Bluetooth Technology 101
From keyboards to headsets to mobile computing, Bluetooth provides the personal wireless network needed to get around without a bunch of cables entangling our lives. Here's a close look at a key technology that empowers our mobile world.
Introduction

Bluetooth is everywhere—you'll find it in smartphones, tablets, laptops, TVs, cars, security systems, computer peripherals (mice, keyboads, headphones), smartwatches and more. A great many manufacturers in every sector of the tech industry have adopted Bluetooth for reliable and ubiquitous short-distance communication. But while most of us can decode the intricacies of a Wi-Fi connection by the standard's nomenclature, recognition of Bluetooth capabilities usually ends with the version number.
Bluetooth is fascinating, though—not just for its technical operation, but for the multi-national conglomerate of corporations standing behind it, and the work they do behind the scenes to makes sure Bluetooth is the standard. This article is an in-depth look at everything Bluetooth: the science, the tech, the security and the standard.
What Is Bluetooth?
In a nutshell, Bluetooth is a wireless communication specification operating on the unlicensed 2.4GHz band. It could be considered a short-range sibling of Wi-Fi. Where Wi-Fi enables wireless local area networks (WLANs) and ties together devices around some venue, Bluetooth enables wireless personal area networks (PANs) to enable communication in a 10-meter range (for Class 2 and Class 3 Bluetooth devices) and more than 100-meter range for Class 1 devices, mostly used for industrial applications. Even the low-power Class 2 and Class 3 devices are capable of greater than 10-meter range with the new networking and modulation schemes introduced by the Bluetooth standard in March 2016.
Wi-Fi, microwave ovens, drones and Bluetooth all operate on the 2.4GHz band. This frequency is categorized as "unlicensed" in most areas of the world. Unlicensed, however, does not mean unregulated—there are limits on the amount of power that can be transmitted, modulation schemes and unintentional out-of-band RF interference. Fortunately, operating a transmit/receive system does not require a user license. Otherwise we'd all have to take a radio operator course before enabling the Wi-Fi or Bluetooth functions on our smartphones, or even to turn on our microwave ovens.
Like all wireless communications technologies, Bluetooth requires a transmitter and receiver (with antennas on each), and modem-like control chips to modulate and demodulate the digital signal. These functions are usually integrated into one SoC that includes a transceiver, antenna and control chip. For more complex systems like smartphones, Bluetooth is often integrated into a multi-communication SoC that handles other wireless specifications as well.
Current implementations of Bluetooth come in two flavors: Bluetooth Basic Rate/Enhanced Data Rate (BR/EDR) and Bluetooth low energy (LE), also called Bluetooth Smart. The former establishes short-range connections for continuous data transfer (think headsets streaming music from a smartphone). Bluetooth LE is designed for short bursts of small data packets over a longer range in order to conserve battery life. Sensors, "smart" lightbulbs and other "smart home" devices are the ideal use-case for Bluetooth LE. Finally, some laptops and smartphones require both LE modes and BR/EDR modes, and this capability is offered by so-called "dual-mode" Bluetooth solutions.
MORE: Wireless Routers 101MORE: Router SoC 101
MORE: All Networking ContentMORE: Networking in the Forums
A Short History Of Bluetooth
In the tenth century, the Viking king Harald Blåtand (Harald Bluetooth in English) united large swathes of modern-day Norway and Denmark under his rule. Fast-forward to 1994, when Ericsson's R&D teams started investigating ways to connect computers and the "smartphones" of the day without cables. In 1997, Jim Kardach proposed the name "Bluetooth" for the new technology that would unify communications protocols like King Harald had united Scandinavia.

But Ericsson soon realized that implementing such a far-reaching, near-universal protocol would require cooperation on a vast scale. So, in 1998, along with Nokia, IBM, Intel and Toshiba, Ericsson founded the Bluetooth Special Interest Group (SIG). The first formalized Bluetooth technical specification arrived in 1999. The standard's logo is a ligature of two runes from the Younger Futhark runic alphabet: Hagall (ᚼ) and Bjarkan (ᛒ), Harald Bluetooth’s initials.
Bluetooth Special Interest Group
The Bluetooth specification was conceived as a worldwide communications specification. The founding members of the SIG, apart from being the multi-national companies with the most to gain from Bluetooth's adoption, also represented geographic regions: Ericsson and Nokia were from Europe, Toshiba hailed from Asia, and IBM and Intel represented North and South America.
The SIG's day-to-day tasks involve Bluetooth advocacy to governments, legal issues, managing test processes and compliance, and publishing the Bluetooth specification.
Microsoft, Motorola, Lucent Technologies and 3Com also jointed the SIG, and these nine companies formed the upper-level SIG administrators, the "SIG Promoters." The current list of promoters includes Apple, Ericsson, Intel, Lenovo, Microsoft, Nokia, and Toshiba.
"Associate Members" sign a legal document and pay an annual membership fee that allows them to participate in marketing and technical activities. They're also allowed to see draft documents 0.5 and above. With new Bluetooth specifications surfacing every few years, early drafts of the regulations provide Associate Members and the SIG Promoters an advantage in product design and deployment lead times. A third tier, called "Adopters," join for free, but still sign a legal memorandum of understanding. They have access to draft document versions 0.9 and above.
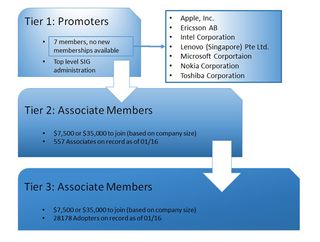
SIG membership is mandatory if a manufacturer wants to use the Bluetooth specification in products, or use the Bluetooth logo or other intellectual property.
IEEE, FCC, CE And Other Regulatory Acronyms
In the United States, the FCC allocates frequency bands for specific uses, the transmission power of devices in various configurations (narrowband vs. spectrum spread), modulation requirements and product certification for any product that has the potential for RF interference.
Most countries require some sort of licensing or approval of low-power devices operating on the 2.4GHz band, and also set limitations on power levels, modulation and other technical specifics of operation. Industry Canada (IC) handles this in Canada, there's CE for Europe and so on. And there are also country-specific requirements. For example, France sets geographical constraints, and Lithuania requires user licenses. Each regulation may also dictate the minimum and maximum number of channels Bluetooth can operate on.
The IEEE, a governing body that develops worldwide consensus standards on electronics, incorporated Bluetooth as standard 802.15.1. Wi-Fi is 802.11, in comparison.
Stay On the Cutting Edge: Get the Tom's Hardware Newsletter
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
-
Fernando_engen Bluetooth is pretty much the future. I have just started developing Bluetooth Low Energy Services/profiles for specific use cases along with the application layer. Its an awesome new world.Reply -
YunFuriku Actually hearing aids with button cell batteries these days can use Bluetooth Smart or to be exactReply
bastardized proprietary version of it by Apple and GN Resound which enables them to have wireless audio streaming from
various devices with Bluetooth. Comes with expense of range naturally because hearing aids need to use low power version of it (1,5V doesn't give much choice on this )
Max 10m in ideal conditions.
Sadly, the audio stack they use is Apple Exclusive so direct connection is Apple devices only.
Non-apple devices require intermediary devices such as TV streamer or Phone Clip to other Bluetooth Capable phones. These devices are relatively cheap compared
to old FM tech hearing aids used to use where transmitter prices were measured in 0,5-2k range, about ~$200-300 at most.
Unfortunate side is that if you want to use it with non-Apple phones you'll have to have intermediary device which serves as bluetooth handsfree mic/answer/volume
buttons too beause of the audio stack which Apple won't license to others.
At the same time Apple is pushing their made for iPhone hearing aid tech to FCC to be recognised as standard.
Here's to hoping hardcore android fan like me won't have to buy iPhone as my next phone if this doesn't come to other phones directly because of silly audio stack :P
-
RIluske Is the graphic about memberships correct? I thought the article said the third tier was free to join, but the graphic has it costing the same amount as second tier.Reply -
zodiacfml I feel WiGig has a better future eventually. Bluetooth will be left to activation or turning on devices or IoT as already mentioned in the article.Reply -
DotNetMaster777 Very useful article !! bluesniping can be done over one km away wow !?!?Reply
Are there any performance tests between wifi and bluetooth ?? -
exnemesis Just give me bluetooth tech that can allow me to walk away 40-50m from my phone and penetrate better through walls and objects and still retain the quality of whatever it is I'm listening to on my phone.Reply -
TripleHeinz This is the best article I've ever read in Tom's. Didn't have a clue that bluetooth was related with Thor the god of thundervolt ;)Reply -
yasminpriya15 Welcome to Bluetooth 101. Here are the top things you need to know about Bluetooth technology.Reply
My Bluetooth doesn’t work. What do I do?
The Bluetooth SIG does not make, manufacture or build any Bluetooth products. We simply support our membership and help them to help make the best products on the market. The best way to solve your problem is to contact the manufacturer directly or start by researching solutions on the Internet.
What is Bluetooth?
Bluetooth is a global wireless communication standard that connects devices together over a certain distance. Think headset and phone, speaker and PC, basketball to smartphone and more. It is built into billions of products on the market today and connects the Internet of Things (IoT). If you haven’t heard of the IoT, go here.
How does Bluetooth work?
A Bluetooth device uses radio waves instead of wires or cables to connect to a phone or computer. A Bluetooth product, like a headset or watch, contains a tiny computer chip with a Bluetooth radio and software that makes it easy to connect. When two Bluetooth devices want to talk to each other, they need to pair. Communication between Bluetooth devices happens over short-range, ad hoc networks known as piconets. A piconet is a network of devices connected using Bluetooth technology. The network ranges from two to eight connected devices. When a network is established, one device takes the role of the master while all the other devices act as slaves. Piconets are established dynamically and automatically as Bluetooth devices enter and leave radio proximity. If you want a more technical explanation, you can read the core specification or visit the Wikipedia page for a deeper technical dive.
Are there different kinds of Bluetooth?
There are actually several “kinds”—different versions of the core specification—of Bluetooth. The most common today are Bluetooth BR/EDR (basic rate/enhanced data rate) and Bluetooth with low energy functionality. You will generally find BR/EDR in things like speakers and headsets while you will see Bluetooth Smart in the newest products on the market like fitness bands, beacons—small transmitters that send data over Bluletooth—and smart home devices.
What can Bluetooth do?
Bluetooth can wirelessly connect devices together. It can connect your headset to your phone, car or computer. It can connect your phone or computer to your speakers. Best of all? It can connect your lights, door locks, TV, shoes, basketballs, water bottles, toys—almost anything you can think of—to an app on your phone. Bluetooth takes it even further with connecting beacons to shoppers or travelers in airports or even attendees at sporting events. The future of Bluetooth is limited only to a developer’s imagination.
What makes Bluetooth better than other technologies?
The short answer is because Bluetooth is everywhere, it operates on low power, it is easy to use and it doesn’t cost a lot to use. Let’s explore these a bit more.
Bluetooth is everywhere—you will find Bluetooth built into nearly every phone, laptop, desktop and tablet. This makes it so convenient to connect a keyboard, mouse, speakers or fitness band to your phone or computer.
Bluetooth is low power—with the advent of Bluetooth Smart (BLE or Bluetooth low energy), developers were able to create smaller sensors that run off tiny coin-cell batteries for months, and in some cases, years. This is setting the stage for Bluetooth as a key component in the Internet of Things.
Bluetooth is easy to use—for consumers, it really can’t get any easier. You go to settings, turn on your Bluetooth, hit the pairing button and wait for it start communicating. That’s it. From a development standpoint, creating a Bluetooth product starts with the core specification and then you layer profiles and services onto it. There are several tools that the SIG has to help developers.
Bluetooth is low cost—you can add Bluetooth for a minimal cost. You will need to buy a module/system on chip (SoC)/etc. and pay an administrative fee to use the brand and license the technology. The administrative fee varies on the size of the company and there are programs to help startups. http://www.traininginsholinganallur.in/qtp-training-in-chennai.html
http://www.traininginsholinganallur.in/primavera-training-in-chennai.html
http://www.traininginsholinganallur.in/big-data-analytics-training-in-chennai.html
