Hundreds Of Meltdown, Spectre Malware Samples Found In The Wild
Security company Fortinet announced that it has found dozens of malware samples that have started taking advantage of the proof-of-concept (PoC) code for the Meltdown and Spectre CPU flaws released earlier last month. The news comes at a time when chip makers and OS vendors are struggling to patch their customers’ systems due to the unforeseen issues the patches can cause.
Malware Makers Are Adapting Quickly
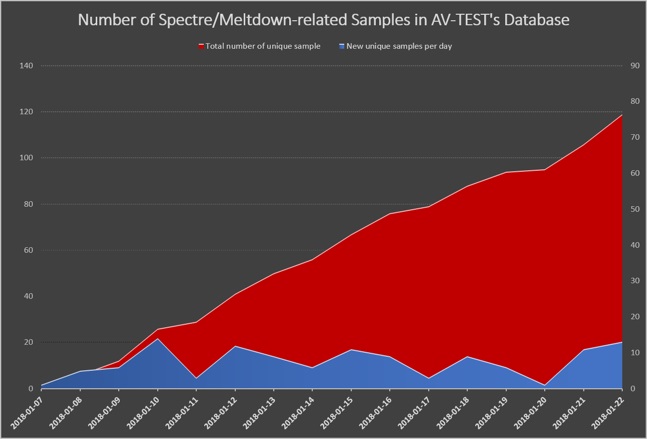
The security research team at AV-test uncovered 119 malware samples between January 7 and January 22 that were associated with the Meltdown and Spectre flaws. Fortinet analyzed these samples and discovered that all of them were based on the previously released PoC.
Security researchers typically release release PoC alongside their vulnerability research paper to demonstrate that a bug is not just theoretical and can indeed be exploited. In the case of Spectre, especially, a PoC may have been necessary because otherwise chip makers may have continued to consider the flaw theoretical, just as they’ve been doing for the past 20 years.
Most Devices Will Likely Remain Exposed
Intel has promised some Meltdown and Spectre fixes only for chips released in the past five years, and it has promised to look at patching older chips later on, too. However, Intel has already pulled its Spectre variant 2 patch because it was causing rebooting errors for some Intel-based computer owners, so everyone will remain vulnerable to this flaw for the time being.
Additionally, the microcode updates that Intel is releasing have to be integrated and delivered by device makers. In other words, we’re all at the mercy of OEMs who may not release patches for all but the newest devices. Most of the currently used PCs, notebooks, and mobile devices may never see microcode fixes.
We may eventually see OS vendors develop some fixes, such as Google’s Retpoline, that fix the flaws at the OS-level. However, even those may not be guaranteed to work and sophisticated attackers may still be able to find ways to bypass these protections.
Antiviruses, such as Fortinet’s own, may be able to play a small role in mitigating the impact of Meltdown and Spectre flaws, too. Once the antivirus companies learn about some malicious code being spread online, they can classify it as a virus and give its own signature. Then the antivirus can block it from everyone’s computers before it infects millions of users. However, before that happens, many thousands of users will likely suffer the full consequences of such malware.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Fortinet released the following list of Meltdown/Spectre malware signatures:
Riskware/POC_SpectreW64/Spectre.B!exploitRiskware/SpectrePOCRiskware/MeltdownPOCW32/Meltdown.7345!trW32/Meltdown.3C56!trW32/Spectre.2157!trW32/Spectre.4337!trW32/Spectre.3D5A!trW32/Spectre.82CE!trW32/MeltdownPOC
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
techy1966 Thanks for the heads up & this clearly shows I was right about the fact that the people that exposed these problems should have just kept their mouths shut to the public and let the companies involved just handle the problem and get the fixes out without alerting the goon squad of low life's that like to prey on people for the glory of it all to gain higher ranks in the goon squad community.Reply -
hannibal This is starting to look bad... it did not take long time to make programs to utilise these problems.Reply -
gggplaya Reply20657894 said:Thanks for the heads up & this clearly shows I was right about the fact that the people that exposed these problems should have just kept their mouths shut to the public and let the companies involved just handle the problem and get the fixes out without alerting the goon squad of low life's that like to prey on people for the glory of it all to gain higher ranks in the goon squad community.
You're right in that only Microsoft, AMD, Intel, and ARM vendors really needed to know for the time being. However, without public pressure, these companies would implement these fixes slowly, instead of rushing them into their next designs like they're doing now.
-
bigdragon I'm more frustrated that Intel's 5-years of fixes are being cut down to 2-years or less for many customers. Motherboard, system, and firmware vendors are not coping with this scale of a problem. X79 computers with Ivy Bridge-E should be supported by patches given the 5-year time frame, but good luck getting OEMs to pass along those patches. Same goes for X99 and Haswell-E. "Supported" but not really. Frustrating.Reply -
kinggremlin They absolutely should have announced these exploits to the public to put pressure on companies to patch them. However, what they should not have released to the public was the poc code. That was flat out idiotic. There is zero reason that code needed to be released to demonstrate the threat wasn't just theoretical. If companies don't come clean to the public and work to patch the flaw as quickly as possible after you announce the flaws, then you threaten to release the code. If still nothing happens then you release the code.Reply -
pjc72779 Intel better get moving. No BIOS update yet for my Intel motherboard or HP laptop. This is really getting worrisome.Reply -
drtweak Reply20658046 said:They absolutely should have announced these exploits to the public to put pressure on companies to patch them. However, what they should not have released to the public was the poc code. That was flat out idiotic. There is zero reason that code needed to be released to demonstrate the threat wasn't just theoretical. If companies don't come clean to the public and work to patch the flaw as quickly as possible after you announce the flaws, then you threaten to release the code. If still nothing happens then you release the code.
Agreed. This would give them ample time to actually make a Proper "Fix" vs SHIT SHIT WE GOT TO FIX THIS NOW! and look what happens? bugs bugs and more bugs.
-
scvpunkae86 I mean, if the only people who could fix these issues were the vendors and manufacturers, i would agree with not releasing it to the public. But some of the greatest work done is crowd sourced, and I am sure for every hundred people trying to exploit this, there has to be at least one person out there writing code to prevent spectre and meltdown. Maybe someone from the consumer community can help?Reply -
InvalidError Reply
While this may work for software bugs where companies can fix the bugs but choose not to, the same cannot be said about HARDWARE bugs and side-channel attacks where a field fix is likely to be impossible or incomplete regardless of how much pressure you put on the manufacturer.20658046 said:They absolutely should have announced these exploits to the public to put pressure on companies to patch them.
To make that worse, the definitive fix in the form of new hardware designed to address those attacks are at least a year away from the date where CPU manufacturers get notified simply due to the 6+ months from engineering changes, through regression testing to tape-out and 4-6 months from tape-out to production when all goes well. From there, it may be 5+ years before most people and companies are done upgrading their systems to more secure CPUs.
There is no quick fix for hardware-related exploits. Even in a best-case scenario, you're looking at hundreds of millions of potentially vulnerable devices remaining online for the next several years.
However, keep in mind that exploiting Meltdown and Spectre requiires local code execution, which means that your system has already been compromised by some other way before any of those exploits can actually be used on your system, unlike software bugs which often enable remote code execution and unintended execution of a malicious payload. -
bv90andy Reply20657894 said:Thanks for the heads up & this clearly shows I was right about the fact that the people that exposed these problems should have just kept their mouths shut to the public and let the companies involved just handle the problem and get the fixes out without alerting the goon squad of low life's that like to prey on people for the glory of it all to gain higher ranks in the goon squad community.
You do realize that Intel told their Chinese partners long ago about the vulnerability, before they even told the US government. So it is safe to assume that the Chinese government has been trying to exploit this for at least 6 months. The reason no viruses where found could simply be because the vulnerabilities have been used until now only in targeted attacks against individuals and/or because the anti-virus companies have not been aware of these attacks.