PIN-Locking Android Ransomware Comes To The U.S.
Android ransomware, first created and discovered last year by the ESET security team, took another step in its evolution by completely locking up users' devices with a PIN number. The new ransomware is called Android/Lockerpin.A and was also discovered by ESET.
Previously, such Android-based ransomware could only constantly bring up the ransom window in an infinite loop, as to appear that the device is locked, but users could eventually bypass it with the the ADB debugging tools or by restarting the device in safe mode and uninstalling the malware.
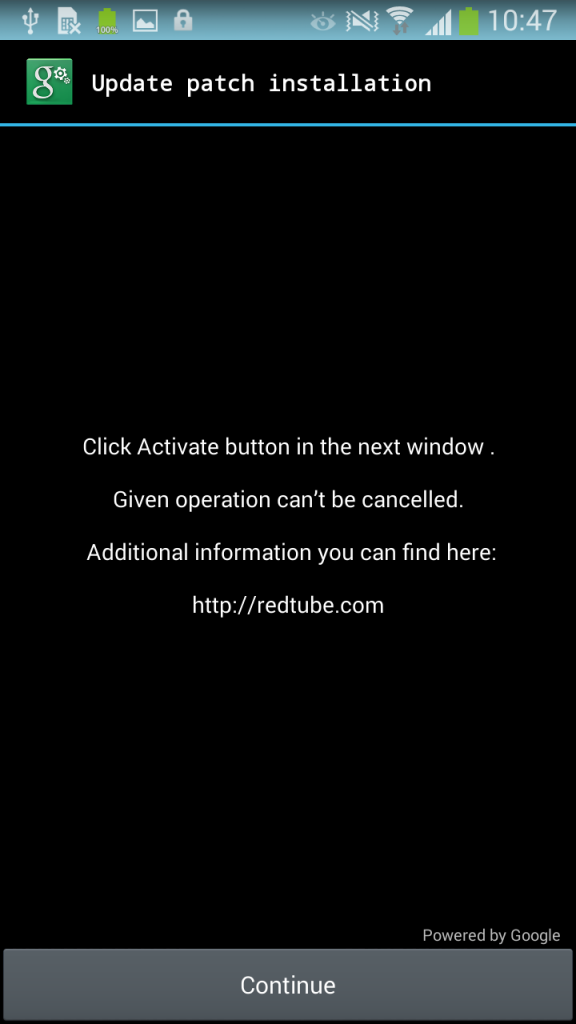
The new ransomware can gain "Device Administrator" privilege and then lock the phone with a PIN number, making it impossible to enter the OS. The malware still needs the user to act in order to gain Device Administrator privilege, so an "Update patch installation" message would have to be approved by the user for this to work.
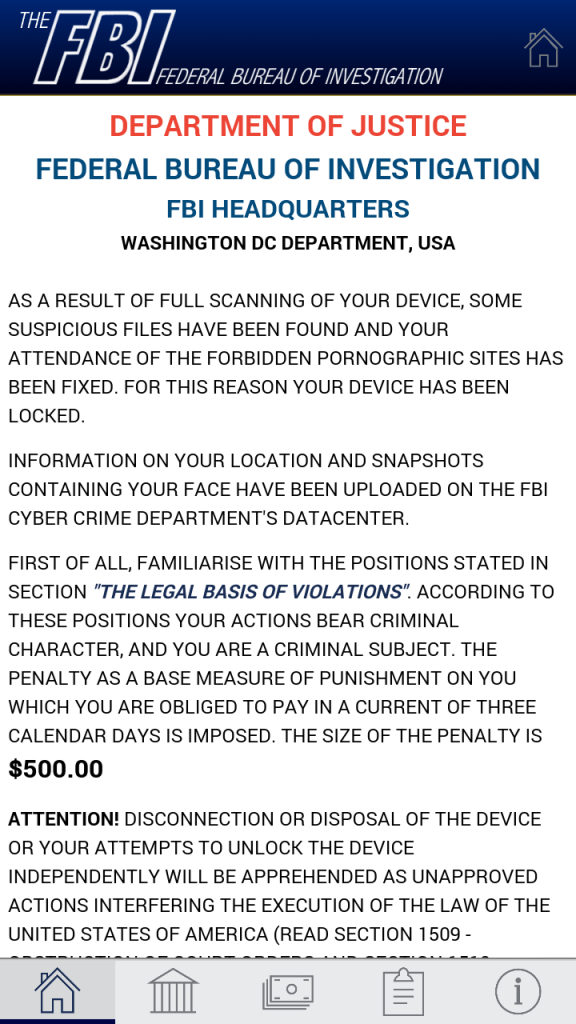
If the user clicks on the Continue button, then the malware can lock the device with a PIN number, and the user will be asked to pay a $500 ransom for supposedly viewing forbidden pornographic material. The message is made to appear as if it comes from the FBI.
The users can uninstall the Android/Lockerpin.A ransomware by going into Safe Mode or using ADB, but this is only going to reset the PIN number with a randomly generated one that won't be sent to the attacker anymore. That means neither the user nor the attacker behind the ransomware will be able to unlock the device any longer.
Users can unlock the device only if they reset it to factory settings, but some of their data could be lost in the process.
The Android/Lockerpin.A ransomware comes with a few self-protection mechanisms that help it against manual uninstallation by the user or by anti-virus apps, which it tries to kill. The anti-virus apps against which it protects itself are ESET Mobile Security, Dr.Web and Avast. However, the team at ESET said that its anti-virus has its own self-protection mechanism against this type of behavior.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
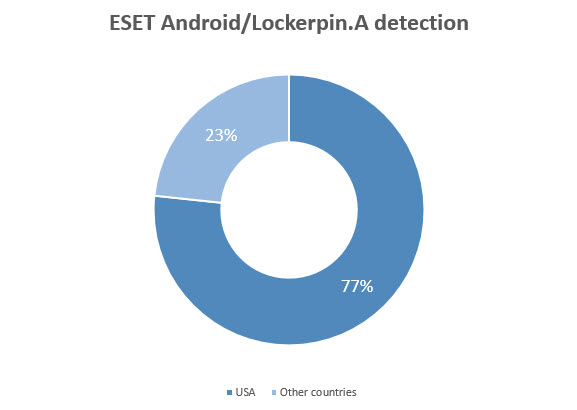
The way the ransomware is distributed is through an app called "Porn Droid." ESET discovered that 77 percent of the infected users were from the U.S. The good news is that the app can't be found on the Play Store, and users would have to manually enable "Unknown Sources" installation on their phones and then install the app from other third-party websites.
This is how most of the Android malware is in fact spread, so it's no surprise that the new ransomware is distributed this way, too. If you never install apps from sources other than the Play Store, then you should be reasonably safe against such malware. Otherwise, ESET recommended using its own mobile antivirus, which detects and stops the Android/Lockerpin.A ransomware.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
jimmysmitty But Linux kernal... secure....Reply
J/K. But this does show that anything that is popular enough will be vulnerable. Even Linux. It is just the way of the software. -
bogieboge Doesn't seem like a software security issue.Reply
1. The user has to enable 3rd party apps and accept a warning about unverified apps
2. Intentionally download and install the app from an unknown source
3. Grant admin privileges (maybe unknowingly)
Android gives the users more leash by allowing the install of 3rd party apps. The users just need to be smart enough to not hang themselves with that leash. -
jimmysmitty Reply16612307 said:Doesn't seem like a software security issue.
1. The user has to enable 3rd party apps and accept a warning about unverified apps
2. Intentionally download and install the app from an unknown source
3. Grant admin privileges (maybe unknowingly)
Android gives the users more leash by allowing the install of 3rd party apps. The users just need to be smart enough to not hang themselves with that leash.
It is the same with Windows though. Although there is no lock on third party program installs (could you imagine the backlash?) people still need to do the same thing. Normally the same thing comes in an email that people click OK to.
My only point is that anything popular enough will find ways around most security. There are other cases, even Apple had this same virus plague Mac OSX. -
jerm1027 Reply16612327 said:16612307 said:Doesn't seem like a software security issue.
1. The user has to enable 3rd party apps and accept a warning about unverified apps
2. Intentionally download and install the app from an unknown source
3. Grant admin privileges (maybe unknowingly)
Android gives the users more leash by allowing the install of 3rd party apps. The users just need to be smart enough to not hang themselves with that leash.
It is the same with Windows though. Although there is no lock on third party program installs (could you imagine the backlash?) people still need to do the same thing. Normally the same thing comes in an email that people click OK to.
My only point is that anything popular enough will find ways around most security. There are other cases, even Apple had this same virus plague Mac OSX.
I wouldn't say that exactly since linux is partitioned by default. A regular user can roam around in the user space all they want, but as soon as something attempts to modify the system, the user must confirm with a root password. With most Windows users, they are already admin/root and the User Account Control is a joke, and more of an annoyance than a security feature - it actually came from Linux, but because Windows is way more integrated, *everything* triggers a prompt. You can get a similar result by using Windows as a Standard User (most people don't), but it isn't exactly the same. For an example, I can't really run my VPN software without the password, and it never gave me an error, so it took me a while to figure out I needed to run the program as Admin. -
house70 Meh. Not really something average Joe needs to worry about. Too many security measures needs to be altered in order to make phone vulnerable, AND then one has to actively install malware from whatever source.Reply
Sticking with Amazon Appstore, Google Play or any other reputable app store will be safe.
This thing is the equivalent of dousing your house in gasoline, then lighting a match and complaining afterwards that it burned down.
This reminds me of the article a little while ago about the vulnerability of jailbroken iPhones. Except there the "jailbroken" bit was (rightfully) included in the title. Here the security downgrading steps necessary to become infected with this thing are mentioned in the last paragraph. Maybe the title should include altered/modified/ or otherwise intentionally crippled Android phones. Just a thought of even-headedness for the OP when reporting such issues. No wonder some people think of Android as less secure, when in fact requires quite a few steps and a good amount of determination to screw- up with the default settings, followed by a suicidal will to install apps from shady sources.
I, for one, still have yet to encounter an infected phone in the wild. -
LostAlone ReplyMeh. Not really something average Joe needs to worry about. Too many security measures needs to be altered in order to make phone vulnerable, AND then one has to actively install malware from whatever source.
Sticking with Amazon Appstore, Google Play or any other reputable app store will be safe.
This thing is the equivalent of dousing your house in gasoline, then lighting a match and complaining afterwards that it burned down.
This reminds me of the article a little while ago about the vulnerability of jailbroken iPhones. Except there the "jailbroken" bit was (rightfully) included in the title. Here the security downgrading steps necessary to become infected with this thing are mentioned in the last paragraph. Maybe the title should include altered/modified/ or otherwise intentionally crippled Android phones. Just a thought of even-headedness for the OP when reporting such issues. No wonder some people think of Android as less secure, when in fact requires quite a few steps and a good amount of determination to screw- up with the default settings, followed by a suicidal will to install apps from shady sources.
I, for one, still have yet to encounter an infected phone in the wild.
I totally agree. The tech press has done such an appalling job reporting about Android recently. To just skim articles you'd think that Android phones are being hijacked left and right, hackers just barging through their awful security. But that's completely false. The only real flaw in Android is that if you really want to it'll let you turn off the safe guards and even then you need to go and acquire the malware basically off your own back.
Shock, horror - If you disable all the safeties and install software of dubious provenance then bad things can happen. That's every computer in the whole world. -
kenjitamura ReplyBut Linux kernal... secure....
You either didn't read the article or have poor reading comprehension. Either way this article cannot be interpreted as "android is insecure". A user has to explicitly disable a security feature, search for the malware on a dubious site, and install it with prompts before it can do anything.
J/K. But this does show that anything that is popular enough will be vulnerable. Even Linux. It is just the way of the software.
I like house70's analogy of it being like dousing your house in gasoline and striking a match and then complaining that the house is on fire because it really is like that.
-
targetdrone I find it funny how you catch this virus by looking at porn on your phone.Reply
Actually I think most viruses are transmitted by looking at porn and other illicit data.
-
turkey3_scratch Reply16621065 said:I find it funny how you catch this virus by looking at porn on your phone.
Actually I think most viruses are transmitted by looking at porn and other illicit data.
Viruses come from the end user doing something stupid. Website viruses used to be huge, but the majority of them resulted from Adobe Flash, as it was highly used on every site in the past. With HTML5 and the absence of Flash on many websites, most viruses will now come from people downloading a program and running the executable. -
house70 Reply16621065 said:I find it funny how you catch this virus by looking at porn on your phone.
Actually I think most viruses are transmitted by looking at porn and other illicit data.
Even watching porn can be done the stupid way (via your admin account on your main machine, using a poorly secured browser) or the smart way (I don't have to spell it for you, but it's basically the opposite of that).