Engineer hacks his Sleep Number bed, reveals potential backdoor and security vulnerability
Allowing a third party to SSH into a device on your local network might not be desirable.

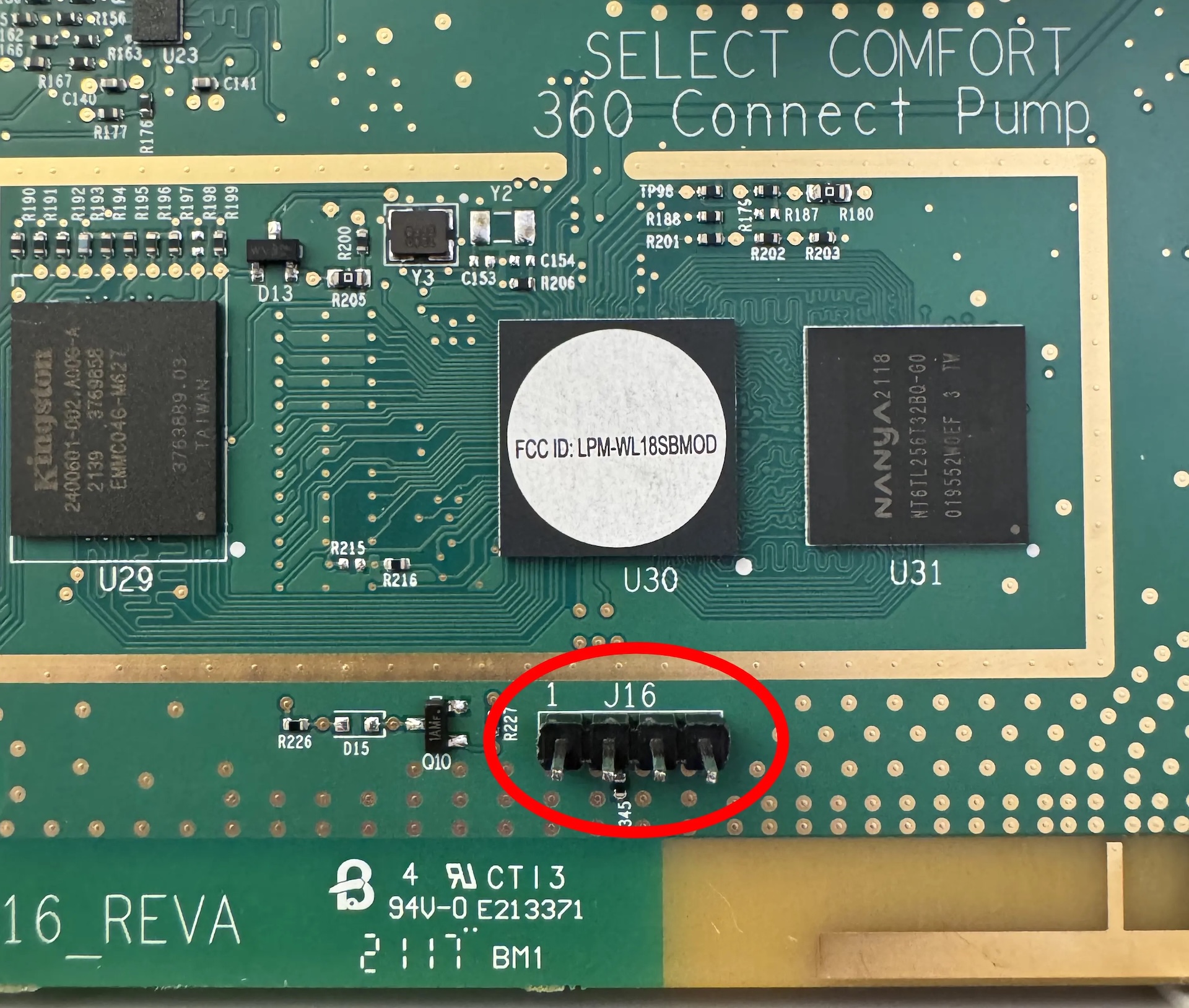
Modern Sleep Number beds are marvels, tracking your sleep, breathing, and heart rate and even maintaining the mattress temperature to your liking. One computer engineer has also figured out how to root the bed’s control hub to allow local control. Along the way, he also made a discovery that may trouble you: a backdoor-like connection that allows Sleep Number to remotely connect to your bed’s hub at will without your knowledge.
Dillan Mills discovered all this after Sleep Number asked him to turn off a Homebridge plugin he’d developed to deactivate some of the bed’s features and run smart home automation if its sensors detected nobody was laying on the mattress. Since the plugin had grown in popularity and polled Sleep Bed’s servers every five seconds, it significantly strained the company’s public servers.
So, Mills set out to find a way to access the bed locally and bypass Sleep Number’s servers altogether. Poking around inside the controller hub for his Sleep Number bed with a UART-TTY device, he eventually struck gold and was able to access the hub’s device console. Looking for a “backdoor” that would give local access to the hub without hooking up a UART reader, he found something else instead.
Sleep Number has a backdoor into the controller hub, allowing it to SSH into the hub. While Mills acknowledges that this is likely for maintenance purposes, the fact that it’s undocumented and secret is disconcerting. After all, it presents a point of entry to your home network that you have no control over and may not even know about. On top of that, the controller hub runs a version of Linux that dates back to 2018.
There is good news, though. Mills was able to root the device and wrote a tutorial to enable local network control over the bed. This way, you can disconnect the bed from your Wi-Fi network and use Bluetooth to control the settings and monitor the bed’s sensors and status.
The process does require some technical knowledge and some hardware. The tutorial is well-written, though, and the hardware you need is fairly inexpensive. You can choose to connect a USB-to-UART reader when you need to access the device console or permanently install a Raspberry Pi Pico W to enable SSH access without opening the hub and connecting the reader.
Once you’ve rooted your bed’s hub, Mills’s tutorial walks you through creating a local network control and monitoring server. This is useful not only for taking control of your bed without connecting to Sleep Number’s server. It could also be the key to keeping your bed “smart” if Sleep Number folds or shuts down the servers, usually making the bed more than a “dumb” mattress.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Jeff Butts has been covering tech news for more than a decade, and his IT experience predates the internet. Yes, he remembers when 9600 baud was “fast.” He especially enjoys covering DIY and Maker topics, along with anything on the bleeding edge of technology.
-
CmdrShepard ReplyYou see, I had set the plugin to request data from the SleepIQ API every 5 seconds to get an accurate reading on the bed presence value. Multiply that by the couple thousand users of the plugin at that point and the result was enough strain on their network that they had taken notice and started looking for the cause. They also weren't too fond of the branding of the repository, since to the untrained eye it looked like an official Sleep Number tool, which it definitely was not. Oh well, lessons learned, I shut it down.
I wonder what lesson he learned?
Hopefully it's "don't be a giant douche when you write software for public use that relies on 3rd party infrastructure".
On a side note, this article talks about a backdoor and the original article also talks as if there is a backdoor in software but I am just not seeing it. Having a working UART header on the PCB to which you have to soldier pins to be able to gain root access doesn't count as a backdoor in my book. -
mhmarefat Thank you Tom's Hardware for this article. Also thank you for your other articles informing people about Microsoft's AI bull and other Corporate BS claims such as ChatGPT and the likes of it being able to replace journalism, etc... but these are not enough. Only informing people is no longer enough. People need to know how they can stand up for themselves and fight back. Tom's Hardware needs to inform people how they can fight back on the legal side against these "Tech Scoundrels" who think they can get away with implementing such backdoors and disrespecting human rights just because they have trillions/billions of dollars?!Reply
The last thing today's world corporations think about is respecting Human dignity. TH, please do not wait for anyone. Lead they way in informing people on lawful ways they have that can bring these corporate douches back to their place.
You can start by asking big techs such as Intel and AMD what are they doing with techs such as Intel Mangement Engine and AMD Secure Technology? By whose persmision they have implemented backdoors on people's hardware? People need to stand up against these low-life techniques and hit back and hit back HARD to preserve their rights and dignity.
Tom's Hardware can start informing people of lawful ways they have to defend themselves against predatory corporate behaviour and rid themselves of these invasive technologies. Simply reporting that some corporatation is stealing/selling people's data or is implementing backdoors to their hardware and moving on is not enough anymore.
Sorry for my long post! -
derekullo Reply
Don't buy products you don't like.mhmarefat said:Thank you Tom's Hardware for this article. Also thank you for your other articles informing people about Microsoft's AI bull and other Corporate BS claims such as ChatGPT and the likes of it being able to replace journalism, etc... but these are not enough. Only informing people is no longer enough. People need to know how they can stand up for themselves and fight back. Tom's Hardware needs to inform people how they can fight back on the legal side against these "Tech Scoundrels" who think they can get away with implementing such backdoors and disrespecting human rights just because they have trillions/billions of dollars?!
The last thing today's world corporations think about is respecting Human dignity. TH, please do not wait for anyone. Lead they way in informing people on lawful ways they have that can bring these corporate douches back to their place.
You can start by asking big techs such as Intel and AMD what are they doing with techs such as Intel Mangement Engine and AMD Secure Technology? By whose persmision they have implemented backdoors on people's hardware? People need to stand up against these low-life techniques and hit back and hit back HARD to preserve their rights and dignity.
Tom's Hardware can start informing people of lawful ways they have to defend themselves against predatory corporate behaviour and rid themselves of these invasive technologies. Simply reporting that some corporatation is stealing/selling people's data or is implementing backdoors to their hardware and moving on is not enough anymore.
Sorry for my long post!
Eventually that company will go out of business due to loss of revenue.
Switch to ARM, get a normal bed... whatever makes you feel safe