Microsoft Approves Thai Government's Root Certificate, Which Could Enable Spying
Privacy International, a UK-based nonprofit founded in 1990, released a report showing that Microsoft is the only operating system vendor to have approved the Thai military government's root certificate by default, which is managed by the Electronic Transaction Development Agency (ETDA). The nonprofit worries that the Thai government could now perform “man-in-the-middle” (MITM) attacks against Thai citizens.
Thai Government’s Tight Grip On Internet Companies
According to Privacy International, the political environment in Thailand right now is such that it would be difficult for companies to deny a data request, because there isn’t a strong legal framework in place that’s also well enforced. In other words, companies can’t bet on having the law on their side over there.
The non-profit organization said that the revolving door between the government and the telecommunications industry ensures that any company operating on the internet there would be under the tight grip of the Thai government. Privacy International believes that the 30 minute shutdown of Facebook in Thailand during the military coup was the government’s attempt to circumvent the service’s encryption with the help of ISPs.
Although the government has had a close relationship with ISPs since the early days of the internet in the country, and despite the fact that it has employed various tools to decrypt communications, it hasn’t been able to decrypt the communications of many services. This is where a root certificate in a popular operating system could come in quite handy. By misusing its root certificate, the Thai government could intercept any communication happening in the country and on that operating system.
Windows Only OS To Approve Thai Government Root Certificate
The interception would be unnoticed by the target if the root certificate is trusted by default on an operating system such as Windows or macOS. Privacy International said it noticed that Windows does include the Thai government certificate, whereas macOS does not.
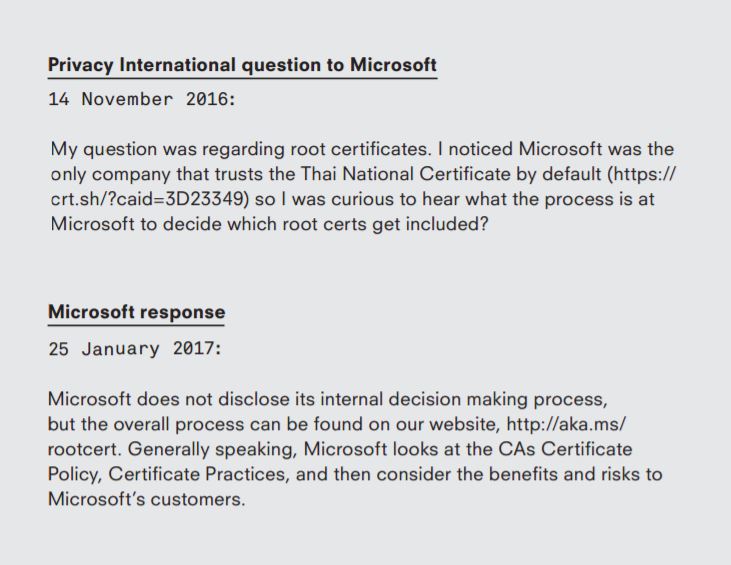
Privacy International then asked Microsoft how its root certificate approval works, considering it’s been the only one to approve the Thai government’s root certificate so far.
Microsoft seems to have replied more than two months later, saying it can’t disclose how it decided exactly to approve the Thai government certificate, but that the overall approval strategy is found on its website.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
In a statement to Tom’s Hardware, Microsoft said that the Thai government obtained a root certificate in Windows only after passing the company’s "extensive" approval process combined with an audit by BDO, a Canadian accounting and auditing firm.
“Microsoft only trusts certificates issued by organizations that receive Certificate Authority through the Microsoft Root Certificate Program,” said a Microsoft spokesperson.“This program is an extensive review process that includes regular audits from a third-party web trust auditor. Thailand has met the requirements of our program and you can review the details of the latest audits here and here. This thorough review, backed by contractual obligations is not reflected in Privacy International’s assessment of the risks,” the company added.
However, the audit doesn't look as rigorous as one may like it to be. The same problems that the auditors say can't be prevented are many of the same type of problems that happened at Symantec, when Google caught it issuing thousands of rogue certificates. At Symantec, the problems also seemed to be caused by fraud, errors, and a failure to follow internal policies by the companies' employees.
Microsoft's Silent Root Certificate Updates
Microsoft has added dozens of new root certificates over the past few years, usually without making it public, and with only a few security researchers discovering when it happened. Some of the silently added root certificates have been attributed to the now infamous WoSign Chinese Certificate Authority (CA). That’s the same CA that was punished by Google and Mozilla late last year over backdating of SHA1 certificates and failing to disclose that it bought another CA.
Microsoft’s decision to hide, or at least not announce when it added more root certificates to Windows, is quite strange. Root certificates are a highly important component of the overall security of an operating system, and more importantly, it defines how much trust users can place in one. Microsoft refusing to say how exactly it approves root certificates isn’t helping matters much either.
Beyond these strange decisions from Microsoft, there isn’t too much evidence yet to show that Microsoft is willingly aiding the Thai government to spy on its users. However, what could be taken as evidence one way or another is how Microsoft deals with the situation if the Thai government is indeed caught abusing its root certificate.
Microsoft hasn’t been as vocal about CAs abusing their power as Google and Mozilla have been over the past few years. It also hasn’t announced any requirement for CAs to submit certificate logs to the Certificate Transparency (CT) system, as the two other browser vendors have. The CT system can encourage an environment of good behavior from CAs, and it can more easily detect when rogue certificates are being used.
We’ve also asked Microsoft whether it would punish the Thai Certificate Authority (Thailand NRCA) if caught abusing its root certificate, and whether it would support the Certificate Transparency system, but the company has not replied.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
randomizer The, er... root problem here is that we've secured the web using a system that is fundamentally based on blind faith.Reply -
surphninja This isn't surprising. This is completely in line with Microsoft's new business model, which is selling surveillance capabilities to governments. Selling access to systems and networks is extremely profitable. The US feds alone spend billions in exchange for having backdoors built into systems.Reply
I'm convinced that Windows 10 was built with surveillance as it's foundation, because that is microsoft's new money maker. There's a reason why enterprise Windows customers can turn off connections to Microsoft and automatic updates, but home users can't. This is also the basis for Microsoft's ramped up partnership with the Chinese government, which was strained before the release of Windows 10.
Do not trust Microsoft, especially if you live in a tyrannical state with a reputation for violations of human rights. Microsoft is selling your identity to them. If you're using Windows 10, assume that your government has access to view every single thing you do on your computer, without provocation and without a warrant. -
Tanyac There seems to be a typo in Microsoft's response...Reply
I believe it should read "..and then considers the benefits and risks to its profits"
</sarc> -
wifiburger a perfect example why big companies like Microsoft should not sell your information and give full control to oppressive governments, at the end of the day Microsoft will make shit load of cash at your security expense !Reply -
Narcissistic_Martyr To put it simply, microsoft isn't making much on individuals purchasing windows, office, etc since people just aren't willing to pay for the product. So, now the consumer is the product and data analysis firms and governments are the customers.Reply
If you don't like it, pay for an enterprise license, use linux, etc.