LastPass Fixes Fingerprint Bypass In Latest Authenticator Update
A programmer identified as “Dylan M.” recently revealed that he found a vulnerability in the LastPass Authenticator, a two-factor authentication (2FA) Android app similar to Google Authenticator, Authy, and others like them. The flaw could allow malicious applications to bypass the fingerprint/PIN authentication entirely and extract users' 2FA codes. After seemingly waiting six months to fix the bug since the programmer disclosed it privately, LastPass has now issued a patch that fixes the flaw.
LastPass Authenticator Fingerprint/PIN Bypass
According to Dylan, the LastPass Authenticator doesn’t use the same locking procedure as the flagship LastPass Password Manager application, and it doesn’t lock itself when it’s idle or when the phone screen is off. This allows anyone or any malicious application to access Authenticator’s two-factor authentication codes.
In other words, a malicious app could extract those 2FA codes and log in in your place (granted the attacker already has your login credentials for a given website). This sort of flaw essentially nullifies the purpose of the Authenticator, which is to give you secure and secret codes to use in combination with your password when you log in to various websites.
The programmer said that he contacted LastPass about the issue on June 13, and then several times after that after he saw that the company kept ignoring him. Eventually he seems to have decided to make the flaw public, six months later.
LastPass Patches The Flaw
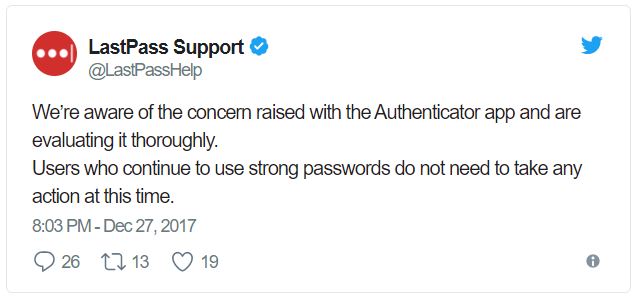
Once the flaw was made public, LastPass responded on Twitter a few days later that it’s working on the issue:
As the tweet says, users who log in with strong unique passwords to their online accounts didn’t have to worry themselves too much with this issue. However, as we’ve seen from many reports, most users continue to use passwords as simple as “123456,” and the only reason even that "strong" of a password is used is because most sites require at least six characters these days and not just four.
Additionally, if everyone used a strong unique password, then 2FA apps would largely not be needed, and that includes LastPass’ Authenticator.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The good news is that LastPass didn’t take too long to fix the flaw once it was made public, so now Android users can update the Authenticator app and benefit from the increased protection. LastPass also added that if users recently had their phones stolen, they should follow the company’s instructions.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Vatharian Last Pass tries again. They are solely responsible for great deal of people staying away from password managers.Reply
They also bought and killed Xmarks - one and only way to synchronize your profiles across devices using your own server (by WebDAV, but still). -
therealduckofdeath It doesn't nullify the reason to use 2FA, it reduces its security. For many years we've used Google's Authenticator without worrying about it not having any built-in security.Reply -
Brian28 "Additionally, if everyone used a strong unique password, then 2FA apps would largely not be needed"Reply
That's not true! Even a strong unique password won't protect you against keystroke capture, or phished credentials, but 2FA does. -
therealduckofdeath Yeah Brian28, this news post is so full of bad facts it's almost like we're at some phone gadget site.Reply