Large DDoS Amplification Attacks Now Possible Via Memcached Servers
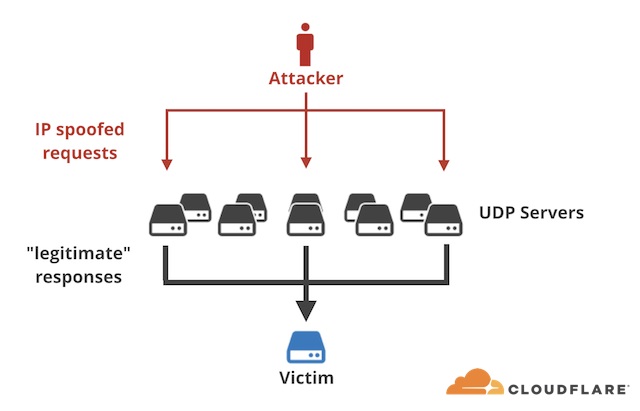
Security researchers from Cloudflare have started to see an increase in DDoS amplification attacks caused by attackers who exploit “memcached,” a distributed server caching system.
Memcached Amplification Attacks
The amplification technique essentially tricks servers into sending traffic to certain targets due to how their protocols usually work. These protocols often demand a response from the server when someone makes a request to the server. One of the protocols that works like this is memcached, which some attackers have started to abuse lately to launch DDoS attacks.
At peak, Cloudflare has seen DDoS attacks with a bandwidth of 260 Gb/s of inbound UDP memcached traffic. This attack is significant by amplification attack standards, according to Cloudflare. One of the reasons why the malicious actors were able to create such powerful attacks was that the packets sent by the memcached servers are quite large. The majority of the packets are 1,400 bytes in size.
The researchers noted that due to how the UDP protocol is used by memcached, this makes memcached one of the best protocols for amplification attacks. There are no checks done by the memcached system to see if the request to the server is legitimate. Therefore, the attackers are able to request large responses of up to 1MB per response.
How Memcached Attacks Are Launched
To make things worse, it doesn’t seem too difficult to set up a memcached amplification attack. The attackers first need to implant a malicious payload on a memcached server. Then, they spoof the “get” request so that the server sends the large responses to the target “source IP” (the target whose service the attackers are trying to disrupt).
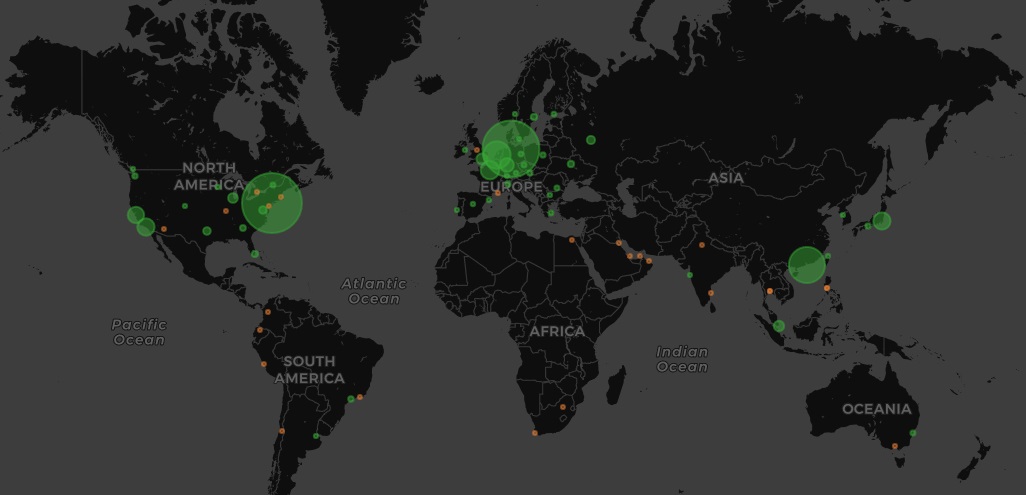
Cloudflare researchers saw memcached attacks that amplified 15 bytes of requests by 10,000 to 51,200 times. Most vulnerable memcached servers seem to be located in North America and Europe.
How To Stop Memcached Attacks
Cloudflare recommended memcached users to simply disable the UDP support, as it tends to be enabled by default. This should be the most effective way to stop this type of attack dead in its tracks.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Additionally, system administrators should also set-up firewalls that restrict the traffic flow of their memcached servers.
Ultimately, if we want to stop amplification attacks for good, Cloudflare believes we should fix vulnerable protocols and end IP-spoofing. As long as IP-spoofing is possible, amplification attacks on the internet through other protocols or vulnerabilities will continue.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
InvalidError Yup, the only way to stop amplification attacks is for ISPs and other edge providers to prevent their end-users from issuing packets with a source address that isn't their own.Reply