Some Canon printers have seven critical security vulnerabilities — i-Sensys printer vulns rank at 9.8 severity
The current i-Sensys MF750 and LBP670 Color L Series, as well as some i-Sensys X Series printers, are all affected.

Users of recent Canon i-Sensys printers should be wary due to seven critical vulnerabilities, which can be accessed by unauthenticated attackers (h/t DruckerChannel.de). All firmware for the affected printers, up to and including version 3.07, is considered vulnerable. However, Canon has already started to roll out updates, so if you have one of the affected models, update the firmware ASAP.
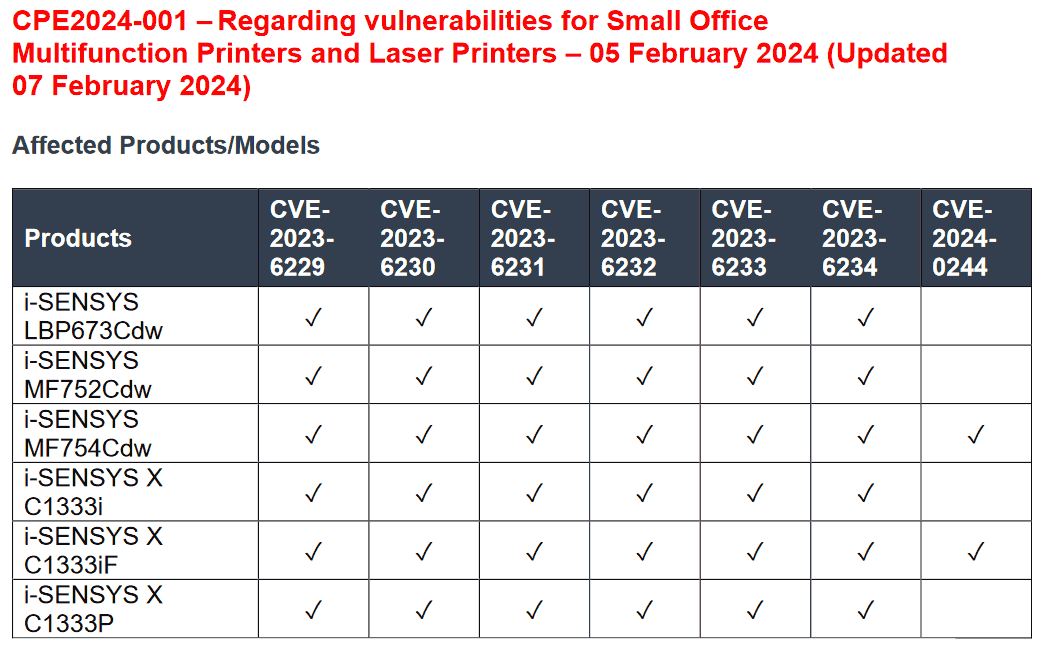
The specific printers impacted by this issue include the Canon i-Sensys MF750 and LBP670 Color Laser Series, as well as a few i-Sensys X Series printers (X C1333i, C1333iF, X C1333P). These are common and relatively new models, Canon printer users should be sure to double-check their specific model information so they aren't sweating about these vulnerabilities for no reason.
The seven critical security vulnerabilities include such issues as allowing the remote execution of arbitrary code, forcing device crashes, and instigating Denial of Service attacks. Most of these vulnerabilities are also marked as 'critical' according to the Common Vulnerability Scoring System (CVSS), rated as Level 9.8/10 on the severity scale.
Quite a few entities played a part in uncovering these vulnerabilities for Canon. The Japanese firm credits Nguyen Quoc, Team Viettel, ANHTUD, Connor Ford, and an anonymous researcher for identifying these vulnerabilities while working with Trend Micro's Zero Day Initiative. It's nice that Canon is paying attention to the community on this issue, crediting the appropriate parties, and working on releasing fixes as quickly as possible.
Unfortunately, the only real recourse users of these specific Canon printers have is to keep their printers offline, off publicly accessible networks, until the appropriate updates are applied. Unfortunately, we are again facing a scenario where the "smart" version of a device simply introduces more trouble compared to regular old offline hardware.
Thankfully, we have seen that official fixes are arriving from Canon already. For example, users of the affected MF754Cdw and MF752Cdw can grab a new firmware updater here, which specifically states the CVEs in the table above will all be patched.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Christopher Harper has been a successful freelance tech writer specializing in PC hardware and gaming since 2015, and ghostwrote for various B2B clients in High School before that. Outside of work, Christopher is best known to friends and rivals as an active competitive player in various eSports (particularly fighting games and arena shooters) and a purveyor of music ranging from Jimi Hendrix to Killer Mike to the Sonic Adventure 2 soundtrack.
-
kyzarvs ReplyUsers of recent Canon i-Sensys printers should be wary of having their printers online due to seven critical vulnerabilities, which can be accessed by unauthenticated remote attackers
Who opens a port-forward to their printer? This is further explained in the link in the excerpt I've quoted:
These vulnerabilities suggest the possibility that, if a product is connected directly to the Internet without using a router (wired or Wi-Fi), an unauthenticated remote attacker may be able to execute arbitrary code on the device. They may also be able to target the product in a Denial-of-Service (DoS) attack via the Internet.
Okay, so they have vulnerabilities to local attacks which is arguably more pressing and an excuse for the author to discuss the merits of true guest wifi networks for example, but for e-management, they are (like almost everything else remotely managed) designed to connect to a processing server from behind a firewall, they don't need to be accessible by the internet at large. Unless your methodology of choice is to give your printer it's own WAN IP or set it up as a DMZ, this is very much in the realms of theoretical, surely? Being Online as the article states in its opening paragraph isn't the problem - you could turn off all remote management and still have a LAN issue.