Digmine Cryptocurrency Bot Spreads Via Facebook Messenger
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
The Trend Micro security company announced that it found a new cryptocurrency-mining bot, "Digmine," spreading through Facebook Messenger.
The bot first appeared in South Korea and has since spread to Vietnam, Azerbaijan, Ukraine, Vietnam, Philippines, Thailand, and Venezuela. Trend Micro believes that at the rate it’s spreading, it should reach many more countries soon.
How Digmine Works
Trend Micro said Digmine currently only works on the desktop, so mobile users will not be affected by the bot. The malware looks like a video file to unsuspecting victims, but it’s actually an executable script. If users had set their desktop Facebook accounts to log in automatically, the malware will log in for the user and then spread itself to all of their Facebook friends via a link to the fake “video.”
The malware is updated through a command-and-control (C2) server, so it could gain more destructive capabilities in the future, such as taking further control of the infected Facebook accounts. The Digmine bot, like any other cryptocurrency-mining malware, will aim to stay on the victim’s computer for as long as possible in order to maximize the number of CPU or GPU cycles it can use to mine cryptocurrencies.
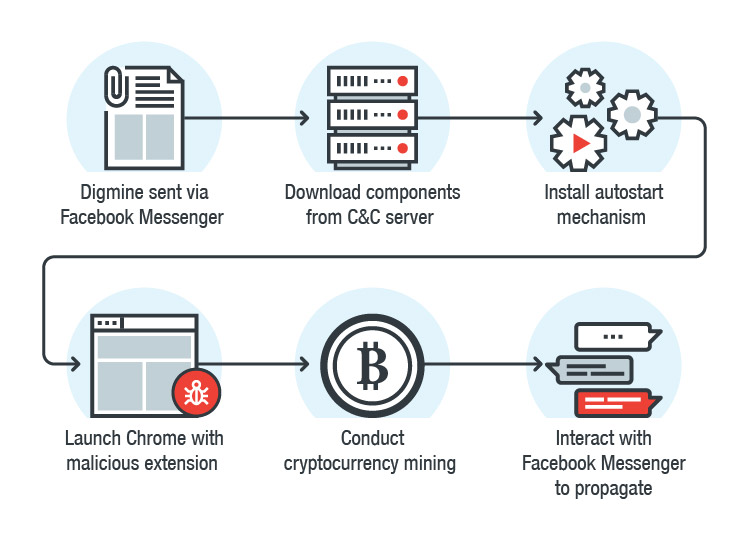
Infection Chain
Digmine’s executable script is a downloader file that downloads additional components from the C2 server after it installs itself on the user’s machine. The additional components are saved in the %appdata%\<username> directory.
Digmine will then perform other actions, such as installing a registry autostart mechanism, and load a malicious extension into Chrome. Extensions can usually be installed only from the Chrome Web Store, but the malware's author bypasses that restriction via the command line.
The browser extension is what helps the Digmine miner propagate to the victim’s Facebook friends. If the user has set his or her Facebook account to log in automatically, then the extension can interact with the user’s Facebook data, such as the list of contacts.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Recommendations
To avoid falling victim to Digmine, Trend Micro recommended you follow social media best practices such as logging out of the accounts they don’t use, removing apps that are connected to their social media account, using a strong password coupled with two-factor authentication, and being aware that some of the links that are shared to them may contain malware.
The security company disclosed the Digmine bot to Facebook, which then promptly removed many of the bot’s links from its platform. Facebook also said that if they suspect a user’s computer is infected with malware, it will provide a free antivirus scan from one of its partners.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.