New 'RuMMS' Android Malware Family Infects Smartphones Over SMS In Russia
FireEye, a U.S. network security company, uncovered a new Android malware family infecting smartphones in Russia through SMS phishing.
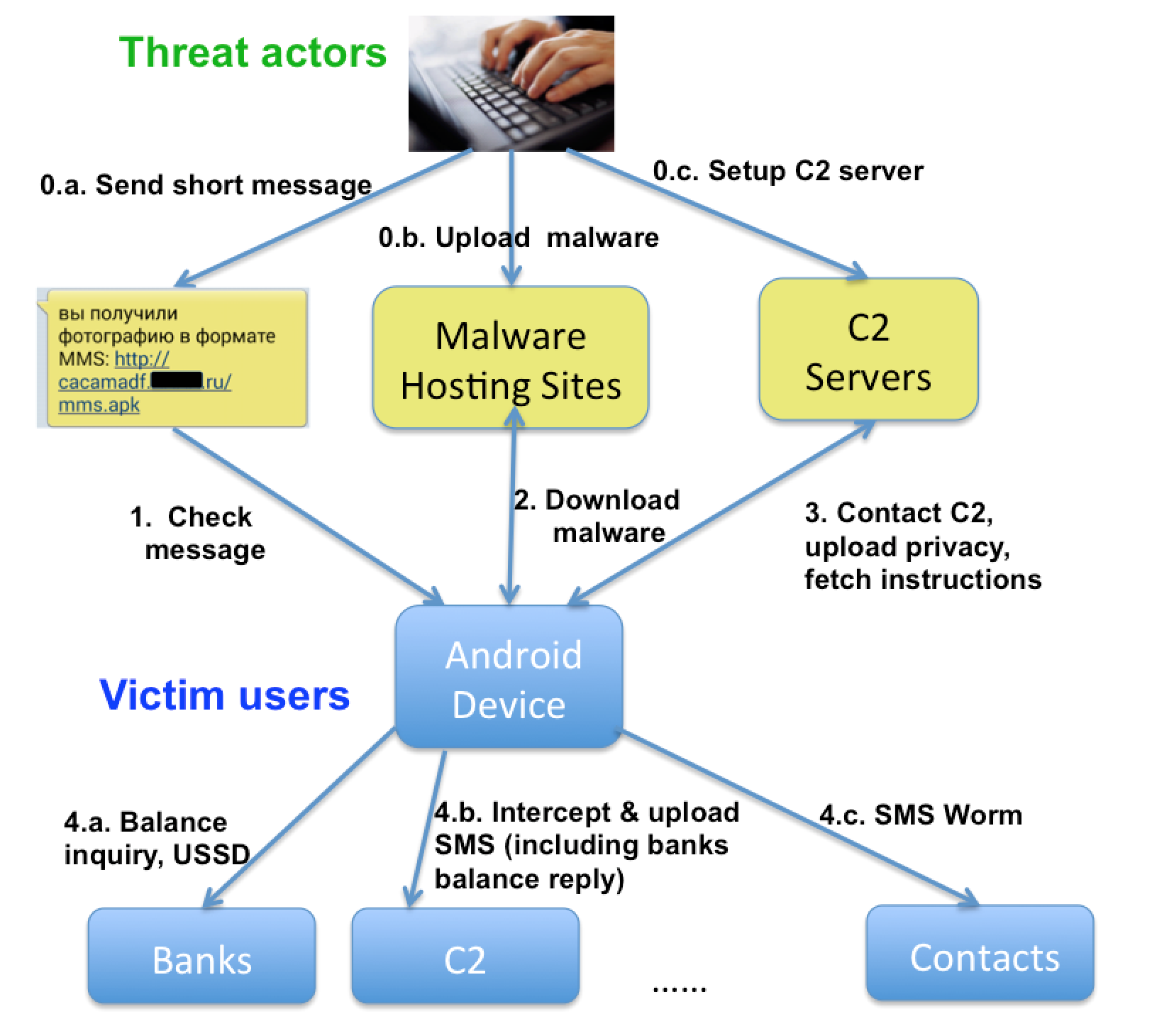
To infect the potential victims, the malicious actors send them SMS texts containing links in the form of hxxp://yyyyyyyy[.]XXXX.ru/mms.apk, which is why FireEye has given the malware the name of “RuMMS.” The people who click on those links then become infected by the malware.
The earliest version of the malware can be traced back to January 18, 2016, and so far FireEye has found over 300 samples of the malware in the wild. Once installed, the malware requests device administrator privileges. Then, it starts running in the background, performing the following malicious actions:
Sending device information to a remote command and control (C2) server.Contacting the C2 server for instructions.Sending SMS messages to financial institutions to query account balances.Uploading any incoming SMS messages (including the balance inquiry results) to the remote C2 server.Sending C2-specified SMS messages to phone numbers in the victim’s contacts.Forward incoming phone calls to intercept voice-based two-factor authentication.
All of the actions can be fully controlled by the command and control (C2) server, which can specify the message contents to be sent, the time period in which to forward the voice call, and the recipients of outgoing messages.
FireEye used an emulated Android device to investigate the RuMMS malware. During one of the sessions, the C2 server commanded the malware to send four different SMS messages to four different phone numbers, which belonged to Russian financial institutions. At least three of the messages were intended to check a user’s account balance at the bank.
Through further investigation on Russian forums, FireEye learned that multiple victims had some funds stolen from their banking accounts after they were infected by RuMMS. FireEye claimed that there have been at least 2,729 infections since January.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
FireEye security researchers said that they haven’t seen any samples of the malware on the Play Store. Google is rather good at keeping the store clean of malware, and if malware does appear there, the company is quick to take it down before too many people get infected. This is why the SMS vector of infection looks much more appealing to these malware makers.
FireEye recommends that smartphone users don’t click on links that come in SMS messages, especially if they don’t know their origin. Users are also encouraged to install apps only from the Google Play Store.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
ammaross If you leave your phone defaulted to only allowing Play Store apps to be installed, you have no problem. Might as well run a story about how China has iPhone malware too.Reply -
Mobius_08 Dont mobile browsers like chrome sandbox web sessions? Or are these users installing the malware and agreeing to the permissions?Reply -
Lucian Armasu ReplyDont mobile browsers like chrome sandbox web sessions? Or are these users installing the malware and agreeing to the permissions?
The users would have to have installing apps from other sources enabled first, and they'd also need to agree to give device administrator rights to the malware, so it's not exactly automatic. The source post doesn't describe which Android vulnerabilities the malware is using, but it's likely taking advantage of various unpatched vulnerabilities in older Android phones that aren't up to date.