Attackers Spread Malware Via Fake Meltdown/Spectre Patches
The Meltdown/Spectre saga is not over yet, at least not until everyone has patched both their operating system as well as their BIOS firmware. However, we’re already starting to see attackers try to take advantage of this situation by publishing fake patches that contain malware.
Meltdown/Spectre Patch In Disguise
Phishing has become an increasingly lucrative tool for attackers lately. The attackers can get the victims to bypass operating system security protections on their behalf and install the malware on their machines. According to German authorities, some malicious hackers have been sending Germans emails titled “Critical vulnerability - important update,” or similar, in order to get the victims to install their malware.
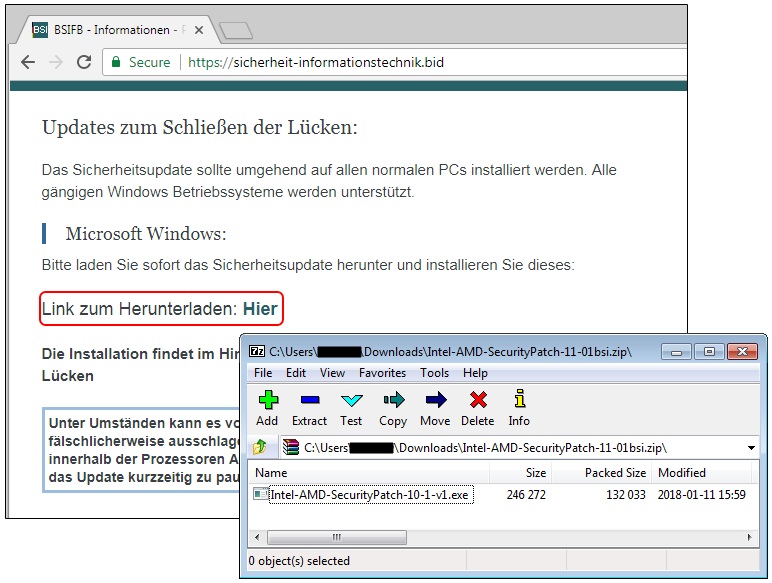
The email warns about the Meltdown and Spectre vulnerabilities and appears to come from the German Federal Office for Information Security (BSI). The email links to an SSL-enabled site that looks like BSI’s official site, where the victims can find a .zip file called Intel-AMD-SecurityPatch-11-01bsi.zip, containing a fake patch file called Intel-AMD-SecurityPatch-10-1-v1.exe.
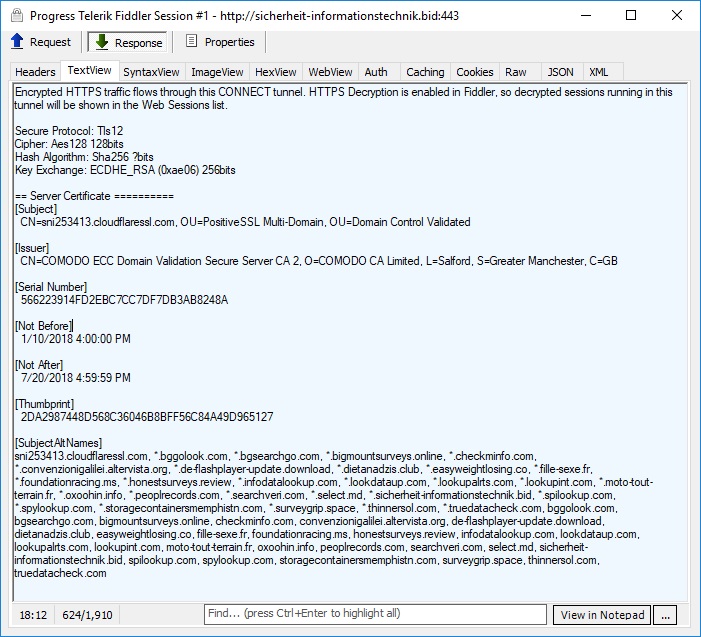
Upon running the .exe file, the victims will be infected with the “Smoke Loader” malware, which can then allow the attackers to deploy new malware code to the infected machines. Post-infection, the malware tries to connect to multiple domains via encrypted channels.
One of the malicious domains, which was also found to deliver fake Adobe Flash patches, was using a Cloudflare and Comodo-issued SSL certificate. Malwarebytes, which was the first to find the malware, contacted Cloudflare and Comodo about it and following Cloudflare’s swift actions, the site stopped responding within minutes.
Be Vigilant About Phishing Emails
As always, the best protection against phishing is to be vigilant and not download or install files either from complete strangers, or even from sources that may look familiar. Even if you receive such an email about an important vulnerability, it would be best to do your research about it, and then install the patch directly from official sources.
Not everyone has received BIOS updates yet, and until they do they are still vulnerable to Meltdown/Spectre. To check whether or not you’re still vulnerable, you can use one of these two tools. If you're still vulnerable, check with your motherboard or laptop manufacturer for an update.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
bernicesmith Good discussion here. I have also read about different malware which seriously generate the irritating scenario on PC.Reply