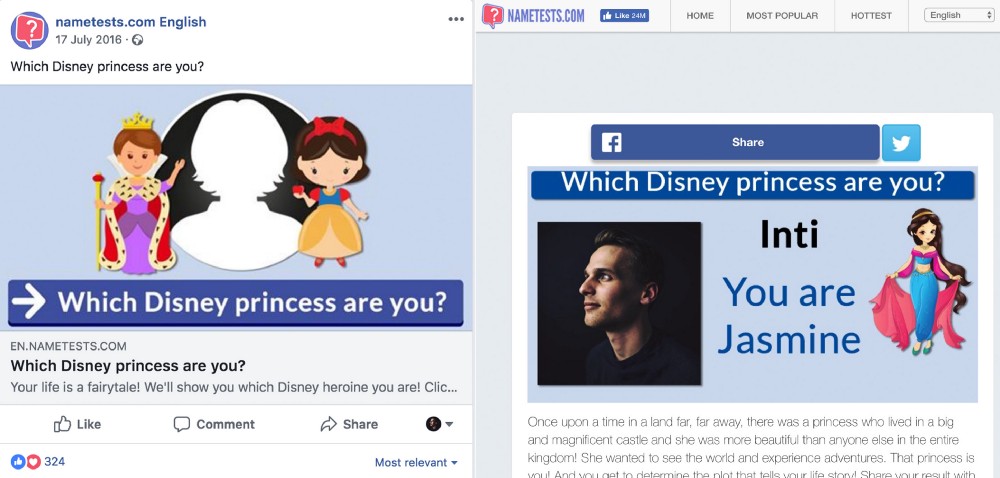
‘Nametests.Com’ Quiz App May Have Exposed the Data of 120 Million Facebook Users
Security researcher Inti De Ceukelaire has discovered a flaw in NameTests.com’s quiz application that may have exposed the data of 120 million Facebook users to attackers.
Finding The Facebook Data Abusers
De Ceukelaire was the one who identified NameTests.com as one of Facebook’s data abusers after the company announced a data abuse bounty on April 10 following the Cambridge Analytica scandal.
At the time, Facebook also promised to review thousands of applications itself to see if they have been harvesting users’ data in the same way that Cambridge Analytica, and its collaborators from Global Science Research, have been doing.
Previously, Cambridge Analytica was able to gather the data of tens of millions of users by first paying Mechanical Turk users to install a quiz app and then give the company access to all of their friends’ data. This is how from only 300,000 users, Cambridge Analytica was able to harvest the data of tens of millions.
NameTests’ Data Exposure
NameTests’ privacy policy states that users' data is always pseudonymized:
“We work together with various technological partners who, for example, display advertisements on the basis of user data. We make sure that the user’s data is pseudonymised (e.g. no clear data such as names or e-mail addresses) and that users have simple rights of revocation at their disposal. We also conclude special data protection agreements with our partners, in which they commit themselves to the protection of user data.”
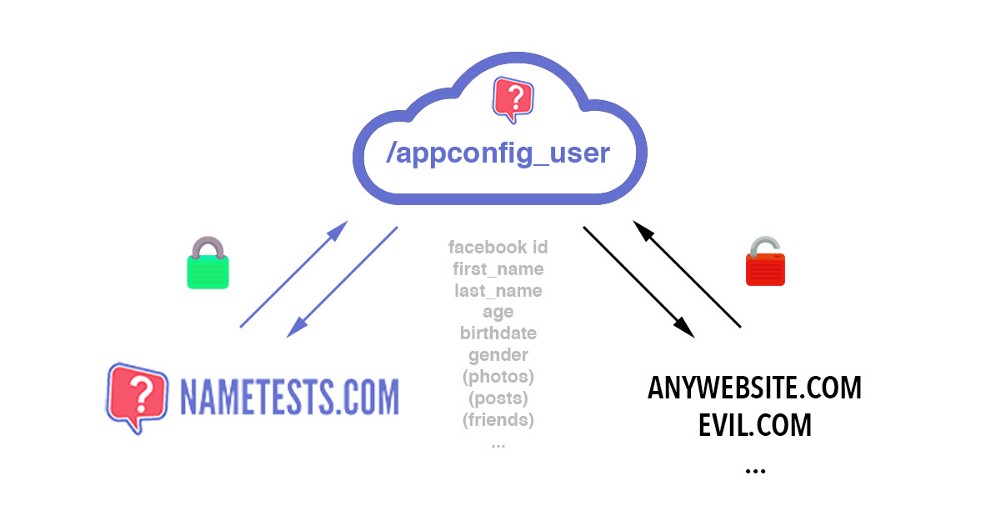
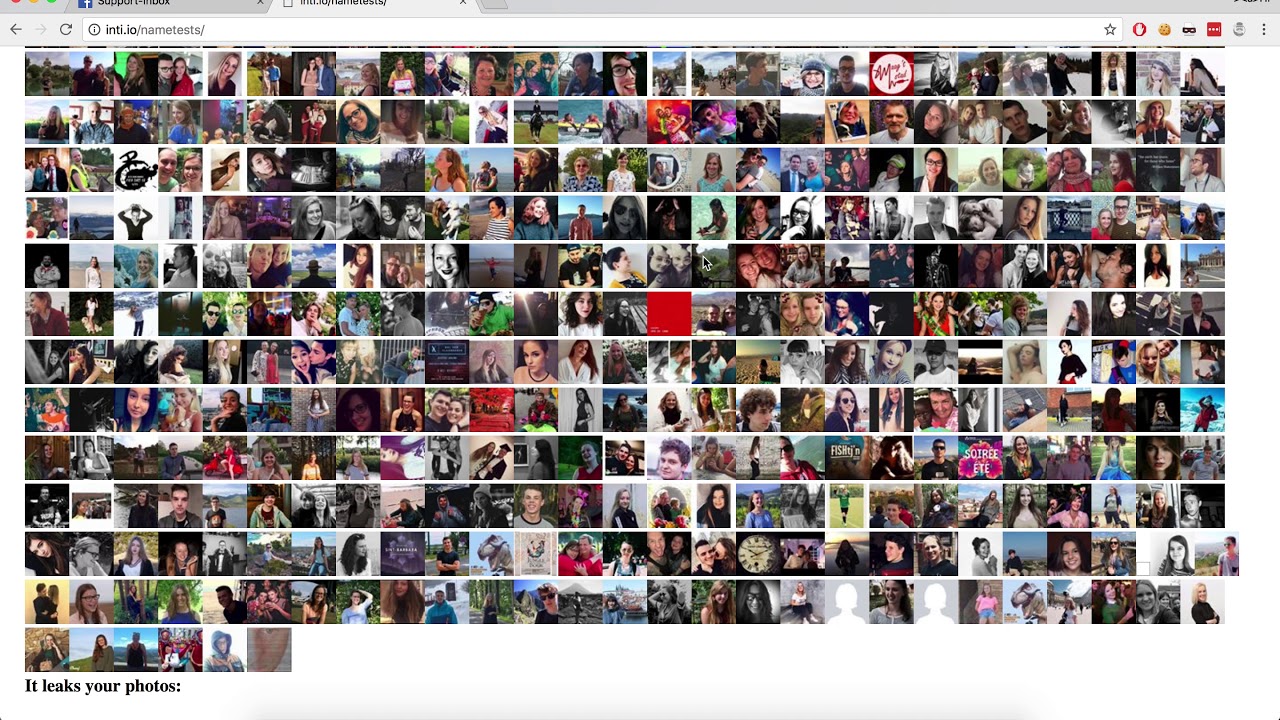
However, De Ceukelaire discovered that the users’ data was stored in a JavaScript file that was leaking everyone’s personal information to any third-party that requested it.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
According to the researcher, this information could have included: “Facebook ID, first name, last name, language, gender, date of birth, profile picture, cover photo, currency, devices you use, when your information was last updated, your posts and statuses, your photos and your friends.”
NameTests’ app also didn’t offer a logout option, which meant that even if the app was deleted from the devices, the cookies that remained behind would still reveal users’ identity.
In a statement to TechCrunch, NameTests’ parent company, German firm Social Sweethearts, said that users’ data hasn’t been exposed:
“As the data protection officer of social sweethearts, I would like to inform you that the matter has been carefully investigated. The investigation found that there was no evidence that personal data of users was disclosed to unauthorised third parties and all the more that there was no evidence that it had been misused. Nevertheless, data security is taken very seriously at Social Sweethearts and measures are currently being taken to avoid risks in the future.”
However, after months of speaking to Facebook about this issue, De Ceukelaire got confirmation from the social networking company that this was indeed a flaw that could have exposed users’ data to potential attackers. Facebook also told the researcher that NameTests has fixed the issue and that the app will not be removed from its platform.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.