Raspberry Pi Detects Ghost Aircraft Using SDR

Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Angelina Tsuboi has taken our favorite SBC, the Raspberry Pi, to the skies with her latest project. Tsuboi works as a pilot and has cybersecurity experience, making this project a no-brainer. She created what she calls Fly Catcher—a Pi-powered system that can detect false aircraft using Automatic Dependent Surveillance–Broadcast (ADS-B).
Aircraft use ADS-B signals to relay their respective location information. Hackers can create false readings that suggest an aircraft is nearby using ADS-B. Fly Catcher works by monitoring the 1090MHz frequency and can determine whether or not a potential aircraft is genuine thanks to a neural network developed just for this project.


The main board behind this project is a Raspberry Pi. It uses a custom neural network developed in Python to analyze ADS-B signals. This algorithm was trained on accurate ADS-B data to recognize actual flight data and fed false aircraft readings using SDR, just like a real hacker could use in an attack.
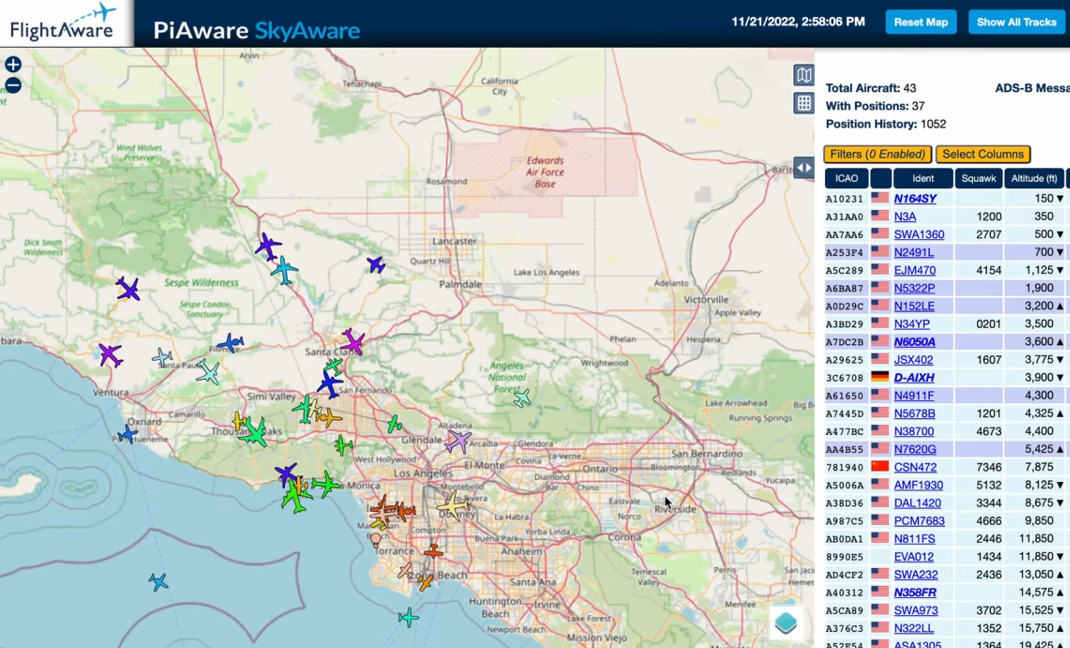
Tsuboi uses a Raspberry Pi 3 B+ connected to a 1,090 MHz antenna. It uses FlightAware SDR and can read ADS-B signals in real-time. To put the unit to the test, Tsuboi took it on an hour-long flight over Los Angeles. You can see this flight on her YouTube channel, where she details the project's inner workings.
Tsuboi was kind enough to make the project open source and has shared the source code for anyone wanting to check it out. With the proper hardware, you must copy the Flight Catcher repository, which can be found on GitHub.
To get a closer look at this Raspberry Pi project, check out the official Fly Catcher project page at Hackster.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Ash Hill is a contributing writer for Tom's Hardware with a wealth of experience in the hobby electronics, 3D printing and PCs. She manages the Pi projects of the month and much of our daily Raspberry Pi reporting while also finding the best coupons and deals on all tech.
-
mrv_co I see the words 'hacker' and 'attack' used. How prevalent is ADS-B 'hacking' and what is the potential 'attack' vector exactly? Clogging up ADS-B with non-existent aircraft?Reply -
bit_user To properly train a classifier, you need positive and negative examples of whatever you're interested in detecting. I wonder what were the negative examples? Did she inject her own fictitious reports into the training data? If so, how does she know it would work with someone else's fictitious reports?Reply
From a cybersecurity perspective, it's a bad idea to publish the classifier, because an adversary could use it to train their own model for generating plausible ghost readings and end up with something that's very good at fooling hers.
IMO, the proper way to solve this problem is by integrating it with air traffic control radar and linking flights back to known observations and flight manifests. They can then try to localize known false reports and hopefully get some law enforcement to use RF tracking equipment to try and find the transmitters of these false broadcasts.
