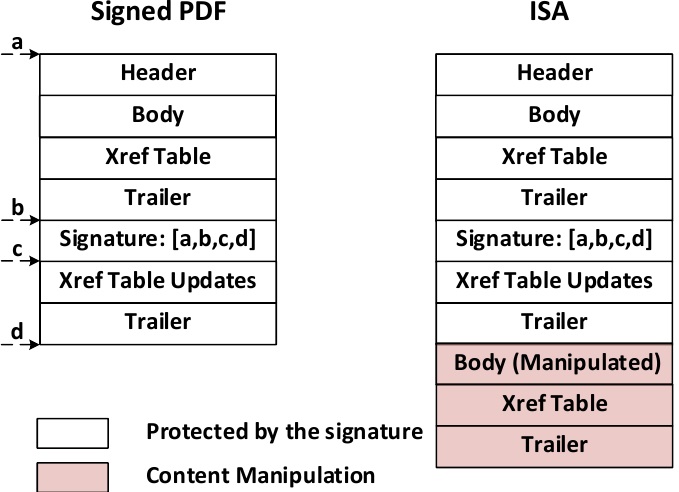
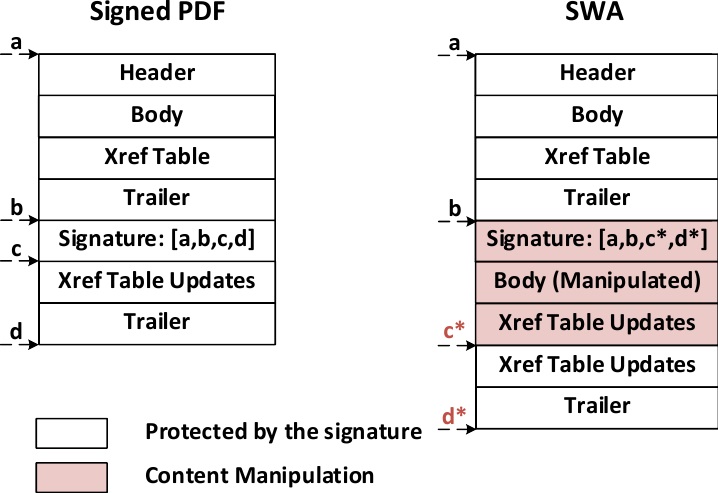
The second type of vulnerability is called an Incremental Saving Attack (ISA). The ISA abuses a feature of PDF files that allows for appending additional information to a document, such as annotations. However, an attacker could also change the document’s text body using the same feature. Therefore, the attacker could use a valid signature on a modified fake document this way.
The problem here is with both the PDF specification, which allows such extensive body modifications to be made to signed documents, as well as the signature validation scheme, which doesn’t indicate that the file has been altered after the signature was made.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The third class of vulnerability, called a Signature Wrapping Attack, allows the verification logic to process different data than the application logic. It’s the more complicated attack out of the three and allows an attacker to change the location of the original document text and insert new text in the original location, all while the document’s signature remains valid.
Update Your PDF Reader Now
The researchers had been working with all of the relevant PDF readers’ developer teams to ensure the applications become secured against these three types of attacks before they made the vulnerabilities public. The German researchers tested all of the apps once again for all major desktop platforms (Windows, macOS and Linux) and found them to be secure against the three types of attacks. If you have a PDF application installed on your computer, now would be a good time to update to the latest version.
The researchers said that they haven’t seen the three attacks performed in the wild, but organizations and people that depend on digitally signed documents should take this recommendation even more seriously, especially now that the vulnerabilities were made public.
Image credits: Vladislav Mladenov, Christian Mainka, Karsten Meyer zu Selhausen, Martin Grothe, Jörg Schwenk
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.