Telegram Zero-Day Let Attackers Install Backdoors, Mine Cryptocurrency
Kaspersky Lab uncovered attacks in the wild that were making use of a Telegram desktop application vulnerability to install backdoors or mine cryptocurrency without the users noticing.
Telegram Zero-Day Vulnerability
The Kaspersky researchers said that the flaw was based on the right-to-left override (RLO) Unicode method, which is primarily used by languages that are written from right to left, such as Arabic or Hebrew. The RLO method provides a way to change direction of written words through a special invisible character, which is what the Telegram hackers used to exploit the app.
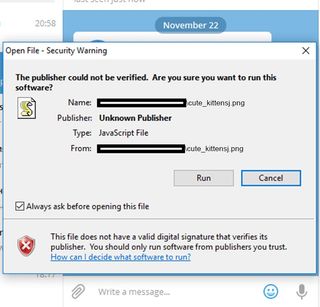
The attackers could have sent Telegram users a malicious script that was written something like this: “cute_kitten*U+202E*gnp.js.” The U+202E string there represents the Unicode character after which letters and punctuation marks are displayed from right to left. This means the user who receives the file would actually see the filename as “cute_kittensj.png,” even if the file wasn’t a .png image, but a JavaScript trojan.
Although the exploit sounds quite ingenious--and it is--this type of attack has been used in email attachments for the past decade, and it’s probably a type of vulnerability against which the Telegram developers should have defended in their app.
Installing The Backdoor
Users should have known better, too, considering Windows does warn them that the file on which they’ve just clicked is not an image but an unverified JavaScript file. However, many people tend to ignore most Windows prompts and click run anyway.
Not to raise any suspicion (beyond the Windows prompt, at least), the malicious script will show an actual image of a cute kitten, too, to put the victims’ mind at ease that they made the right call clicking through that warning message to see it.
The script comes with two types of payloads. The first one is a miner application that mines cryptocurrencies for the attackers, and the second is a backdoor which gives them remote access to the victims’ machines.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
One of the main rules for internet security is to be careful when downloading files from strangers online. Failing that, you should at least sandbox the application or use some other security solution that blocks malicious scripts from running on your machine.
Most Popular



