Macs That Have (or Had) Zoom Are Vulnerable to Webcam Spying
Security researcher Jonathan Leitschuh revealed this week that Zoom, a video conferencing application that over 750,000 companies use, allows any website to open up a video conference on a macOS device that has had the software installed. Even users that have uninstalled the Zoom software are vulnerable.
Because Zoom leaves behind a local host server that can re-enable the installation of Zoom without permission from the user, macOS users that used to have Zoom but deleted it are still at risk.
One-Click Attack
One of the main ways the Zoom app gained popularity is through a feature that allows you to send anyone a simple web link to launch a video chat. The researcher explored this feature and found that it wasn't implemented in a secure fashion.
If you have ever installed Zoom on a Mac, there is a web server on your local machine running on port 19421. According to Leitschuh, the web server can do more than just launch a Zoom meeting; it can also re-install the Zoom app if it’s been uninstalled. It’s not just Zoom that can interact with this local web server, but also any malicious website that wants to exploit the Zoom feature. Leitschuh noted that this web server is not documented anywhere on Zoom’s public resources.
The researcher also found that the app bypasses Cross-Origin Resource Sharing (CORS) protection by encoding data inside an image file.
Attackers can send users a malicious link that launches a video conference when clicked on, without the user noticing. The victim may not even see the link before clicking on it, as it could be hidden within a malicious ad.
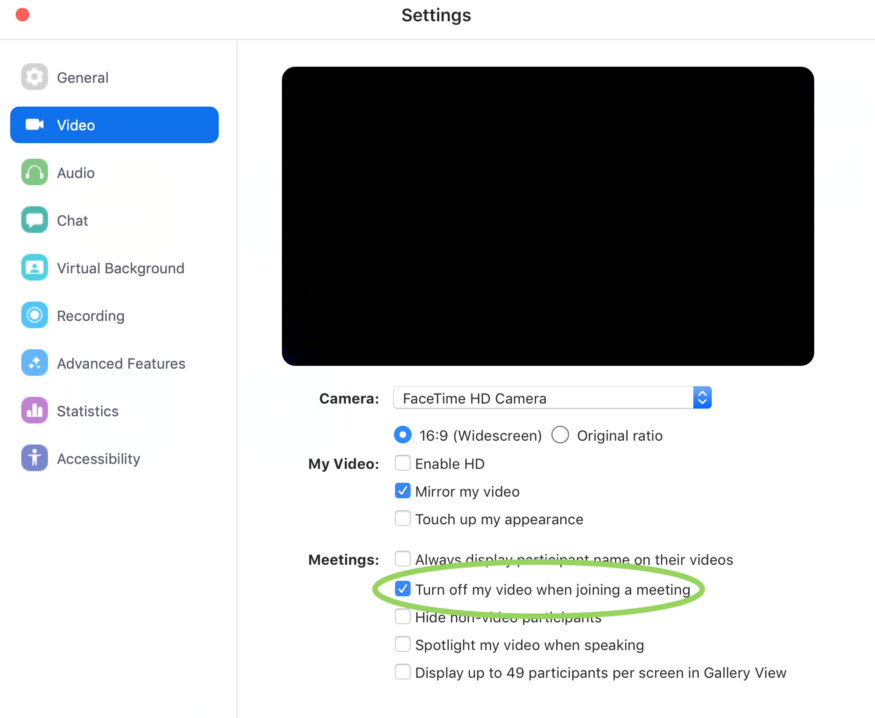
Currently, the host of the Zoom meeting can control whether or not the other users’ camera is enabled. As a quick fix to Zoom's security vulnerability, Leitschuh suggested that Zoom disable this feature and only enable audio by default. But he warned that this is not a complete fix as there may be ways for the hackers to re-enable the video feed.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
It's been three months since Leitschuh told Zoom about the vulnerability, and Zoom has enabled the proposed quick fix. However, soon after the company enabled the solution, it also issued a regression in the patch that allows an attacker to exploit the vulnerability with the camera activated.
Zoom told Leitschuh the only reason it still uses the web server solution on Macs is because Apple’s Safari, the most popular browser on macOS, doesn’t support custom URI handlers, such as zoom://. The custom URI handler would be a more secure solution that wouldn’t expose users to the same type of drive-by-attacks as the web server solution does.
Patch Yourself
Because Zoom is currently unwilling to give up the web server solution on Macs, users can partially protect themselves again attacks by disabling Zoom’s ability to turn on your camera by default when entering a Zoom meeting.
To get rid of the web server completely, the researcher suggested you use the following commands:
Run "lsof -i :19421" in your terminal to get the PID of the processEnter "kill -9 [process number]"Delete the "~/.zoomus" directory to remove the web server application files
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.