New 'Kemoge' Android Adware Spreads Through Third-Party App Stores And Ad Networks
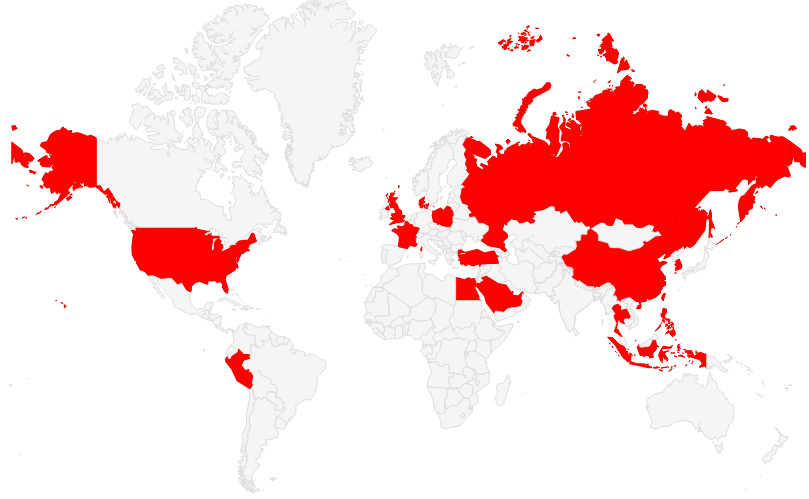
FireEye, an American security company, discovered a new malicious adware family originating in China, which affects users from over 20 countries. The adware comes bundled with many popular repackaged apps in third party stores and allows for complete takeover of users' devices.
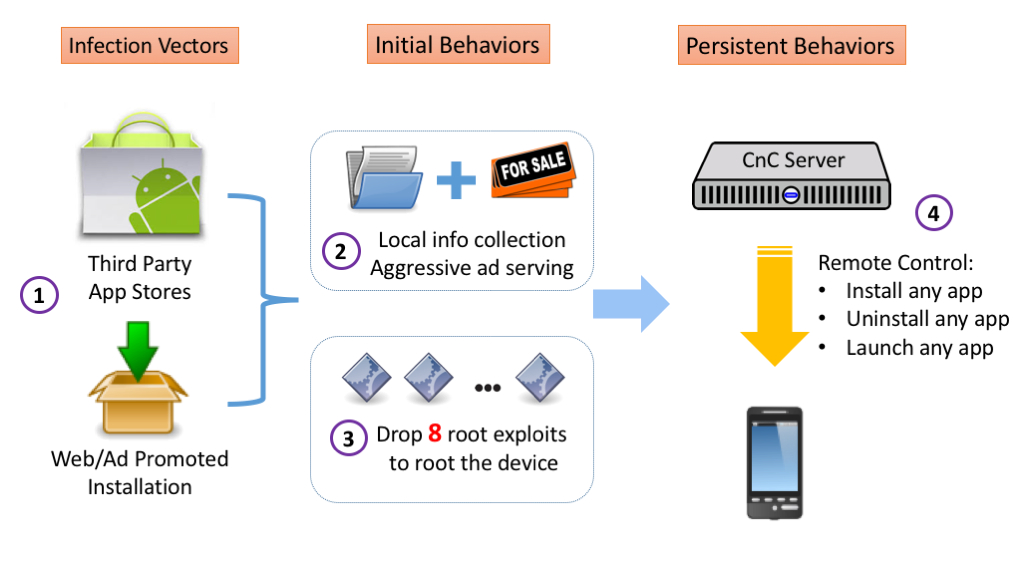
The malicious entities behind the Kemoge adware (named after the kemoge.net command and control server) upload popular applications to third party app stores that are already injected with the adware. Then they promote the apps through ad networks that themselves may infect users through web installs. The ad networks that can gain root privilege through various vulnerabilities found in certain browsers can also automatically install the malware on devices.
On the initial launch of the adware, Kemoge collects device information and uploads it to the server. Then it starts serving ads from the background, which appear all the time, even on the home screen.
After that, Kemoge delivers a .zip payload to the devices, which is encrypted multiple times and is made to look as an .mp4. file. Once it arrives on the device, the file is decrypted to unload eight different root exploits, some of which are used by the open source modding community to install ROMs on devices.
After gaining persistent root, it infiltrates itself further into the system with names similar to the launcher service or other services such as the ones from Facebook or Google. To evade detection, the malware contacts only its command and control server after first launch, or 24 hours after its last command.
In each communication, it transmits the IMEI, IMSI, storage info, and installed app info to the kemoge.net remote server. Then, the server can send a command to uninstall certain apps (such as anti-virus applications), launch other apps, or download and install apps from URLs given by the server. These actions can be used to launch further attacks, according to FireEye. Presently, FireEye researchers were still able to see that the kemoge.net command and control server was up and running.
FireEye believes that the adware was written by Chinese developers and that the threat is significant because it's spreading on a global scale. The company suggested that you:
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Never click on suspicious links from emails/SMS/websites/advertisements.Don't install apps outside the official app store.Keep Android devices updated to avoid being rooted by public known bugs. (Upgrading to the latest version of OS will provide some security, but it does not guarantee that you will remain protected.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
targetdrone "Keep Android devices updated to avoid being rooted by public known bugs. (Upgrading to the latest version of OS will provide some security, but it does not guarantee that you will remain protected."Reply
That should read "buy a newer andoird device for the latest security updates" because Carriers do not release Android updates. -
blazorthon Reply"Keep Android devices updated to avoid being rooted by public known bugs. (Upgrading to the latest version of OS will provide some security, but it does not guarantee that you will remain protected."
That should read "buy a newer andoird device for the latest security updates" because Carriers do not release Android updates.
They usually do for the decent phones, granted not as long nor fast as they should. Updates aren't such a problem for Nexus devices. -
ErikVinoya Reply"Keep Android devices updated to avoid being rooted by public known bugs. (Upgrading to the latest version of OS will provide some security, but it does not guarantee that you will remain protected."
That should read "buy a newer andoird device for the latest security updates" because Carriers do not release Android updates.
Samsung says: How adorable