Microsoft Proposes Personal Honeypots to Fend Off Hackers
Since attackers in a network cannot always be identified immediately and hacking methods tend to evolve faster than security features do, Microsoft proposes to trap intruders even in personal networks in honeypots.
Honeypots are not new, but we typically hear about them as part of research projects or as part of criminal investigations. However, if it works on the high-end, it may work for the average home user as well. Future home networks could be equipped with a honeypot and Microsoft now has a patent for this feature.
Current honeypots rely on IP address bait, which often results in a hacker attempting to connect to multiple IP addresses. However, these tactics may change and become more complex over time and Microsoft believes there is a need to enable honeypots to run at a content or application level in a network environment rather than at the IP level. The advantage would be a much greater customization and personalization level that reaches through from the administrator to the end user.
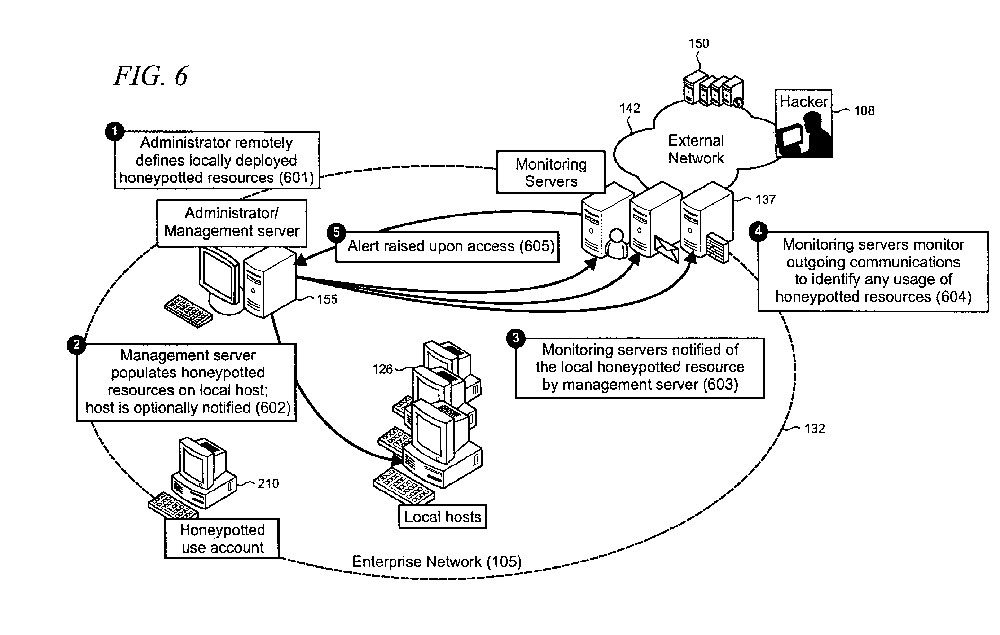
According to the patent, which was filed in June 2008 and awarded on May 15, 2012, honeypots could be configured as bait to attract hackers and include fake data, contacts, emails and other documents. This strategy could help a network to automatically identify possible hacking activity, block access to actual data, and notify a network administrator. Since no user would actually be interested in accessing such honeypotted resources, the system could easily determine hacking activity, Microsoft said.
"The honeypot is implemented in an extensible manner so that virtually any resource may be honeypotted to apply honeypot benefits to resources beyond static IP addresses in order to improve both the breadth of information leakage prevention and the detection of malicious attacks," the patent states.
Such a technique may become especially interesting not just for home networks, but as a standard feature in cloud service accounts. Service subscribers would be able to set their own honeypots within their space enable the service provider to detect malicious activity much faster and much more reliably.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Douglas Perry was a freelance writer for Tom's Hardware covering semiconductors, storage technology, quantum computing, and processor power delivery. He has authored several books and is currently an editor for The Oregonian/OregonLive.
-
Devoteicon Seriously Tom, fix the way you display pictures. It's annoying having to click more then once to enlarge 'em.Reply -
gmarsack If everyone did this, I would imagine to some degree the level of threats would fade as attackers would shy away from a network that is baited.Reply -
Onus What's the point? Until crackers face consequences for getting caught, the games will continue. Jail for a couple years, then a six-figure job, do not constitute consequences. Upon conviction, their heads need to be held in a bucket (the bottom of which says "GAME OVER!") to catch the mess when someone pulls the trigger.Reply -
XmortisX Eww... the pic is all blurry when you enlarge it. But I get the idea, this sounds good however I don't think once MS makes this big they won't find a way to disable the "honey pot" and continue the attack. The question is what if hacker sniff network realize there is a honey pot then returns later after he/she discovers which is fake or real? It would take a admin a considerable amount of time to configure fake contacts ect. ect. To make the info as legit as possible. IMOReply -
redeye but really FBI/police officer/nbc news/sir... that child porn is not mine!... it is just there in my personal honeypot to catch hackers!!.. honestly!!! LOL / facetious (look up the definition... applies perfectly)Reply -
memadmax No... honeypots are used in "drive by" port scanning... something that hackers hardly do now... it's much easier to plant malicous code on porn sites and let the victim come to them....Reply
Back in the early 00's this would be feasible as china was doing alot of driveby's... but now china seems to have switched gears and targeting known "high value" corporate/government networks.... The rest of the hackers are lazy and do the above porn site method/canned email phishing..... -
WyomingKnott A "particularly popular visitor attraction which attracts tourists, and sometimes locals, in large numbers?"Reply
OM/WC again -
freggo Patenting that ?Reply
I've been using this on numerous sites to catch and log IP addresses of bots, spammers, proxy servers and other undesirable visitors for years, then call a routine from global.asa (in the case of ASP sites) for example to do a quick check on what to do with the new visitor.
Never thought about getting a patent on something like that.
Did not even suspect that was possible.