How To Hack A Car Over The Internet
"Even though they were driving slowly, my heart was pounding. I had no control." This is Andy Greenberg's description (who wrote the superb Wired article on the Jeep hack) of that now iconic picture of the Jeep Cherokee being driven into a ditch by its hackers, Charlie Miller (Twitter) and Chris Valasek (IOactive), with Andy aboard. Both did this research in their spare time, though Chris was able to count some of it as work time, as it was related to his job.
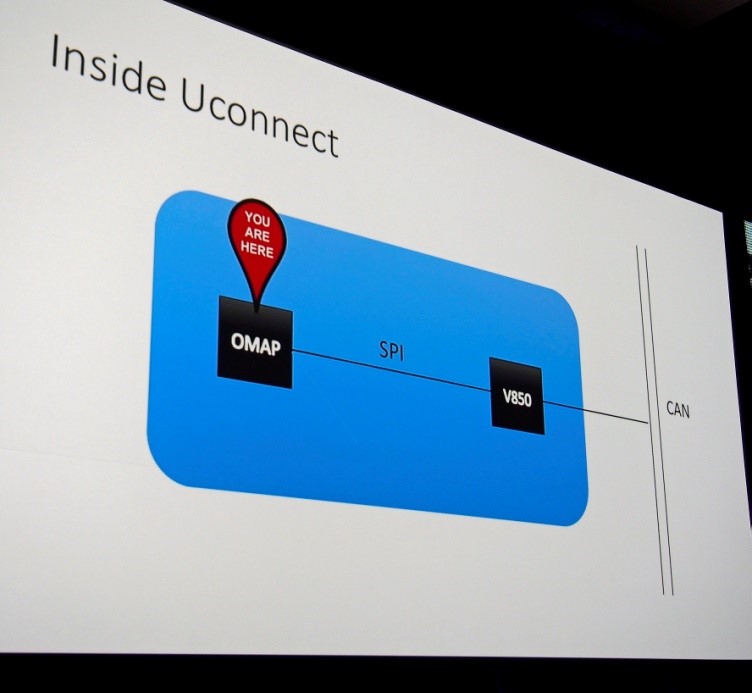
In a highly entertaining and comedic presentation this week, Chris and Charlie detailed the results of their project that has been ongoing for at least two years. Last year at DefCon/Black Hat, they described how one might communicate between the entertainment system and the CAN (Controller Area Network) Bus, the bus that melds together all of the car control systems.
The image above shows Charlie's Jeep after he remotely steered it into a ditch, with Andy Greenberg unable to brake. He pressed the brakes to the floor, the brake lights were on, but the car rolled forward anyway (idle speed).
The entertainment system connects to the CAN Bus, but doesn't normally allow commands to be sent. Charlie and Chris rewrote the V850 firmware.
They had several false starts. They jailbroke the Uconnect system (entertainment), but that wasn't required for remote exploitation. They hacked the wireless system -- the Jeep had a wireless hotspot, which has now been disabled with the latest firmware update -- but that also wasn't required. The wireless system had several shortcuts that allowed them to guess the password.
Both hacks let them become familiar with the car systems and served as an invaluable source for interprocess communications.
The final remote step occurred over cellular communications, which were on even with no opt-in. They had to obtain the particular car's IP as well; this took a few weeks for them to figure out. The hardest part was rewriting the firmware of the V850 chip to allow them to send arbitrary commands to the CAN Bus to do their bidding. That was possible because updates are not authenticated. The firmware software they used was not entirely disclosed. The communication over the cellular network used port 6667, and that was necessary to find the Jeep's IP; Sprint has now blocked that as well. Port 6667 is not normally used for other important functions on that Sprint network, though it could be used for an IRC relay.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Description of this hack will be published in a detailed paper on Monday. There were approximately 1.4 million vehicles potentially susceptible to this hack. After the Wired disclosure, Sprint blocked the port that allowed Charlie and Chris to take vehicle control within two weeks. At least two venues of attack, probably more, were fixed. Defense in depth. Charlie felt that this was unprecedented, and that as hackers, he and Chris were able to make a difference: the quickness (in car terms, anyway) of the Chrysler recall, several senators calling for legislation mandating security, and finally, car manufacturers paying attention to security.
Follow us @tomshardware, on Facebook and on Google+.
-
NightLight ReplyThe security fix is very simple.
that's basically the fix for EVERY vulnerability
DO NO NETWORK the engine control module!
-
milktea Why doesn't ppl think this is another Gov/NSA sponsored project?Reply
First they control your communications, and now they control your transportation. -
JPNpower ReplyWhy doesn't ppl think this is another Gov/NSA sponsored project?
First they control your communications, and now they control your transportation.
Because that would be against the law so hard it would be high risk/little return. Seriously, if they wanted to get you, they have safer ways of doing so. (Like the police! jk)
-
boosted1g On the bright side, since the car uses Sprint's network, the hack is severely limited to cars that can maintain a good reception signal with Sprint. Talk about thinning out the herd.Reply -
boosted1g Reply16413823 said:Why doesn't ppl think this is another Gov/NSA sponsored project?
First they control your communications, and now they control your transportation.
Is it just me, or is it impossible to read this without reading it out loud in a "Merica" accent?
The government has no desire to kill off Americans buying cars. let alone new cars.
That American is either on entitlement programs so they need that person's vote, or that person actually works a decent enough job to afford a new vehicle and thus they desperately need that person to pay taxes to pay for all the entitlement programs. -
targetdrone Reply16413823 said:Why doesn't ppl think this is another Gov/NSA sponsored project?
First they control your communications, and now they control your transportation.
Is it just me, or is it impossible to read this without reading it out loud in a "Merica" accent?
The government has no desire to kill off Americans buying cars. let alone new cars.
That American is either on entitlement programs so they need that person's vote, or that person actually works a decent enough job to afford a new vehicle and thus they desperately need that person to pay taxes to pay for all the entitlement programs.
And what happens when the productive person says They had enough and won't pay their taxes? An unexplained car crash. -
JPNpower Reply16415025 said:16413823 said:Why doesn't ppl think this is another Gov/NSA sponsored project?
First they control your communications, and now they control your transportation.
Is it just me, or is it impossible to read this without reading it out loud in a "Merica" accent?
The government has no desire to kill off Americans buying cars. let alone new cars.
That American is either on entitlement programs so they need that person's vote, or that person actually works a decent enough job to afford a new vehicle and thus they desperately need that person to pay taxes to pay for all the entitlement programs.
And what happens when the productive person says They had enough and won't pay their taxes? An unexplained car crash.
Chrysler have announced that they will donate a brand new Jeep to Edward Snowden as a recognition of his work in revealing government spying.
-
DookieDraws Good grief, this is getting ridiculous! What's getting hacked next, a toilet?Reply
By the way, my awesome cat hacked up 2 big hair balls today. Yup! My cat's a hacker! :p -
clonazepam ReplyWhy doesn't ppl think this is another Gov/NSA sponsored project?
First they control your communications, and now they control your transportation.
Well, as far as transportation conspiracy theories... what I've heard, is... "if you build it, they will come". Listen in on some transportation meetings. Some of their bright ideas are changing traffic lights' timings to create more congestion to push people toward "greener" methods, especially public. They also come up with ideas like shutting down entire highway lanes to encourage public transit. Look up budgets for highway maintenance, and see how little actually goes to highways. Anyway, enough of that fun stuff I heard on AM radio while cruising to and from LA.
Anyone remember when Tom's Hardware taught us how to use a search engine to connect to and take over peoples' webcams? Man, those were the days. In my 20 or so minutes of freetime, I annoyed a home owner by moving his camera back and forth as he tried to correct it, and spied on a box of kittens. Where's the tutorial? /s