Google Reveals 'Half-Double' Technique for Exploiting Rowhammer in DDR4
It's that Rowhammer time again.
A seven-year-old flaw in DRAM chips is making another comeback. Google revealed this week that it's discovered a new technique, Half-Double, that can be used to exploit the Rowhammer bug thought to have been fixed with the release of DDR4.
Rowhammer was discovered in 2014 when researchers showed that it was possible to manipulate data stored in DDR3 memory by repeatedly accessing ("hammering") a single row of memory cells to cause bit flips in adjacent rows.
Manufacturers responded with Target Row Refresh (TRR) mitigations, but in March 2020, researchers showed that it was possible to bypass those protections in a paper titled "TRRespass: Exploiting the Many Sides of Target Row Refresh."
But TRRespass still operated under the assumption that Rowhammer attacks were only capable of affecting rows of memory adjacent to the row being hammered. Google said that doesn't seem to be the case, which is where Half-Double comes in.
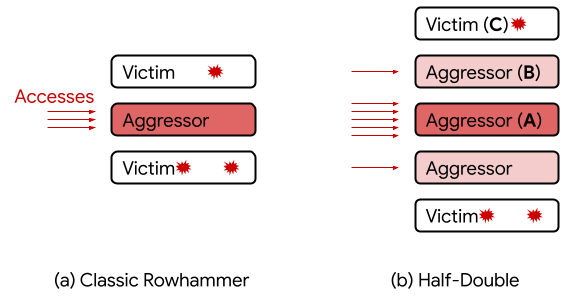
"Unlike TRRespass, which exploits the blind spots of manufacturer-dependent defenses, Half-Double is an intrinsic property of the underlying silicon substrate," Google said. "This is likely an indication that the electrical coupling responsible for Rowhammer is a property of distance, effectively becoming stronger and longer-ranged as cell geometries shrink down. Distances greater than two are conceivable."
Google said it's been working with JEDEC, a trade group devoted to open standards for the semiconductor industry that counts more than 300 companies among its members, and "other industry partners" to work on solutions to Rowhammer.
"We are disclosing this work because we believe that it significantly advances the understanding of the Rowhammer phenomenon, and that it will help both researchers and industry partners to work together, to develop lasting solutions," Google said. "The challenge is substantial and the ramifications are industry-wide. We encourage all stakeholders (server, client, mobile, automotive, IoT) to join the effort to develop a practical and effective solution that benefits all of our users."
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
rluker5 Hopefully Raptor Lake will come with an edram like cache that defeats this like the 5775c had. Highly used data got moved to cache, effectively sandboxing it.Reply
That and it would be great to have more of that processing power quickly fed by something faster than dram. -
InvalidError Since normal software has no control over where in the randomized physical memory its memory allocations will land and no way of knowing where the target data is, it should be virtually impossible for attackers to target specific data. I'd be more worried about random memory corruption from this style of attack.Reply -
InvalidError Also, server memory usually has ECC so if rowhammer-style attacks manage to flip a bit, ECC should flip it right back the next time an address gets read, making it that much more difficult to extract any data.Reply -
pjmelect I have always thought that this type of attack was impossible, as memory test should find out any tendency for adjacent memory cells to flip and manufacturers of the memory go to great lengths to ensure that this does not happen, further just because memory cells are numerically next door to each other does not mean that they are physically close to one another on the memory chip, in fact numerically adjacent memory cells can be anywhere on the die and the layout is different for different manufacturers.Reply
I have discovered that to get the bits to flip they have to alter the memory timings so that the memory is at the edge of not working, again this is dependent on the type and manufacture of the memory.
If you have access to a computer that allows you to change its memory timings and allows you to write to adjacent memory bits and to also know the layout of the memory chips of the particular manufacture that is in the computer, and not to crash the computer doing this, then this attack might work, but if you have this level of access to the computer then why not just simply write to the memory locations you want to change.