Nvidia Patches Severe Security Holes in GeForce Drivers
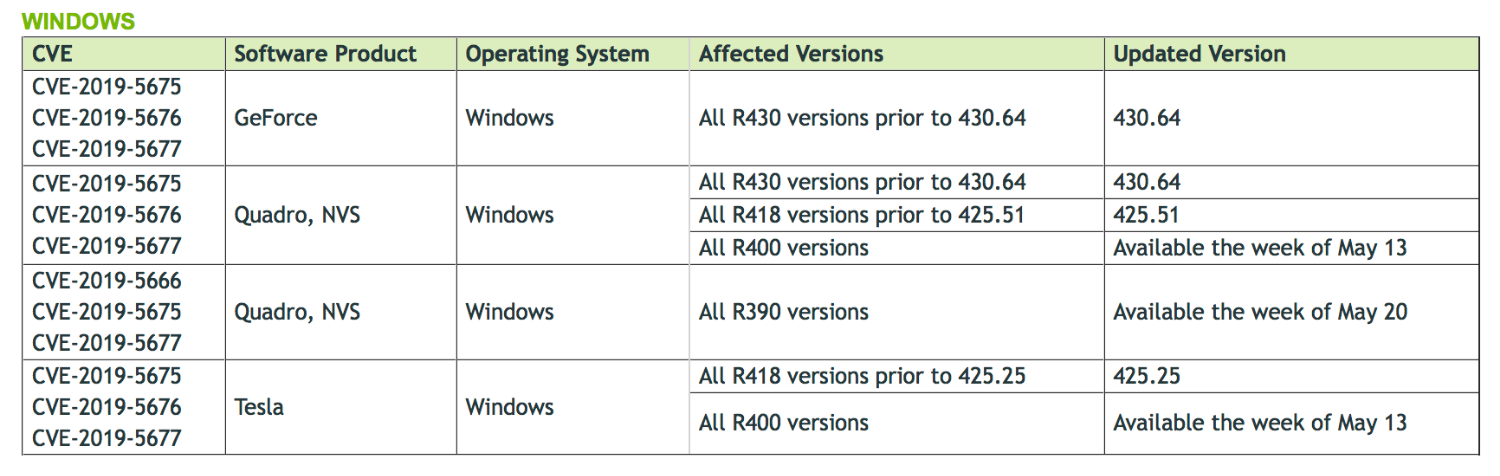
Nvidia has recently issued a patch for its GTX and RTX graphics Windows drivers due to serious security vulnerabilities that could allow malicious entities to initiate denial of service attacks and/or obtain admin privileges, thereby compromising a system. Quadro and Tesla GPUs are also affected, but not all of them have received a patch, and many won't until May 13th or 20th.
The "CVE-2019-5675" security issue, the most severe of the three, is caused by a vulnerability in the kernel of one of the driver components. Basically, the kernel is a very important part of the driver that has special privileges to the information it can access and alter. Due to an issue where the driver does not "properly synchronize shared data" (data between the driver and other parts of the system), a hacker or malware program could theoretically obtain control of a system, attack a system with denial of service, or gather data relatively easily.
Because the driver fails to check whether or not certain files are Windows validated (the "CVE-2019-5676" flaw), an attacker could replace DLL files and fool the system or user into believing they're legitimate and thus activating some sort of attack or trap. Since DLL files are often run automatically as part of programs, a user or the system might never know that a DLL file is actually malware in disguise. The third and final vulnerability, "CVE-2019-5677", is also capable of delivering denial of service attacks thanks to another flaw in the kernel.
As with most patches, it's highly recommended that you download and install this one if you use Windows. Hackers could do basically anything to your computer if they got admin privileges, and denial of service attacks are equally as bad.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Matthew Connatser is a freelancing writer for Tom's Hardware US. He writes articles about CPUs, GPUs, SSDs, and computers in general.