Chinese engineer accused of stealing Google's GPU and TPU secrets, transferring them to China-based startups
Former Googler arrested in California faces up to 10 years in prison and a $1 million fine.

Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
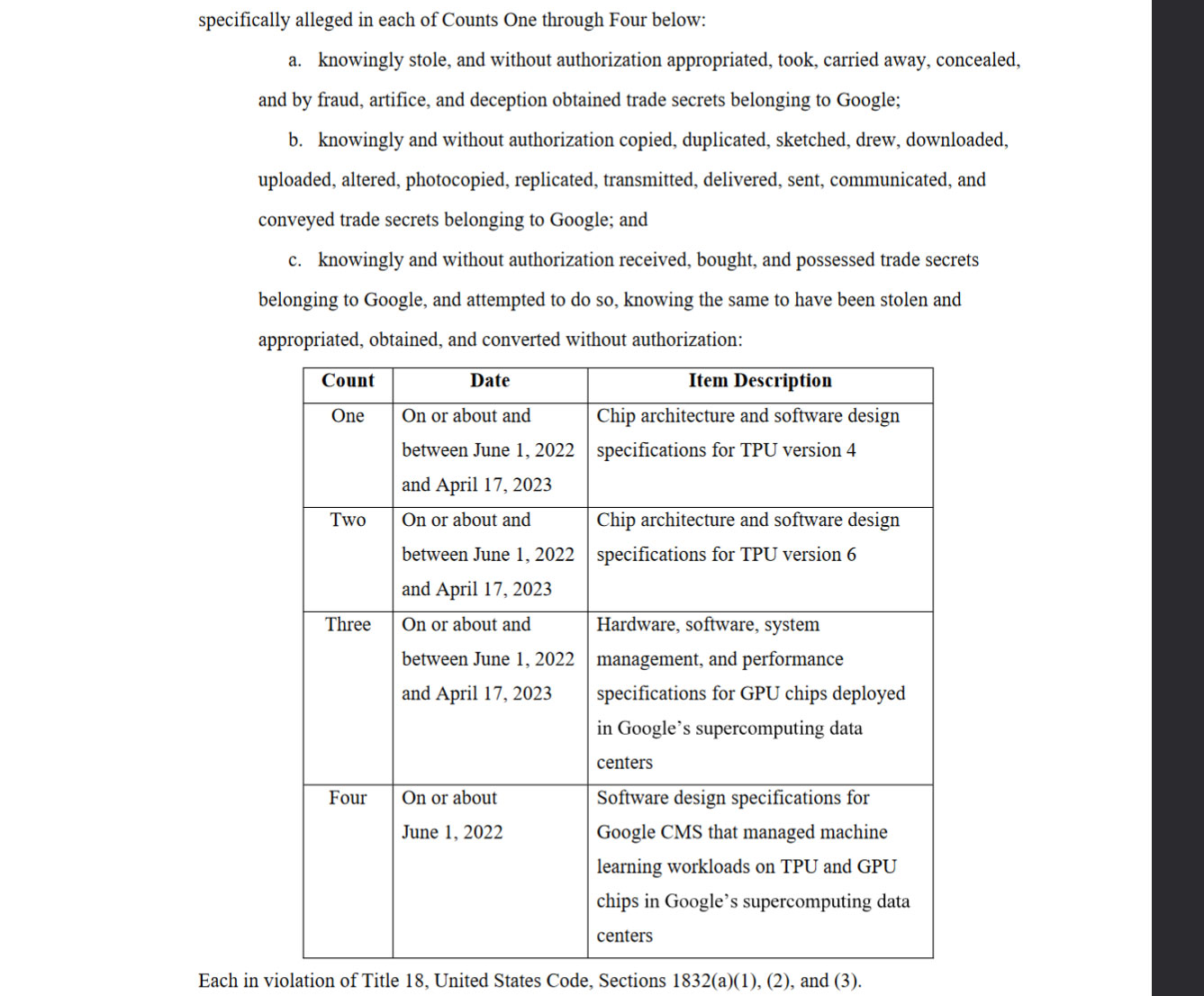
Former Google employee Linwei Ding has been arrested and charged with stealing Google's TPU and GPU secrets. The 38-year-old Chinese national was employed by Google as a software engineer from May 2019 until January 2024. However, in his brief spell at the U.S. tech giant, Ding is thought to have stolen more than 500 confidential files containing information about Google's AI technology. The indictment alleges four counts of trade secrets theft, covering areas such as TPU development, GPU deployments and specs, software design for machine learning, and more.
Stealing secret documents is bad enough, but during his employment at Google, investigations reveal that Ding also started working as the CTO of a Beijing AI startup called Rongshu. Moreover, he founded his own machine learning company in Shanghai in May 2023, becoming the CEO of Zhisuan. Working at these rival companies in overlapping technology areas seems to trample all over Ding's solemnly signed Google Employment Agreement and the firm's code of conduct. Last but not least, AI technology is protected on national security grounds.
Above you can see the four counts Ding is facing. Ahead of the tabulated section, the prosecution asserts that Ding knowingly and without authorization copied, stole, and passed on these trade secrets.
The filing at the federal California court provides a timeline of Ding's alleged data thefts, as well as some background information indicating how he was discovered. Apparently, the Chinese national began exfiltrating files in May 2022, sending them to a personal Google Cloud account. Google's protection policy enforcers would have noticed this earlier if it wasn't for Ding "copying data from the Google source files into the Apple Notes application on his Google-issued MacBook laptop," says the filing. "Ding then converted the Apple Notes into PDF files and uploaded them from the Google network into DING Account 1." Another personal account dubbed DING Account 2 was accessed while the ex-employee was on one of his China trips.
Google also seems to have records of Ding's correspondence with Rongshu, his travels with his Google laptop, and his other Chinese business ventures like Zhisuan. One of the most damning quotes that has been shared in the indictment is Ding's claim on behalf of Zhisuan "we have experience with Google's ten-thousand-card computational power platform; we just need to replicate and upgrade it and then further develop a computational power platform suited to China's national conditions."
When Google's internal investigators quizzed Ding in December 2023, he signed a legal document saying he had no non-public Google information in his possession. He never admitted to uploading more than 500 confidential files, or working for / founding Chinese companies.
Thankfully, the FBI sprang into action in January 2024, with a search warrant and permission to seize electronic devices and other evidence from Ding's US residence. FBI investigations confirmed that the personal cloud accounts contained over 500 confidential Google documents. These findings formed the basis of Counts One through Four of the indictment.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The theft of these Google trade secrets has much wider potential repercussions due to the national security implications of AI technology. Regular readers will be very aware of the U.S. government's keen eye on entities that could export leading-edge AI hardware and software to China. One of the most publicized tech restrictions involves powerful Nvidia GPUs, even including consumer-grade products like the GeForce RTX 4090.
"The Justice Department will not tolerate the theft of artificial intelligence and other advanced technologies that could put our national security at risk,” said Attorney General Garland in a press release on Wednesday. “In this case, we allege the defendant stole artificial intelligence-related trade secrets from Google while secretly working for two companies based in China. We will fiercely protect sensitive technologies developed in America from falling into the hands of those who should not have them.”
If convicted Ding could face up to 10 years in prison, and a fine of up to $250,000 for each count. We don't yet have a date for when the case will reach court.

Mark Tyson is a news editor at Tom's Hardware. He enjoys covering the full breadth of PC tech; from business and semiconductor design to products approaching the edge of reason.
-
peachpuff Maybe us firms need to do some more background checks on chinese people to circumvent ip theft when interviewing them.Reply
Born in america and never travelled to china... you're hired.
Lived in china most of their life and moved here... a bit sus, monitor everything they do or pass on them depending how valuable their work will be to china if stolen. -
sivaseemakurthi How do companies protect IP after the arrival of internet? Do they monitor employee laptops?Reply -
nightbird321 Reply
Per count, so 40 years maxevdjj3j said:10 years seems like a light sentence to me. -
Dadata What astonishes me every time is that china can easily afford to hire the chip architects and people to design chips specifically for their manufacturing nodes. Yet they resort to espionage and probably just get poor data every single time.Reply
It just reeks of stupidity.
All big companies have locks and security around their ip assets including spyware.sivaseemakurthi said:How do companies protect IP after the arrival of internet? Do they monitor employee laptops? -
bit_user Reply
I'm sure that would run afoul of anti-discrimination laws. Also, let's be clear about something: most of the people who would get caught in your net haven't and wouldn't do anything wrong. What's possibly worse is that it would surely miss many - it's not as if IP theft only involves China.peachpuff said:Maybe us firms need to do some more background checks on chinese people to circumvent ip theft when interviewing them.
Born in america and never travelled to china... you're hired.
Lived in china most of their life and moved here... a bit sus, monitor everything they do or pass on them depending how valuable their work will be to china if stolen.
I don't envy the big tech firms, as it's hard to see how they can completely avoid such incidents. If he had merely studied the documents and exfiltrated key details in his brain, they probably wouldn't have caught him. While you can limit what information an employee has access to, not enough to adequately protect a company's crown jewels, especially from the very employees who are working with them.