Apple 'AceDeceiver' DRM Flaw Allows Malware To Install Itself On Non-Jailbroken iPhones
Security researchers from Palo Alto Networks uncovered a new iOS malware family that takes advantage of vulnerabilities in Apple’s DRM software and can infect non-jailbroken devices. The researchers called the malware “AceDeceiver.”
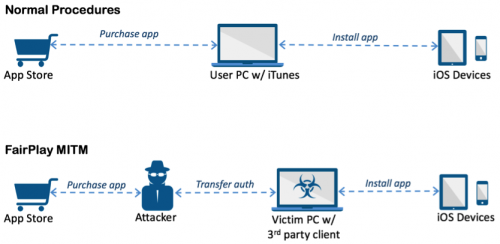
AceDeceiver uses a novel way of attacking iOS devices by managing to install itself without any enterprise certificates. Instead, it exploits design flaws in Apple’s “FairPlay” DRM mechanism that allow the malware to be installed on non-jailbroken devices.
Apparently, this “FairPlay Man-In-The-Middle” attack was identified for the first time in 2013, but so far Apple still hasn’t fixed it. It’s been used to spread pirated iOS apps so far, but now malware makers seem to be taking advantage of it as well.
According to Palo Alto Networks, three “wallpaper apps” from the AceDeceiver family have been uploaded to Apple’s App Store since July 2015, and they managed to bypass the review process seven times in total (four of which were updates).
Apple removed these apps from the App Store in late February 2016, but the malware-infected apps had to have been in the store only once; after that, it can get a copy of authorization from Apple, which will allow it to spread itself to iOS devices without being available on the App Store.
The malware creator also built a Windows program called Aisi Helper that offers iOS services such as system re-installation, jailbreaking, system backup, device management and system cleaning. However, the program also installs the malicious apps on any iOS device connected to that Windows PC. Then, the malicious apps ask users to input their Apple credentials to gain more features.
For now, AceDeceiver has been found only on iOS devices from China. However, the Palo Alto Networks researchers believe that this type of attack could spread elsewhere because of how easy it is to infect non-jailbroken iOS devices without enterprise certificates. The installation of these malicious apps doesn’t require any user confirmation on iOS devices, making the malware harder to detect, as well.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.