Intel-Tsinghua Jintide Xeon Processor: Hot Chips 2019 Live Coverage
Tsinghua and Intel unveiled more details about the "Jintide" Xeon processors here at Hot Chips 31.
Intel has a partnership in China with Tsinghua University, long known to be heavily influenced by the Chinese government, and Montage Technology Global Holdings, a Chinese server vendor, that allows the development of a co-processor that connects to Intel's Xeon cores to provide China-approved encryption/decryption technologies. These two solutions are combined in a single "Jintide" package.
Given the ongoing U.S.-China tradewar, which finds the U.S. government banning joint ventures with Chinese interests (like the banning of AMD's JV), the presentation comes at a curious time.
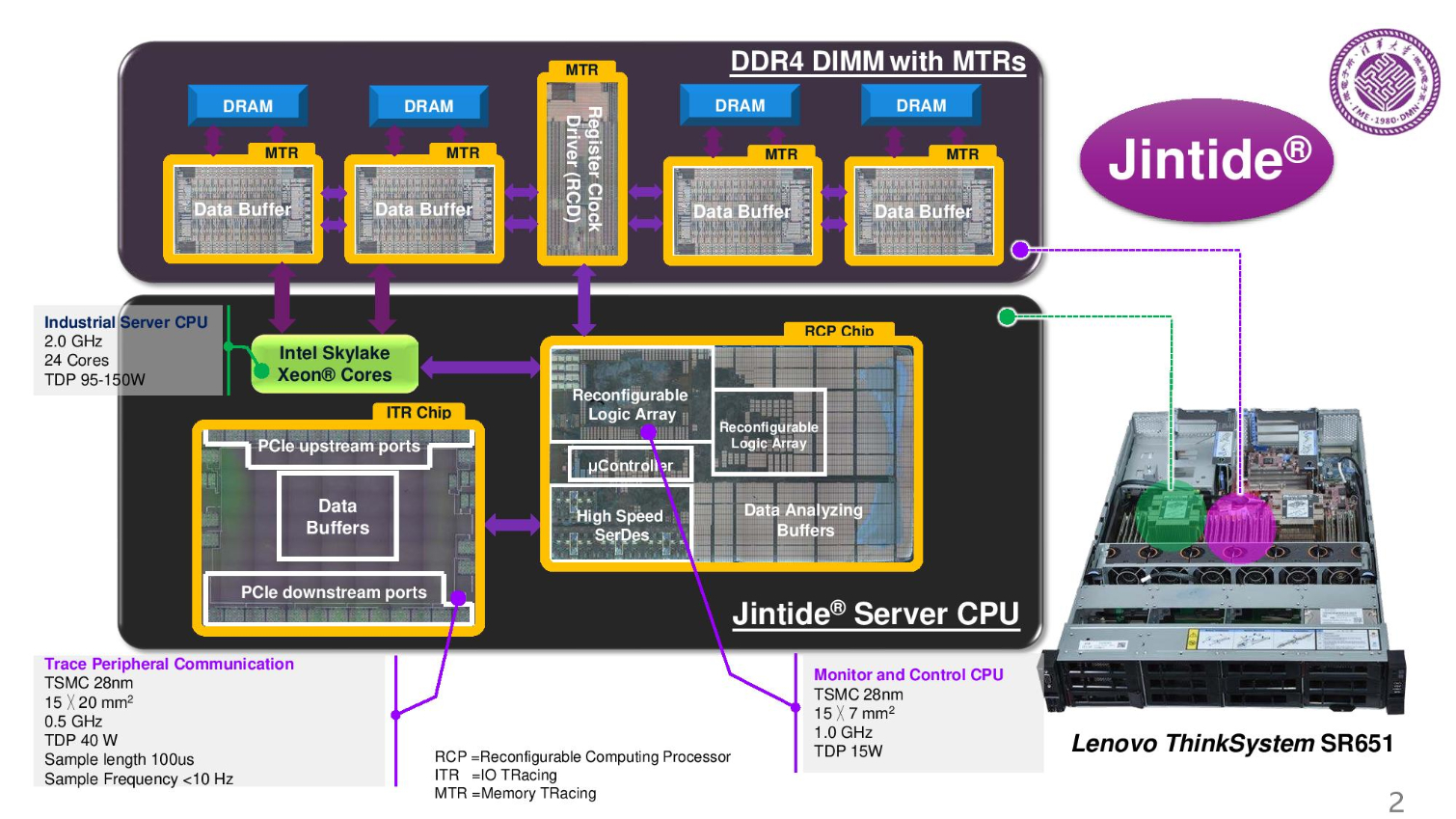
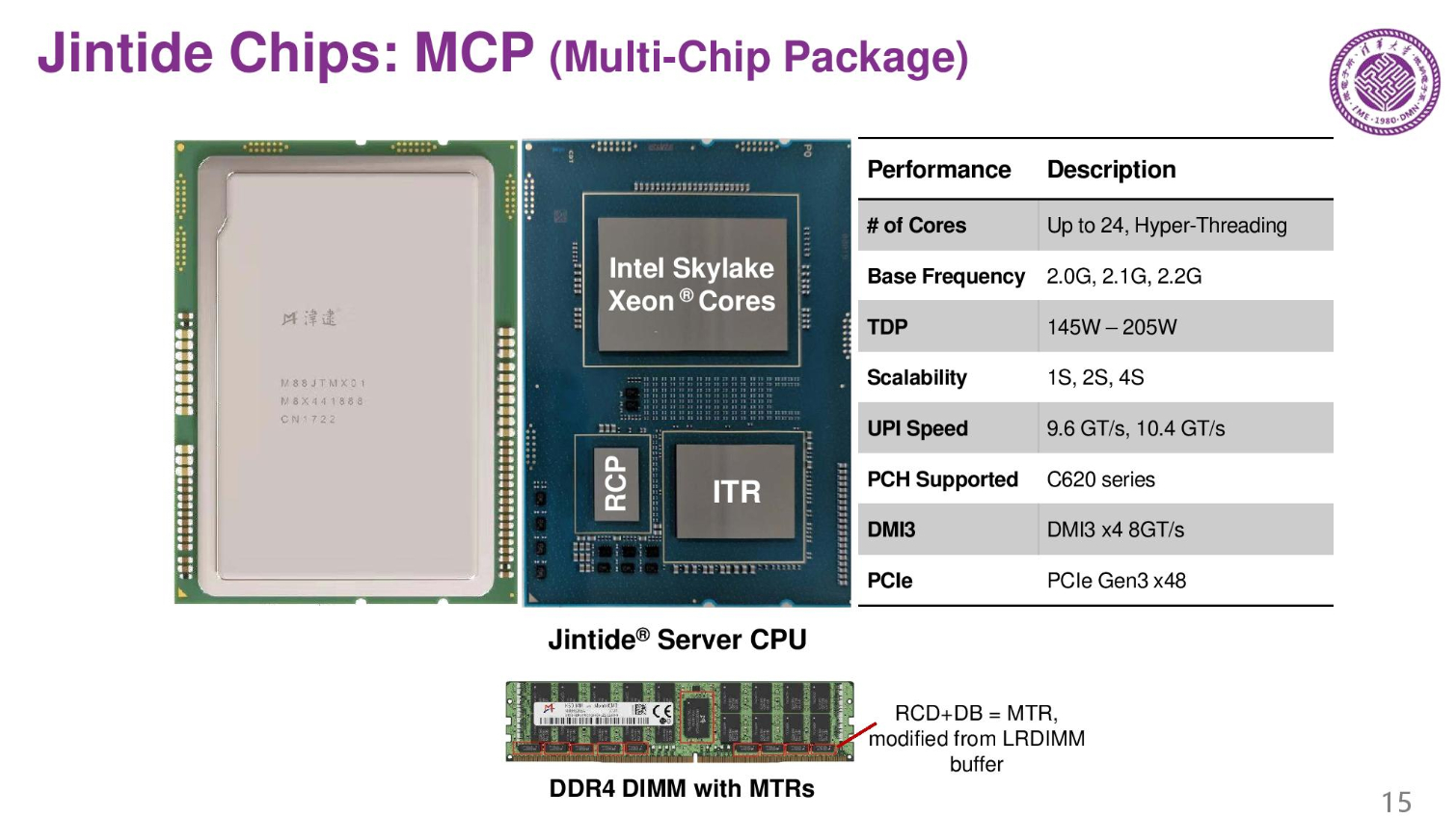
Tsinghua replaced the register clock driver and the data path with their design and also added a memory tracing chip and an I/O tracing chip. They integrated two extra chips into the CPU package.
Motivation: Hardware Security and Dynamic Security Check
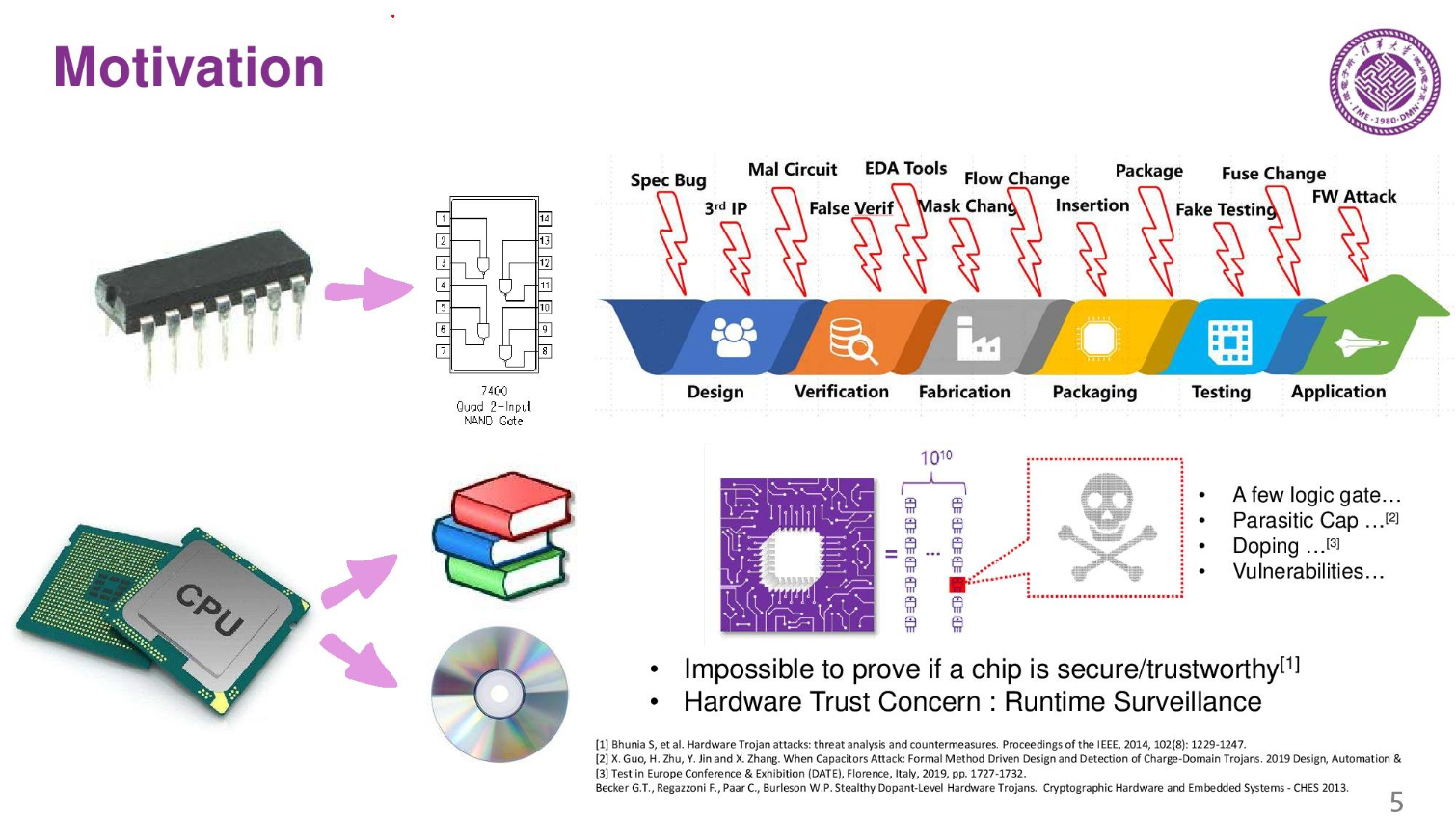
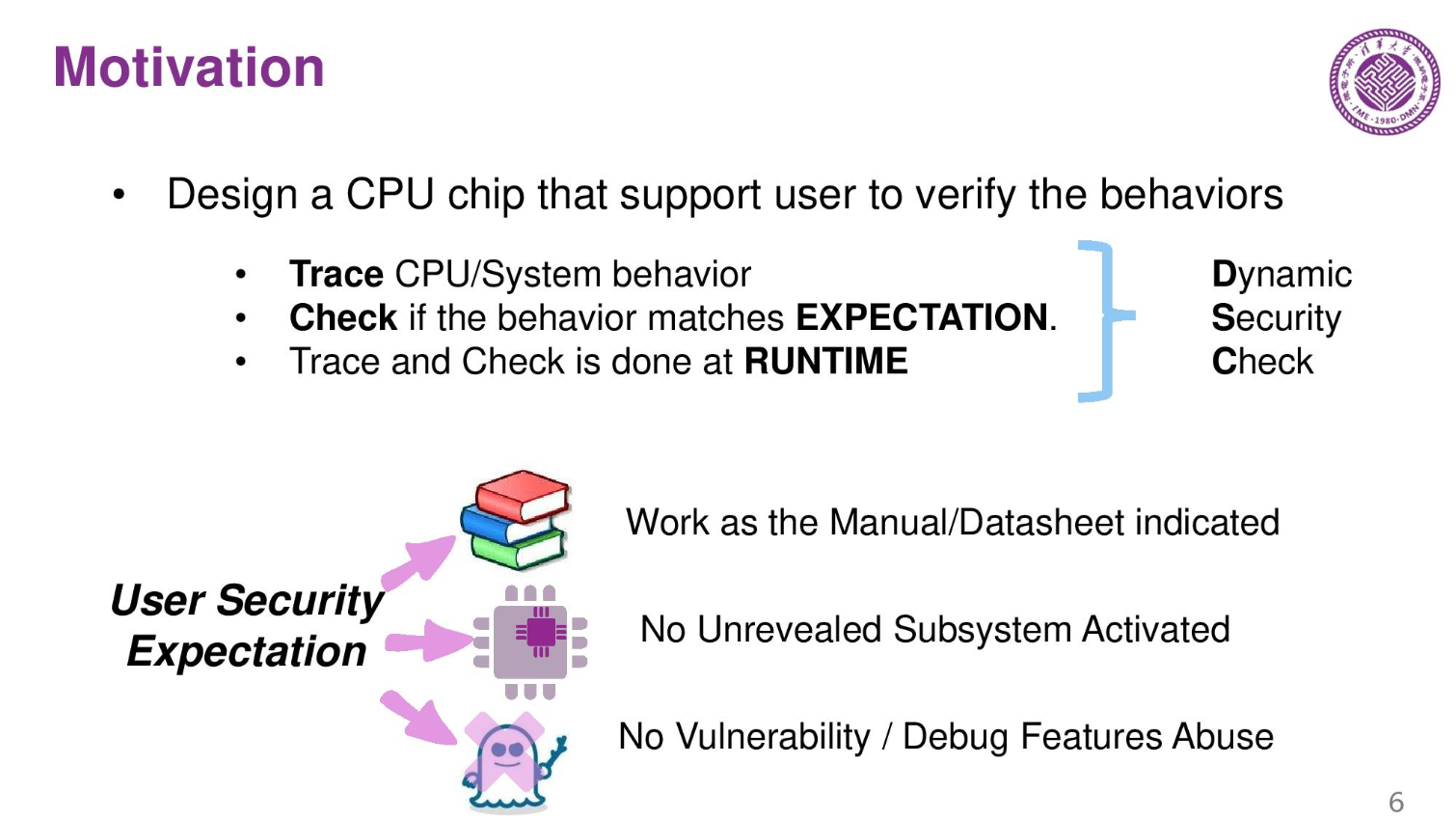
Design flow is complex, so production of a modern chip passes through many countries. There is no way to tell if there are modifications to the chip, so China wants to monitor the chips. It is almost impossible to prove a chip is 100% secure. The only way to fix the issue is run-time surveillance to make sure the chips aren't compromised.
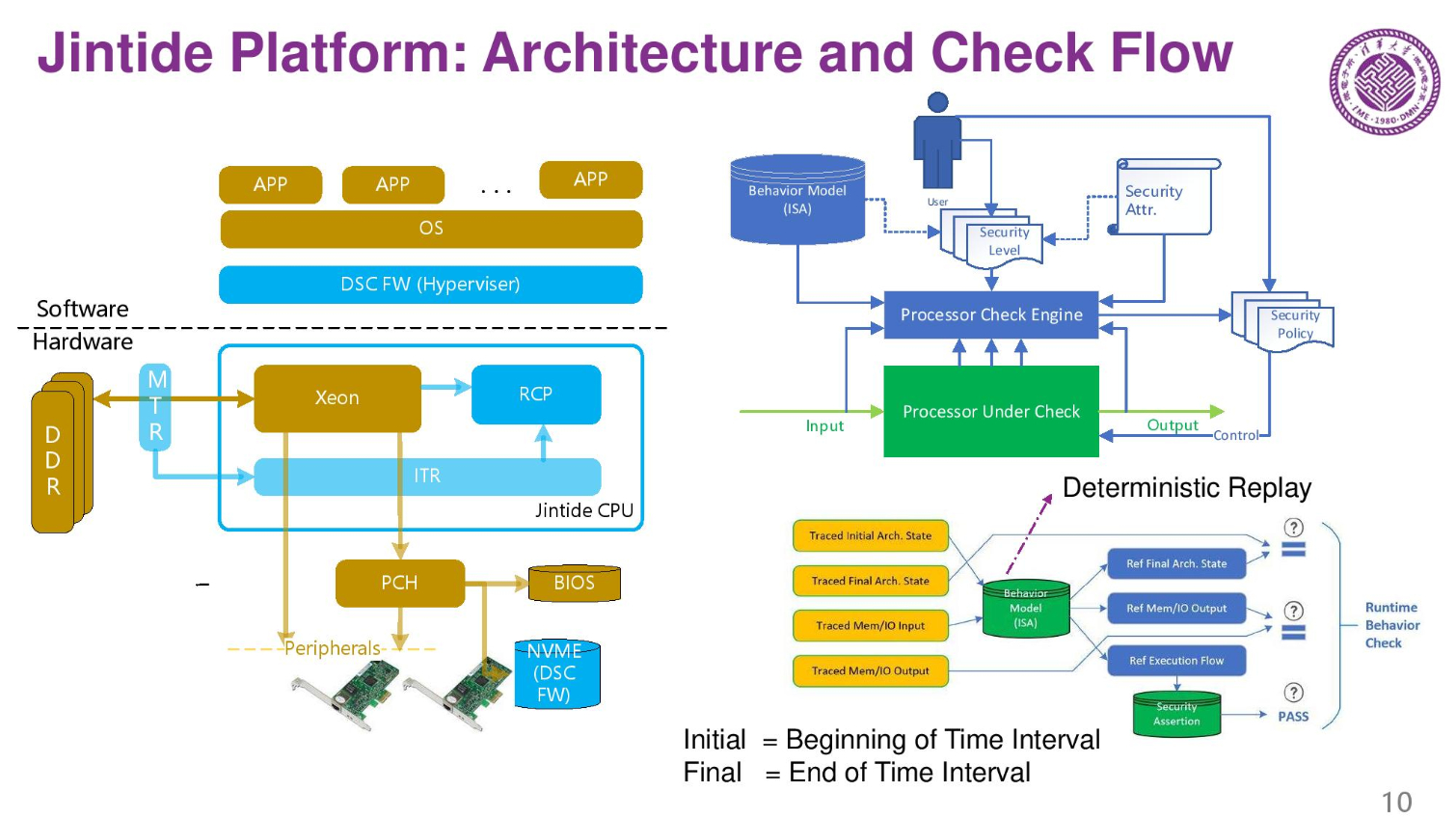
Three years ago the company designed a few tracking chips that can verify the behavior of the primary compute chip. They trace the system and CPU behavior and make sure that it matches expectations. This is called a dynamic security check.
Jintide Platform: Architecture and System Features
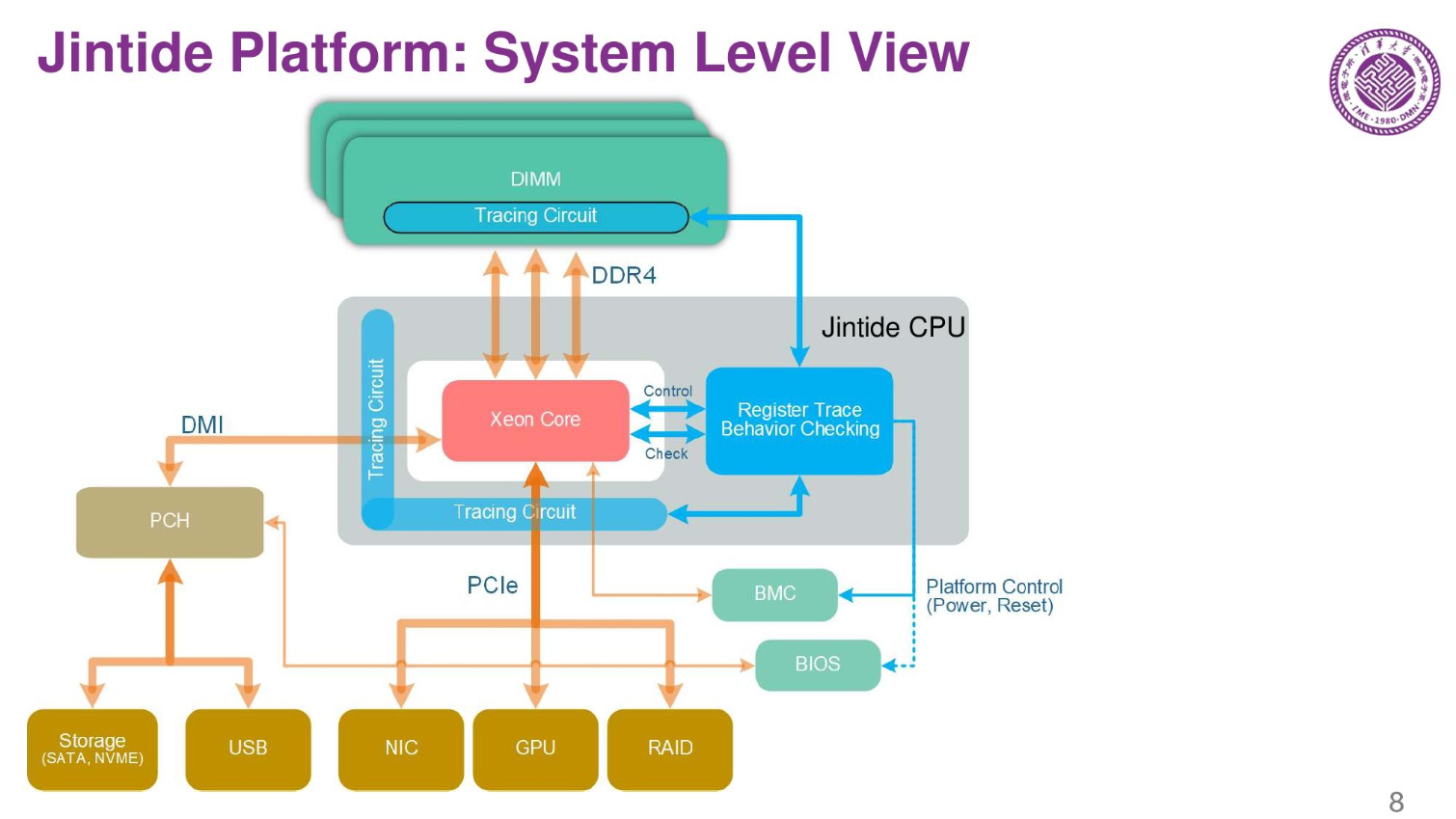
The basic platform consists of a standard server platform and they use tracking chips to monitor the CPU, memory, and all I/O coming in and out of the server. The only way to trace the hardware correctly is to trace it at the hardware level. Software won't work.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
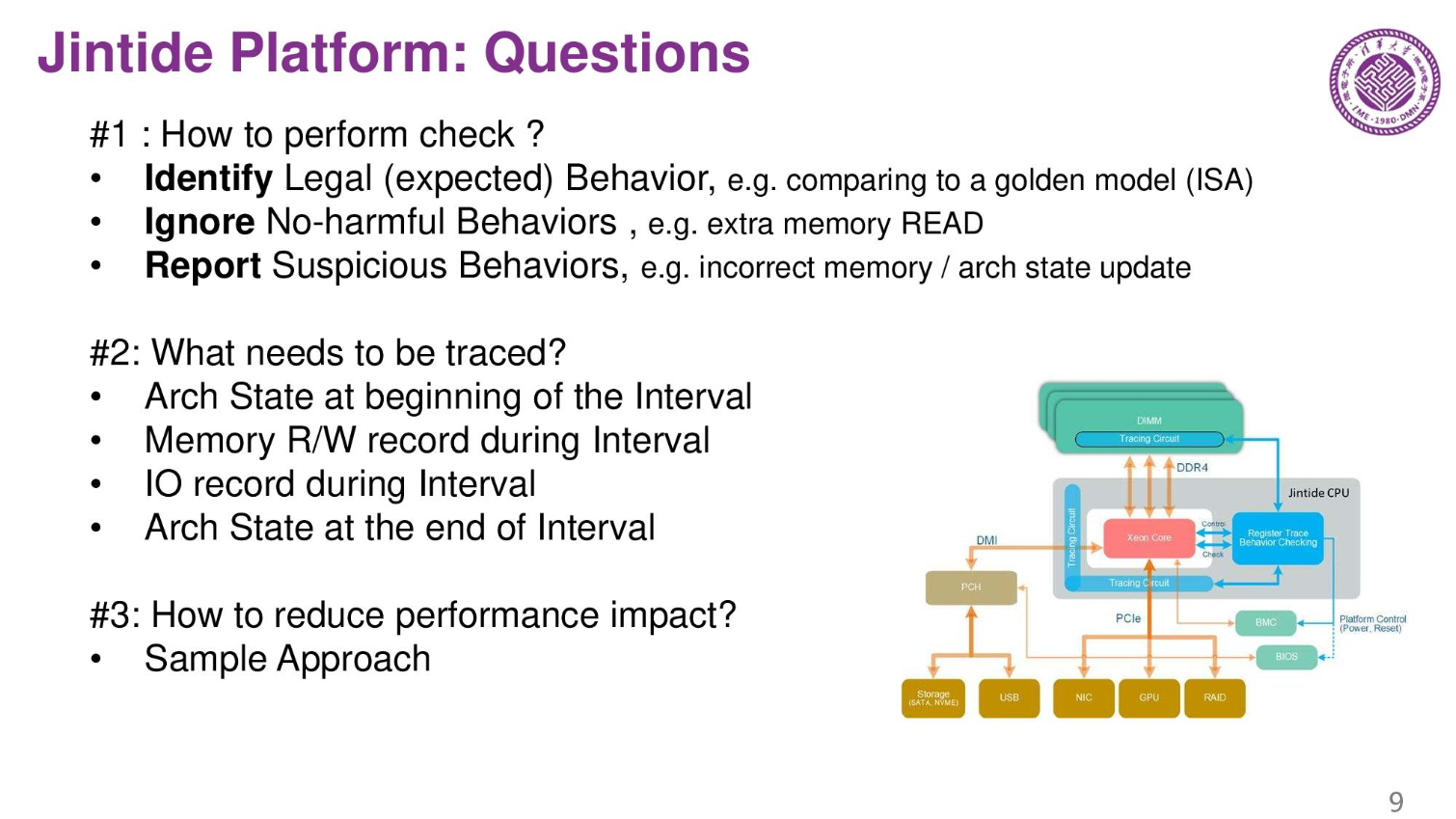
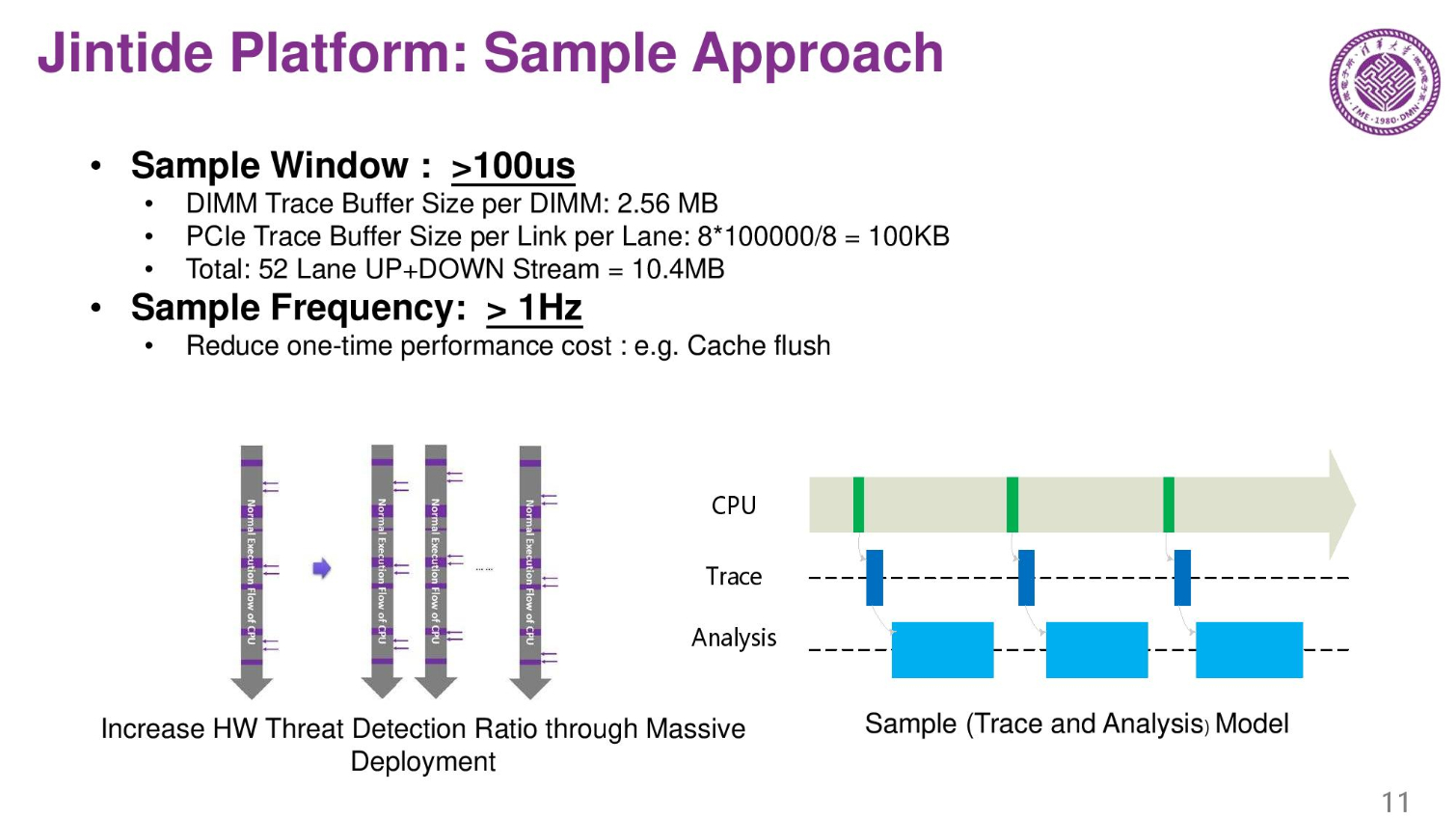
The system can identify good behavior, ignore non-harmful behaviors, yet report suspicious behaviors. Here we also see a list of the items the external chips trace. It is key to retain performance, so reducing overhead from the tracing process is a primary goal.
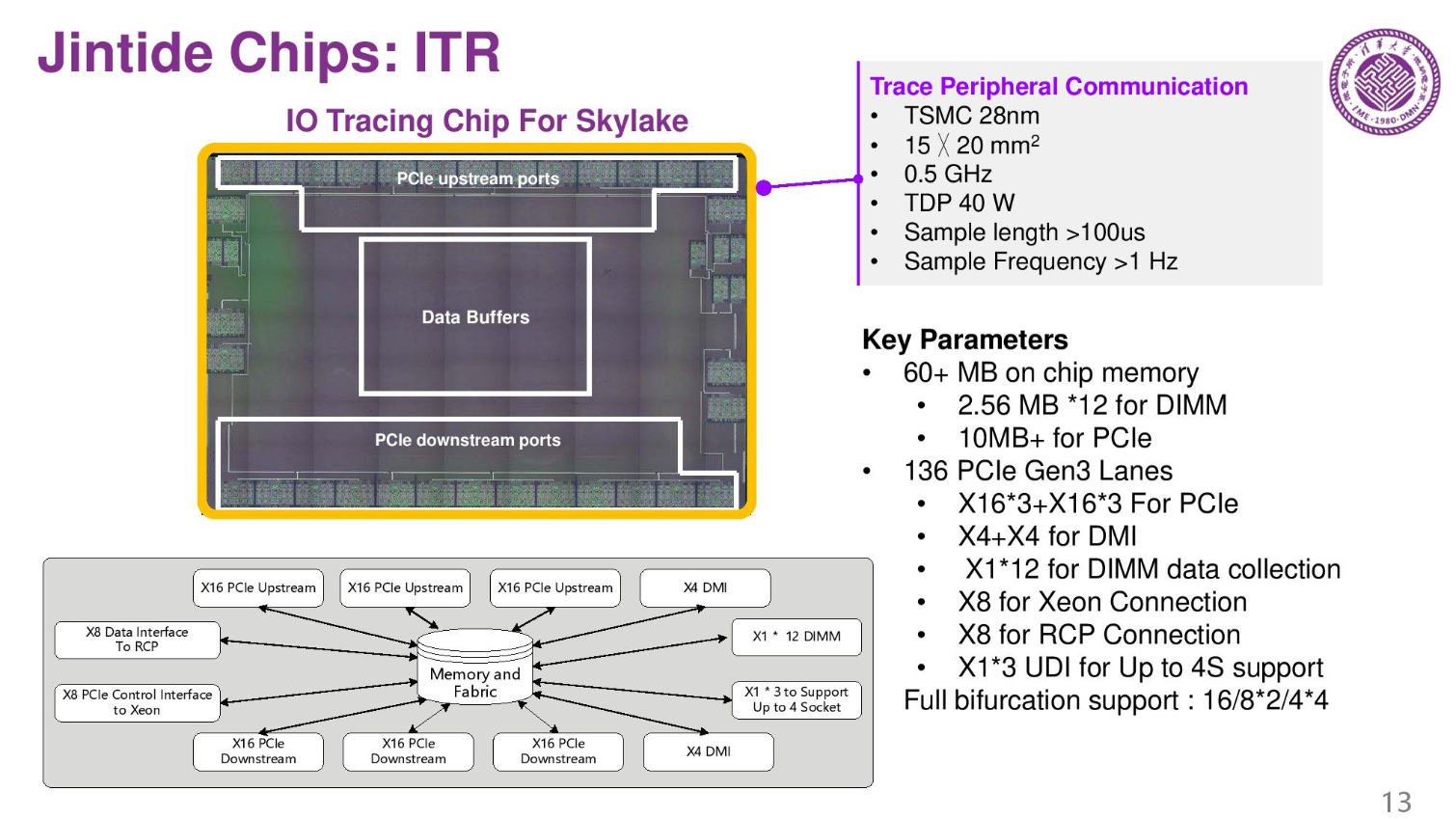
This is done with three total chips (fabbed on 28nm TSMC). These chips are connected through the on-die PCIe lanes on the Skylake chip. These are probably the spare lanes that Intel disables.
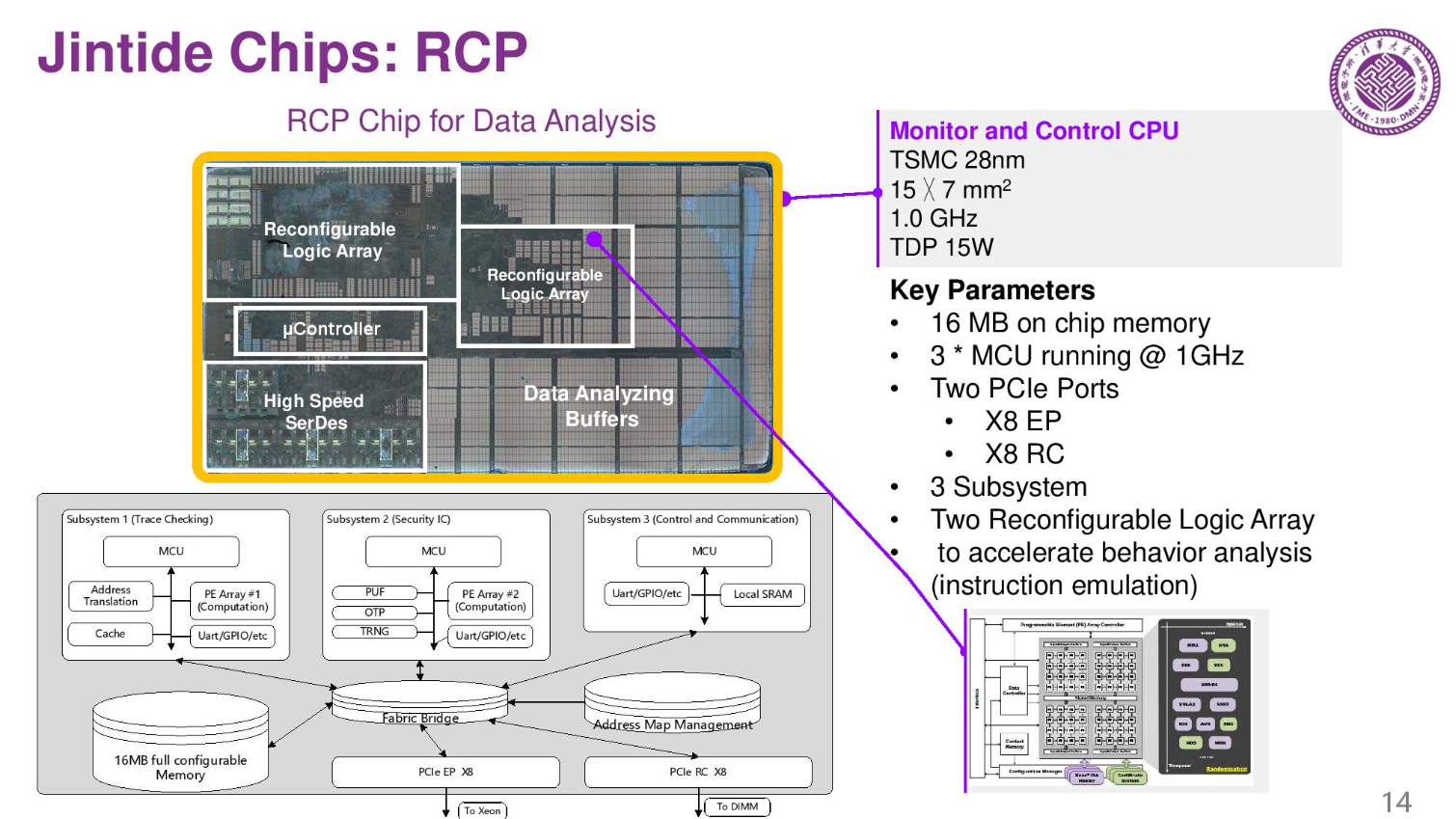
The MTR (memory tracing chip) tracks memory buffers, and ITR and RCP chips track the processor and other I/O. A special firmware also does checking and tracing. On the right is the check flow during run time.
The chips trace at 100ms intervals. For Skylake processors they use 52 lanes of upstream and downstream checks, needs to store 10.4 MB.
Jintide Chips: Specification and Tapeout Results
This chip is the I/O tracing chip. 300mm squared running at a 40W TDP. That's quite a bit of power for surveillance.
The second chip is the RCP. It has three microprocessors inside, and there are encryption and decryption features in the chip. There are also two reconfigurable arrays.
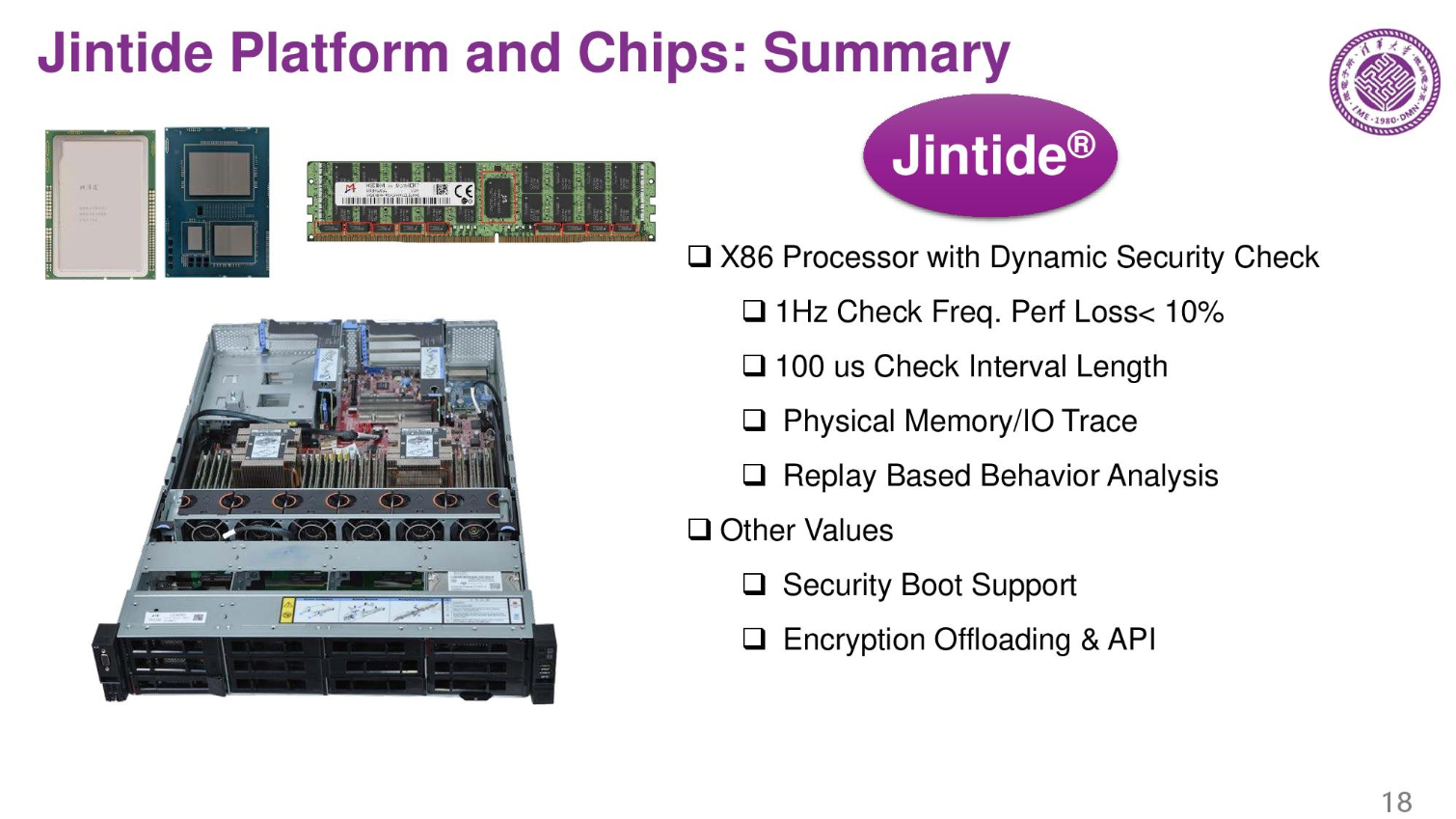
Here we can see the multi-chip package they designed. The pin-out is almost the same as a regular Skylake, but it has two extra chips, so power consumption is higher.
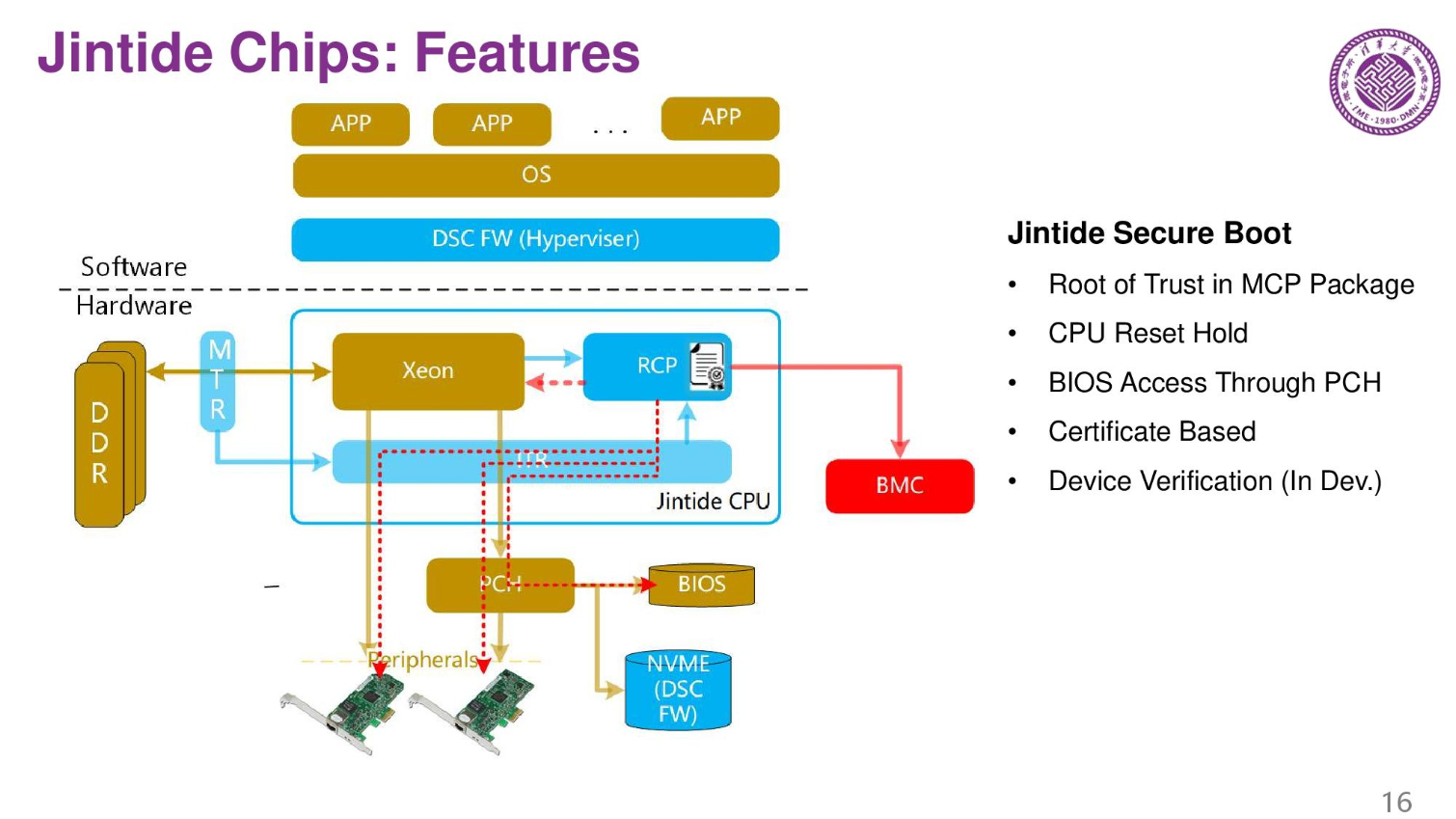
The MCP also serves as a root of trust for the system. It also detects and identifies all of the devices connected to the server.
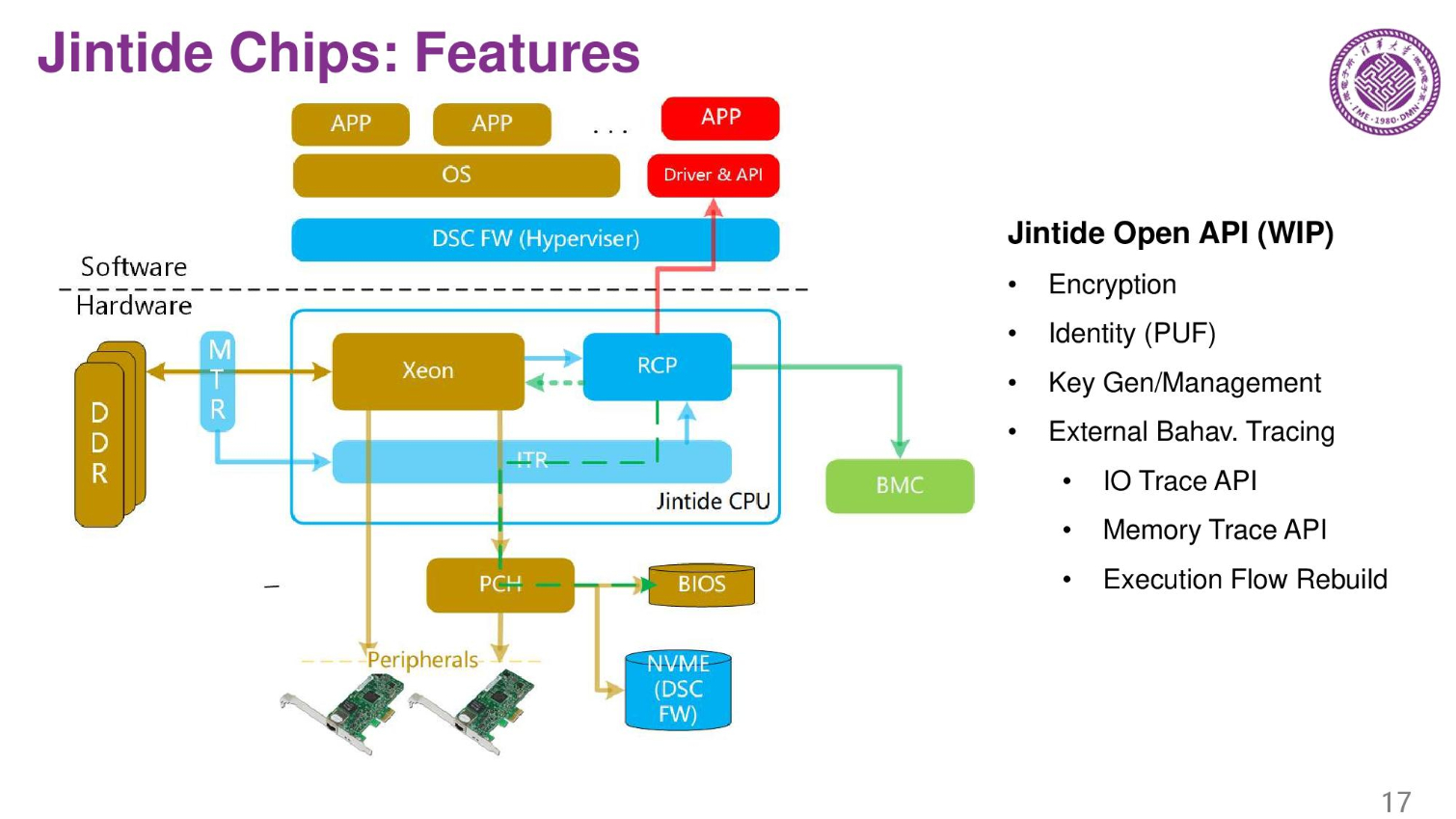
The system also offers encryption features through the Jintide Open API that runs in a custom hypervisor that also needs installed in the system. The system also generates and manages the platform's encryption keys.
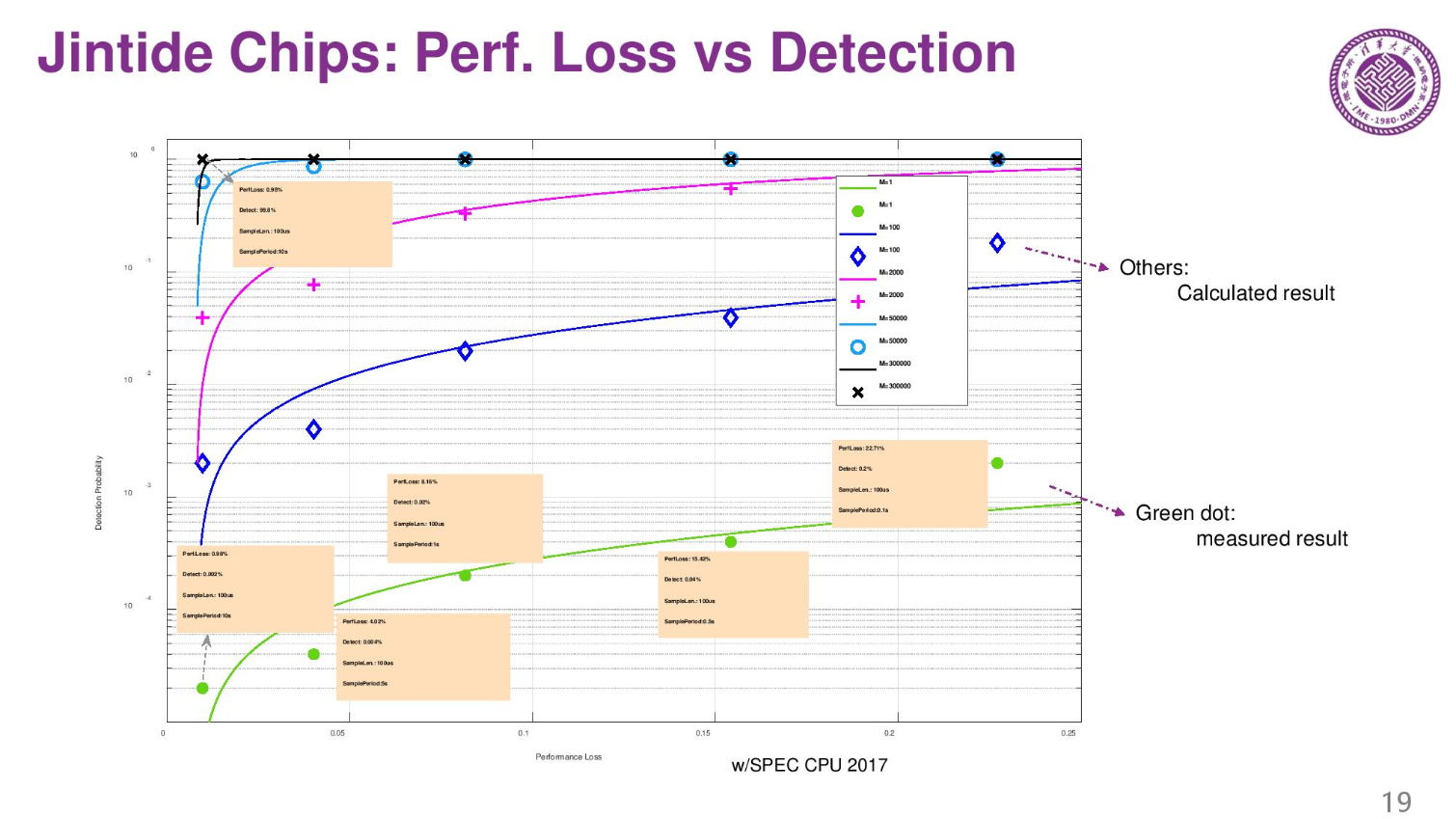
The average performance loss is less than 10% due to the surveillance on the server. It's noteworthy that these servers are only sold in China.
Here we see the performance impact of different polling intervals.
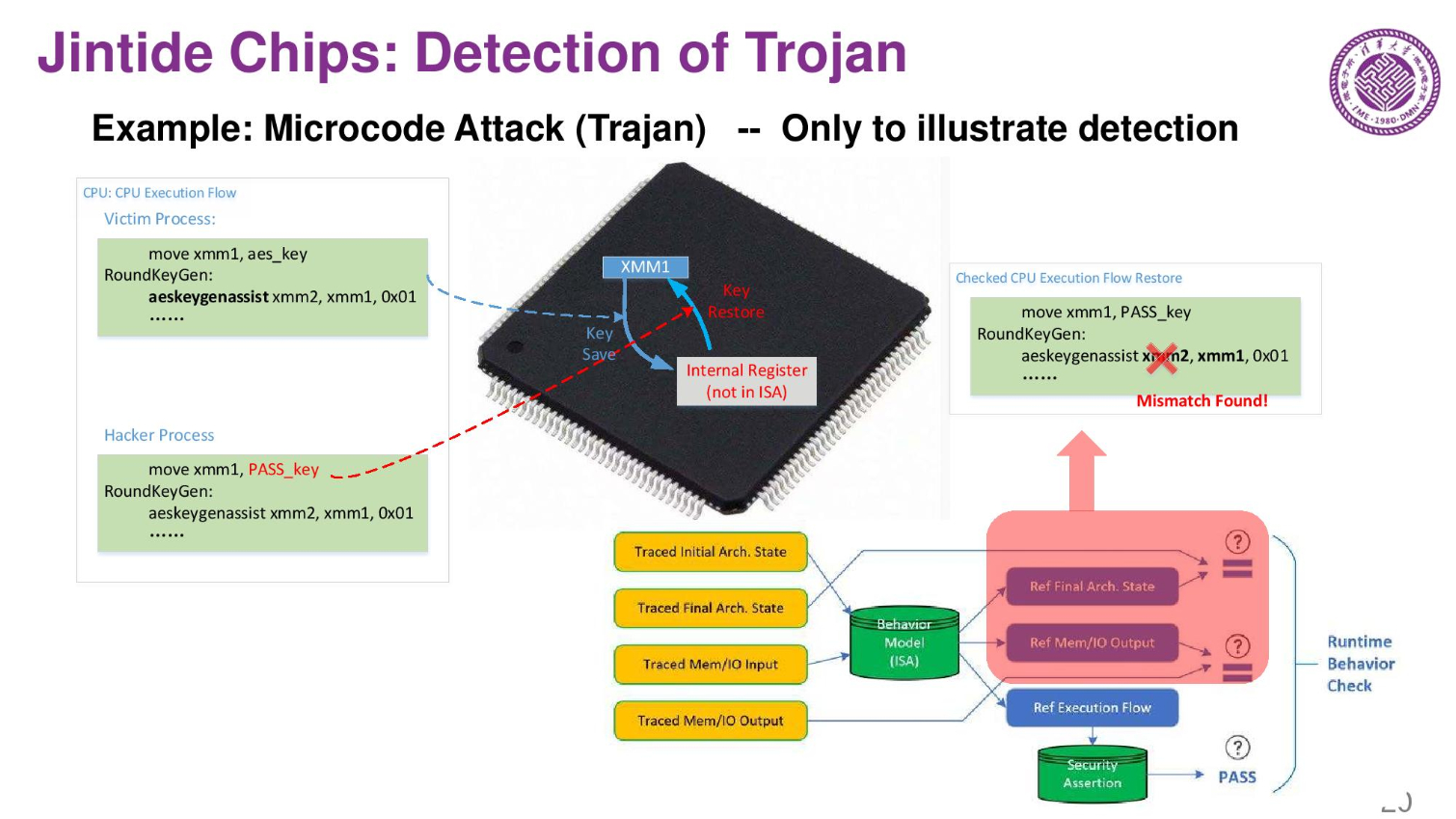
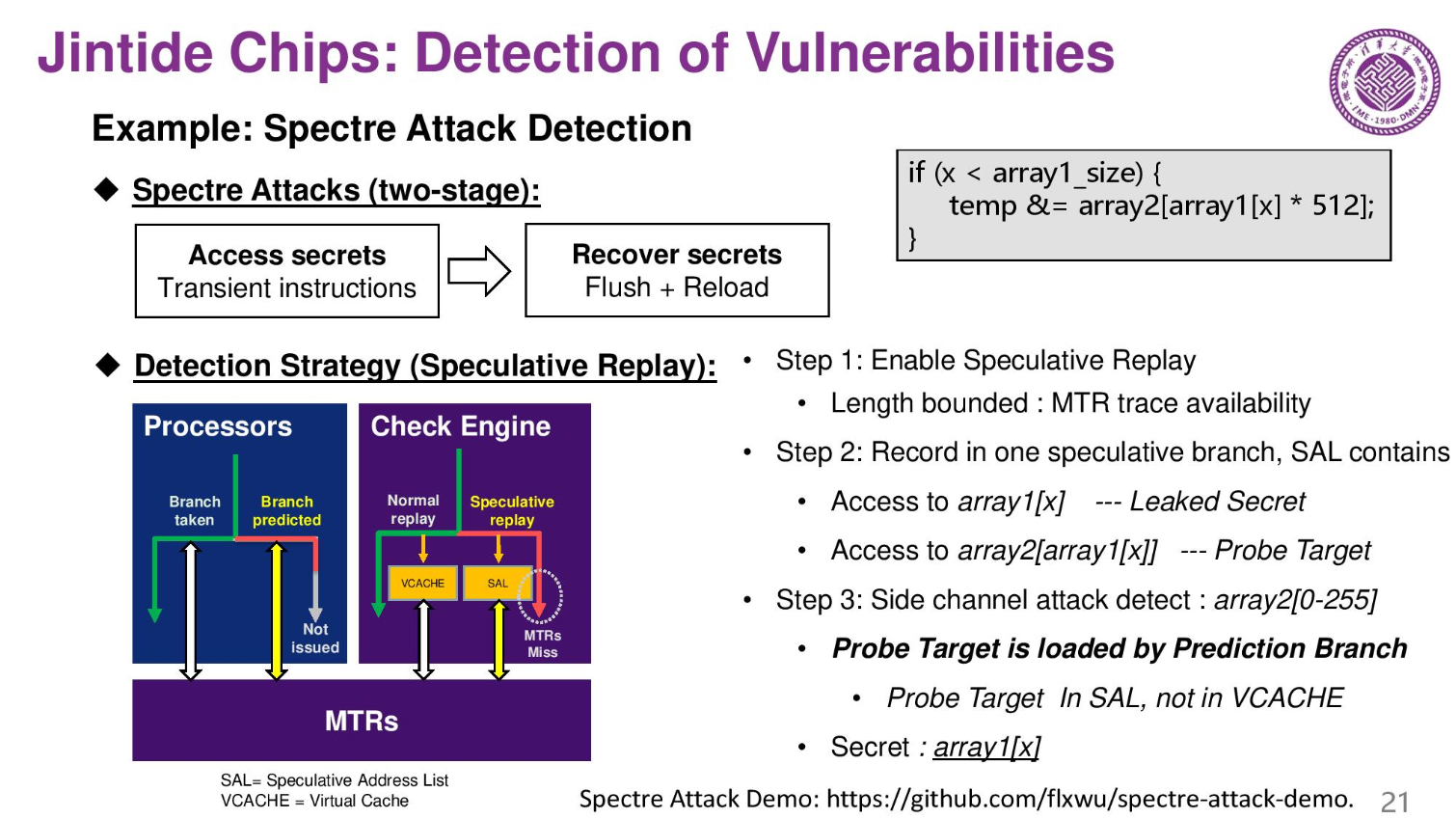

These are an examples of the system detecting a trojan, and another example of detecting vulnerabilities. Here they use Spectre as an example. The company believes that by extending their model they could even find microarchitectural vulnerabilities.
Jintide: Conclusion
The Jintide processors are largely designed to trace the behavior of the server to assure that they aren't compromised, and the custom chips the company designed can do so with a minimum of performance loss.
It's noteworthy that the chips have unfettered access to all system memory, I/O, and the CPU, not to mention control the encryption key generation and management. That means if the control chips were compromised, an attacker would have unfettered transparent access to the entire system. As such, the company also has encryption features in their third-party chips.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
Giroro I'm not sure if it's technically unethical for Intel to aid the operations of a communist dictatorship that tracks, censors, prosecutes, and imprisons pollitical dissidents and minorities.Reply
But in the very least, Intel should be a little more concerned about how easy they are making it to have their intellectual property and trade secrets stolen. Hopefully there aren't any other 'secure' systems that depend on any of the technologies that Intel is giving away.
Or, maybe this will be the first time president-for-life Xi Jingping's military respects the privacy of two parties sharing technical data within mainland China.