Devilish SATAn Hack Turns Drive Cable Into Antenna to Steal Data
All your data belong to us
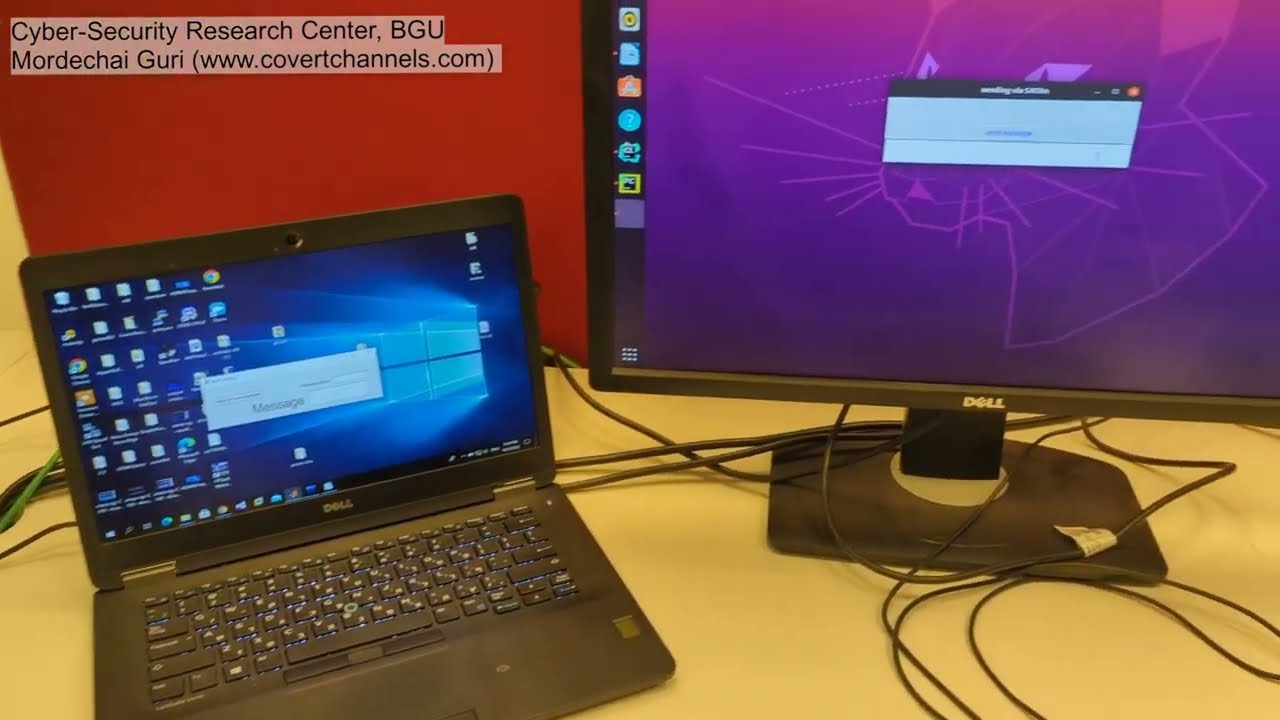
Researchers today revealed a new 'SATAn' attack that can turn a SATA cable into a radio transmitter, thus allowing a hacker to exfiltrate data from a system that isn't connected to a network and transmit it to a receiver 1m away — all without physically modifying the SATA cable or hardware. The software-based technique can work from user space or through a virtual machine (VM), and you can see a short demo in the embedded video below.
The ubiquitous SATA connection is used in billions of devices worldwide to connect hard drives and SSDs inside a PC, making it the perfect target for hackers looking for a sophisticated attack with a wide footprint.
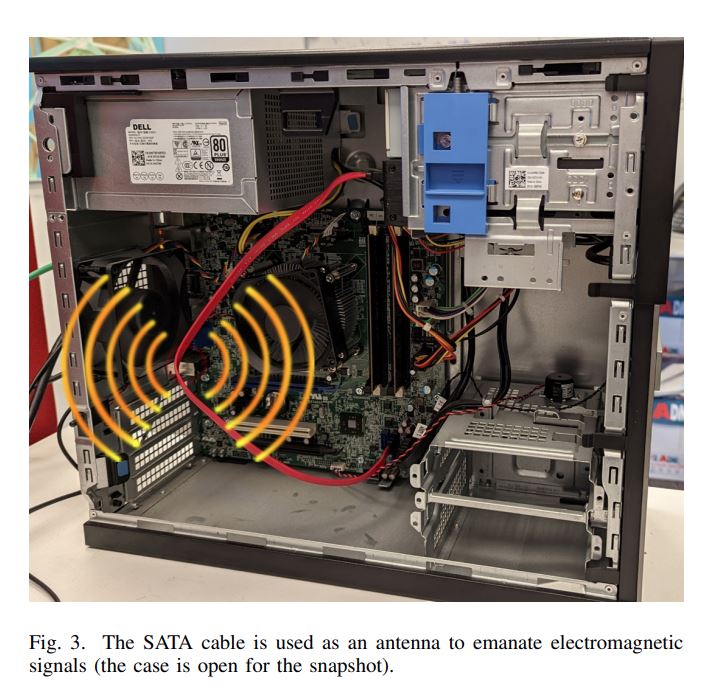
Some of the most sensitive data on the planet is stored in air-gapped systems. These systems are entirely isolated from any connection to the outside world, like a network or the internet, and also don't have any hardware that can communicate wirelessly, like wireless Bluetooth or Wi-Fi hardware. As such, it requires ultra-sophisticated techniques to steal data from them. Researcher Mordechai Guri at the University of the Negev, Israel, has accomplished the feat by converting a standard SATA cable into a radio transmitter, but without actually making any physical modifications to the hardware.
As with all computer interfaces, the SATA bus generates electromagnetic interference during normal operation, and if used correctly, that interference can be manipulated and then used to transmit data. In this case, the researcher used the SATA cable as a wireless antenna that operated on the 6 GHz frequency band, thus transmitting a short message to the nearby laptop. This attack can be used in concert with keyloggers to steal passwords or other sensitive data. Likewise, attackers can employ other mechanisms to steal important data, like files and images.
Naturally, the attacker would first have to install malicious software onto the targeted machine, but as we've seen with Stuxnet and other attacks, USB devices with malicious code can spread malware inside protected systems. Otherwise, the attacker would need physical access to install the attack payload.
Once installed, the malicious software first encodes the data to be stolen. Then it conducts certain types of file system access, like reads and writes, in a controlled manner to generate a signal on the cable. While either read or write operations can effectively create the correct signals, the researcher notes that read operations typically don't require higher permissions at the system level and generate stronger signals (up to 3 dB) than write operations. The researchers also noted that background operations that incur other traffic to the storage device are generally fine. Still, intense drive activity can muddy the transmissions, so it's best to pause or stop the transmission when heavy background activities occur.
The attacker can then receive the signal from a nearby device, but the reach is limited. In this case, the receiver has to be within 1m of the transmitter due to increased bit error rates associated with longer distances. The receiving device, in this case, a laptop, uses a Software Defined Radio (SDR) receiver to receive the signal.
The philosophy behind this type of attack isn't new — researchers have previously demonstrated manipulating the clock rates of an AMD Radeon graphics card to create a radio transmitter that generated a signal that an attacker could receive through a wall 50 feet away — but the hacks are becoming increasingly sophisticated as researchers find new interfaces to exploit.
There are several ways to mitigate these types of attacks, but they aren't foolproof. The paper suggests that the first line of defense is to implement policies that prevent the initial penetration, along with other tactics, like forbidding radio receivers in the secured facility. Naturally, spooks can also use monitoring hardware of their own to detect if any nefarious transmissions are underway, or install software on secured machines that monitors abnormal file usage, like odd read and write activity to temporary files. These tend to be low-yield methods of detection, though, because the transmissions and drive activity are easy to disguise.
The most direct method of protection would be to add extra electromagnetic shielding either on the SATA cable or to the PC's case. But then again, perhaps the complexity of the attack itself is the best protection for us normal folks. Building the receiver is surprisingly simple, but developing the requisite software and encoding techniques would require a high level of sophistication, meaning that these types of attacks are most likely relegated to nation-states engaging in espionage, meaning the average user has nothing to worry about.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
WilliamRJK Does not work on laptops (no SATA cables)Reply
Does not work on systems with a caddy to a cableless backplane (Mac Pro 1,1-5,1 for example)-. Does not work on SAS (twisted pair and 4 lanes per cable instead of 1, plus shielded, if that works i'm impressed af)
Does not work on PCIe SATA SSDs (these do not exist anymore, Samsung PM951 is good example, has SATA traces on PCB but just a few mm total)
Does not work on PCIe NVMe SSDs
SATA is being phased out at an ok pace and with the above i don't see much danger in this for ultra secure systems (= secured datacenter, not a CIA field office with a NUC...)
Very interesting concept though, i don't know why we Israelis always come up with such hacks, weird. -
escksu Pretty useless hack I have to say....Reply
This is its biggest failure......
1. Hacker has to access the system physcially to install the software to get the hack to work....
This isn't the movies, if its that easy to gain access to such a system, people wouldnt even need to hack. Even insider jobs are very very difficult to perform to due to security. Its extremely hard to plug a USB drive into the machine to install the software.
This is 2nd failure....
allowing a hacker to exfiltrate data from a system that isn't connected to a network and transmit it to a receiver 1m away...
Again, not the movies. If the server/PC (whatever) its placed in a secure location, it won't be right against the wall for obvious reason. Computers are mostly placed in racks. You need to clearance around the racks in order to access it for maintenace and installation. -
ingtar33 Reply
does not work on proper computer cases either; a proper computer case will act like a faraday cage. there is a reason they have the side of the computer case off in the demo, with the side on it wouldn't work either. Highly unlikely to work in a rack mount server either. those cases are literal faraday cages, and of course they're all SAS; typically cordless...WilliamRJK said:Does not work on laptops (no SATA cables)
Does not work on systems with a caddy to a cableless backplane (Mac Pro 1,1-5,1 for example)-. Does not work on SAS (twisted pair and 4 lanes per cable instead of 1, plus shielded, if that works i'm impressed af)
Does not work on PCIe SATA SSDs (these do not exist anymore, Samsung PM951 is good example, has SATA traces on PCB but just a few mm total)
Does not work on PCIe NVMe SSDsSATA is being phased out at an ok pace and with the above i don't see much danger in this for ultra secure systems (= secured datacenter, not a CIA field office with a NUC...)
Very interesting concept though, i don't know why we Israelis always come up with such hacks, weird.
this also doesn't work with EM shielded SATA cables which they do make. This may work with tempered glass side panels, but no one has a boutique computer case they don't connect to the internet.
this is a parlor trick not data theft. -
shady28 Another example of how these security lab types are sitting around wasting time and money with far-fetched attacks, apparently to impress the less technically savvy types or get media attention.Reply -
TwoSpoons100 Would have made more sense to hit the mouse or keyboard cable : fully exposed, longer, and generally crappier cable than SATA. And operate at a lower frequency than 6GHz for more range.Reply
And as has been pointed out - if someone can get this spyware onto an air-gapped machine, then there are bigger problems to fix than shielding the SATA cables! -
WilliamRJK Replyshady28 said:Another example of how these security lab types are sitting around wasting time and money with far-fetched attacks, apparently to impress the less technically savvy types or get media attention.
Education is free in Israel and such projects are sponsored by our agencies (mostly mossad). I dont see it as waste of money, more a waste of time at Technion that could be used for better things like Iron Beam. -
Murissokah It's an exploit targeted at air-gapped facilities, it doesn't target notebooks or current hardware. Think highly secure, air gapped facilities, like nuclear power plants. They run the same hardware for decades, so servers and desktops running SATA hardware are very much relevant. These computers have measures to prevent any form of data copy so no networking, blocked USD storage. So even if you manage to sneak malware in (say you compromise a software vendor and inject malware in their code), you still wouldn't be able to get the data out. This can be used for that.Reply
If you are thinking about how this would be useless in a modern datacenter or an enterprise workspace, you missed the point entirely. Modern datacenters are the polar opposite of an air-gapped facility. -
InvalidError I didn't see the SDR antenna and receiver in the video. I'd imagine the signal through a secure server's steel window-less rack-mounted chassis would do a rather pretty good job shielding its internals from short-range RF tricks. If you are going to use RF hardware this sensitive, then an easier lower-tech approach would be to create a power virus that modulates power draw to encode data and do your RF attack on the power lines, you'd probably be able to do 1kbps that way.Reply
Typical rows of racks only give you access to the front and back. If you need access through the top or sides, you have to pull stuff out.escksu said:Computers are mostly placed in racks. You need to clearance around the racks in order to access it for maintenace and installation. -
digitalgriffin This is why "sensitive" buildings are a giant EMF/Faraday cages, including the windows. Even artwork hanging on a wall can be used as a transmitter with a passive power source.Reply
How a Gift from Schoolchildren Let the Soviets Spy on the U.S. for 7 Years - Atlas Obscura -
mikeebb Reply
If it's attacking a server, chances are there's no keyboard, mouse, or even display attached, so the signal would have to be generated internally.TwoSpoons100 said:Would have made more sense to hit the mouse or keyboard cable : fully exposed, longer, and generally crappier cable than SATA. And operate at a lower frequency than 6GHz for more range.
And as has been pointed out - if someone can get this spyware onto an air-gapped machine, then there are bigger problems to fix than shielding the SATA cables!
That said, if you have enough access to plug in a USB drive to install the software needed for this, then why bother with this? Just copy what you want to the USB drive and leave. Unless you're doing a Stuxnet with USB drive left around a parking lot ...
Funny, in ancient days, there was software that would play a tune with a Radio Shack Model 1 (aka broadband RFI generator) using a BASIC program containing instructions that generated RFI that would be picked up as tones by a AM radio next to the computer. What's old is new again...