Intel Ups Data Center, Firmware Security With New SGX Card and Open Source Software
Ahead of the RSA 2019 conference next week, Intel announced two major hardware-enhanced security solutions for data centers and firmware developers: the Software Guard eXtensions (SGX) Card for servers that use processors without support for SGX (older than Skylake), and the Host-Based Firmware Analyzer (HBFA) for the open source UEFI implementation called TianoCore.
Intel SGX Card
Starting with the Skylake generation of processors, Intel included support for a new security feature called SGX. Applications that make use of Intel’s SGX can create encrypted regions in active memory that the host and any application running on the host can’t read. This allows developers to protect sensitive information, such as encryption keys from malware that infects the host operating system, as the malware wouldn’t be able to see inside the secure enclaves.
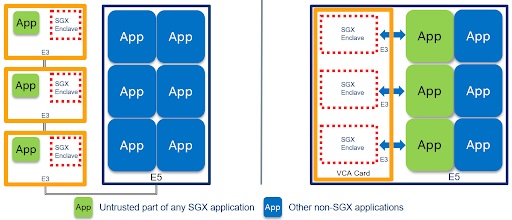
Intel’s new SGX Card is a repurposed Visual Compute Accelerator (VCA) that has the graphics accelerator disabled but still comes with three Xeon E-series processors and the SGX module built-in.
At first glance it seems like Intel is trying to sell three extra processors for every SGX module sold. However, the vendor in its announcement claimed the three processors are required for “offloading performance-hungry tasks that require additional protection.” According to the company, a standard 2U Intel Xeon Scalable server can support up to four SGX Cards, which means up to 12 extra processors will be used in combination with the SGX modules.
SGX Card vs. SGXSpectre, Foreshadow Attacks
Many of the major public cloud services, including Microsoft Azure, IBM Cloud Data, Baidu and Alibaba, as well as some security-focused applications, such as Signal, have adopted SGX for its security promises. However, we’ve recently seen that it’s not infallible.
SGX seems to be vulnerable to side-channel attacks, such as SgxSpectre, that take advantage of Intel CPUs' speculative execution capability. Until Intel disables speculative execution on its CPUs or comes up with a new design that completely stops all speculative execution-related side-channel attacks dead in their track, this issue will likely not be resolved, as per recent research.
Intel hasn’t clarified whether or not the SGX Card is anymore secure against SgxSpectre than regular processors with SGX support, but that seems unlikely at the moment.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Another related attack also takes advantage of Intel CPUs’ support for Hyper-Threading (HT) to exploit and compromise SGX enclaves. So far, Intel has only offered partial protection against this, but some security experts believe the only protection against this type of attack would be to disable HT on Intel’s CPUs.
Host-Based Firmware Analyzer (HBFA)
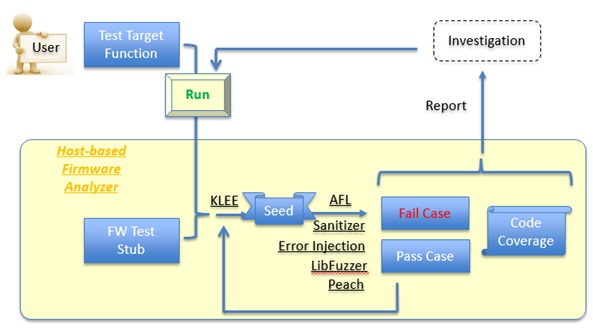
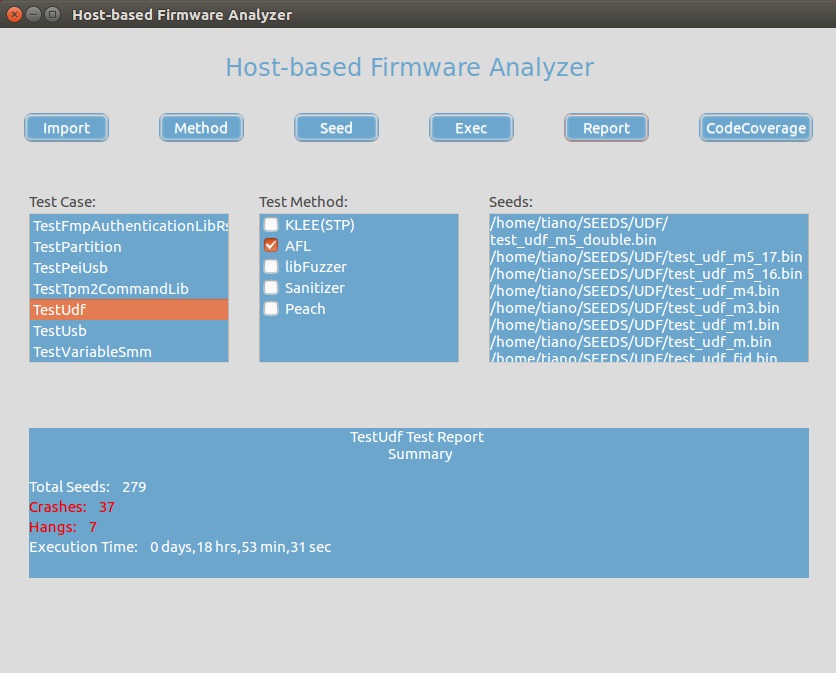
Intel created the open source HBFA test suite to enable advanced testing of UEFI and UEFI PI drivers in the developer’s OS environment. The HBFA comes with support for modern software vulnerability testing tools, such as fuzzing frameworks, symbolic execution, address sanitization and code coverage reports, as well as methods for fault injection and trace.
According to Intel, these testing tools and methods have rarely been applied to firmware because firmware, unlike drivers and applications, lack direct interfaces to the OS. HBFA introduces a stub interface for firmware components based on TianoCore EDK II, enabling firmware developers to test firmware components prior to system integration.
Intel intends to release the HBFA as an open source contribution to the TianoCore community. The company noted that the use of HBFA should be in addition to existing guidelines for secure code design, code review, test strategies and test tool development.
Other Intel-Related Security News
Intel also announced that its Threat Detection Technology (TDT) now supports Linux servers and has evolved its machine learning models to detect unauthorized execution of cryptomining and targeted attacks.
Intel partnered with Eclypsium, which recently uncovered how easily backdoorable Supermicro’s servers are, to develop the Eclypsium Platform. Organizations can use the platform protect their entire hardware and firmware against various threats.
In late January, Fortanix, an Intel partner, launched its Enclave Development Platform (EDP). It uses Intel SGX and the Rust programming language to create significantly more secure enclaves for applications. Rust is the Mozilla-backed language that aims to eliminate all memory corruption vulnerabilities (which currently comprises a large portion of all software vulnerabilities).
Want to comment on this story? Let us know what you think in the Tom's Hardware Forums.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.