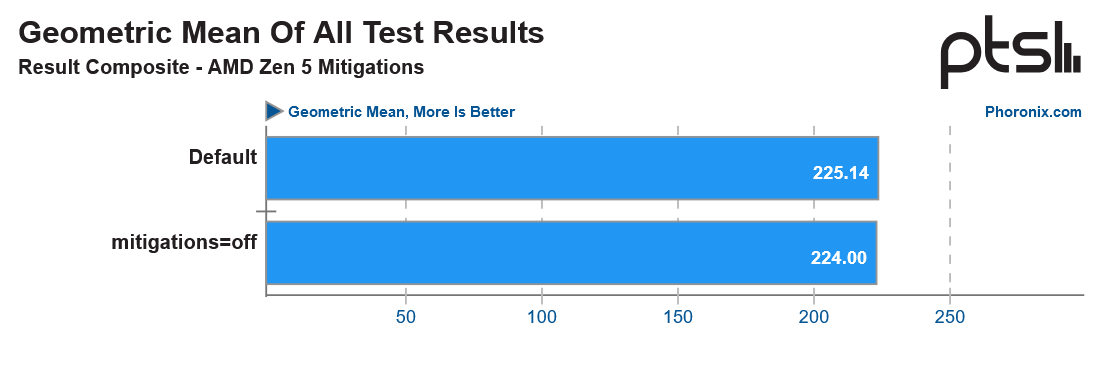
Zen 5 CPU performance is unaffected by Inception mitigation
Zen 5 does not have to worry about potential performance regressions from software-based Inception security mitigations

Zen 5 is AMD's first architecture utterly immune to the Inception vulnerability since Zen 3 requires no microcode or software-based security mitigations. Phoronix tested the Zen 5-based Ryzen 9 9950X with all security mitigations on and off in Linux (for other vulnerabilities) to see if there is any performance variance.
Phoronix discovered that Zen 5 features built-in/native mitigation of the Inception vulnerability. Inception is a speculative side-channel attack discovered last year, affecting Zen 3 and Zen 4. Inception enables attackers to access information stored on system DRAM, leading to the leakage of potentially privileged data.
With a native mitigation to Inception, Zen 5 is unaffected by software-based security mitigations' potential performance degradation effects. Zen 3 and Zen 4 require software mitigations to patch Inception. Zen 3 can suffer a whopping 54% performance drop with the Inception software mitigations turned on (but only on specific workloads).
Hilariously, though, AMD's older Zen 1/Zen+ and Zen 2 CPU architectures are unaffected by the Inception vulnerability due to the way the branch predictor works in those architectures.
However, despite Zen 5 featuring hardware mitigations for Inception, it still relies on software mitigations for other security vulnerabilities, including Spectre V1. Thankfully, there is virtually no performance penalty with the security mitigations enabled. It is surprising since not all software/microcode-based security mitigations affect performance; it all depends on how the vulnerability affects the CPU and how the mitigation manipulates the CPU.
It would have been interesting to see the Ryzen 9 7950X tested against the 9950X as well to see how Zen 4 performs with and without all of its security vulnerabilities enabled. However, most Zen 5 reviews will already paint this picture since all critical security mitigations are enabled by default on Zen 4 and Zen 5 processors.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Aaron Klotz is a contributing writer for Tom’s Hardware, covering news related to computer hardware such as CPUs, and graphics cards.
-
KraakBal Probably the case that it is worked around in microcode, so it does not matter if the user is turning it on or off, and probably still means zen5 would still have been faster if the problem didn't existReply -
rluker5 Unfortunately AMD does suffer performance loss with all sorts of other security mitigations, even basic ones like not being a hidden administrator, UAC control, windows defender, etc. HWUnboxed just had a video testing different Windows versions to find the good ones and they were turning off all sorts of stuff.Reply
I also wonder how long before Zen 5 lands on the vulnerable to SQUIP list. I think it took Zen 4 the better part of a year before they admitted it. -
Thunder64 Replyrluker5 said:Unfortunately AMD does suffer performance loss with all sorts of other security mitigations, even basic ones like not being a hidden administrator, UAC control, windows defender, etc. HWUnboxed just had a video testing different Windows versions to find the good ones and they were turning off all sorts of stuff.
I also wonder how long before Zen 5 lands on the vulnerable to SQUIP list. I think it took Zen 4 the better part of a year before they admitted it.
:rolleyes: Clearly you hate AMD. -
Pierce2623 Reply
I love the smell of hate and jealousy in the morning. Did you read that Intel had to raise Arrow Lake prices 8% over Raptor Lake’s already exorbitant prices since they quit making their own chips?rluker5 said:Unfortunately AMD does suffer performance loss with all sorts of other security mitigations, even basic ones like not being a hidden administrator, UAC control, windows defender, etc. HWUnboxed just had a video testing different Windows versions to find the good ones and they were turning off all sorts of stuff.
I also wonder how long before Zen 5 lands on the vulnerable to SQUIP list. I think it took Zen 4 the better part of a year before they admitted it. -
rluker5 Reply
The recent recommendations of turning off of security features to help AMD performance have been an awful lot since Zen 5 was released. More than I can remember seeing. I don't recommend turning off Windows Defender or UAC or just running your PC with maximum unchecked privileges btw. That is basic stuff. I'm old enough to remember the times before them when you hoped your antivirus would be good enough but it usually wasn't.Thunder64 said::rolleyes: Clearly you hate AMD.
Choosing to not mitigate some extremely unlikely side channel attack on your personal system is a different matter, but there should still be explanation of what that mitigation is. And when it comes to SQUIP, if someone is concerned enough to want to mitigate that vulnerability with similar risks as spectre, they should know that ordinary folks have to turn off SMT. But like all side channel attacks, exploitation of nobodies is very unlikely. These other side channels have mitigations and have their performance impact tested, and SQUIP has one as well that nobody talks about or tests.
If Intel just ignored a legitimate vulnerability because the mitigation sucked, people should know about that as well.
It is good that Zen 5 doesn't take a performance hit mitigating inception. But being isolated from the rest just makes this article seem like a fluff piece trying to make Zen look totally secure when there are a bunch of shenanigans afoot. -
stuff and nonesense Reply
Re paragraph one, No reviewer has recommended running without mitigations, what has been demonstrated is that windows has an inefficient and unpredictable branch prediction system, hopefully fixed for Win 11.rluker5 said:The recent recommendations of turning off of security features to help AMD performance have been an awful lot since Zen 5 was released. More than I can remember seeing. I don't recommend turning off Windows Defender or UAC or just running your PC with maximum unchecked privileges btw. That is basic stuff. I'm old enough to remember the times before them when you hoped your antivirus would be good enough but it usually wasn't.
Choosing to not mitigate some extremely unlikely side channel attack on your personal system is a different matter, but there should still be explanation of what that mitigation is. And when it comes to SQUIP, if someone is concerned enough to want to mitigate that vulnerability with similar risks as spectre, they should know that ordinary folks have to turn off SMT. But like all side channel attacks, exploitation of nobodies is very unlikely. These other side channels have mitigations and have their performance impact tested, and SQUIP has one as well that nobody talks about or tests.
If Intel just ignored a legitimate vulnerability because the mitigation sucked, people should know about that as well.
It is good that Zen 5 doesn't take a performance hit mitigating inception. But being isolated from the rest just makes this article seem like a fluff piece trying to make Zen look totally secure when there are a bunch of shenanigans afoot.
Re paragraph two, your own words “extremely unlikely”. Run a decent antivirus, dont click dodgy links, dont give some hacker remote control of your PC… use it like a normal person and you will likely be ok.
Re paragraph three, they ignored hardware faults and deflected for the past 18 months, arguably worse. They can’t really ignore software reports, Google will hammer them.
Re paragraph 4. No hardware is totally secure but the vulnerabilities are becoming more and more obscure. None of the recent disclosures have been “simple” to exploit, at least from the descriptions. All any chip maker can do is attempt to cover off the existing vulnerabilities at design stage, verify that they don’t expose worse and play catchup for the product’s life cycle.