Hackers Exploit 19-Year-Old WinRAR Vulnerability
WinRAR's unlimited trial period has made the compression tool so popular that paying for it has become a meme. The program is said to be used by 500 million people, many of whom are affected by a 19-year-old vulnerability that's still being exploited today, as recent McAfee research has made apparent.
Check Point Research revealed the vulnerability on February 20. On Thursday, McAfee Labs said it observed "over 100 unique exploits and counting, with most of the initial targets residing in the United States at the time of writing" in the first week since Check Point made its revelation. Hackers are rushing to take advantage of the vulnerability before those 500 million people install the patched version of WinRAR.
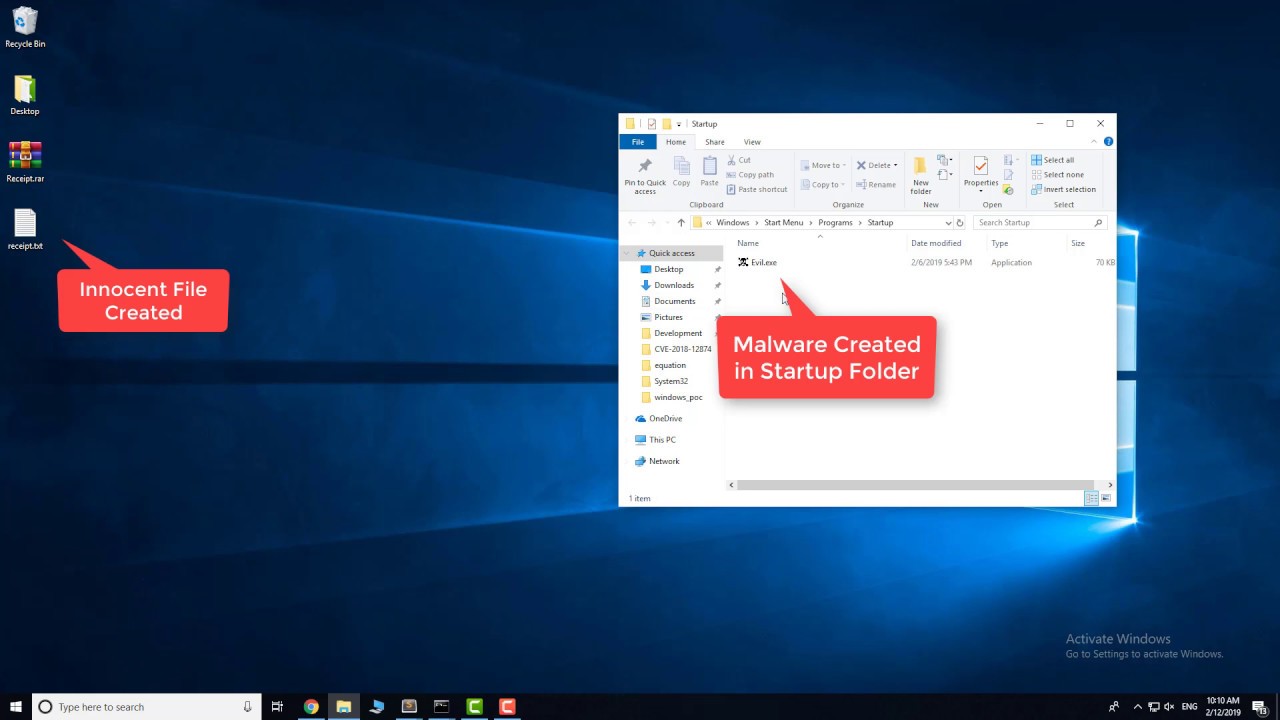
The vulnerability itself, according to Check Point, lets hackers "gain full control over a victim's computer" by "just extracting an archive." The issue lies with "an old, dated dynamic link library (dll) that was compiled back in 2006 without a protection mechanism (like ASLR, DEP, etc.) and is used by WinRAR."
Check Point published a YouTube video demonstrating the exploit:
The discovery led WinRAR's creator, Rarlab, to drop support for the vulnerable format (UNACEV2.DLL) from WinRAR version 5.70. The company said UNACEV2.DLL hadn't been updated since 2005, and because it didn't have access to the source code, it couldn't resolve the problem itself. So it ditched ACE archive support.
But the problem is that many people--to put it bluntly--suck at updating their software, especially when it's a free program like WinRAR that, frankly, they were probably using for pirated files anyway. Check Point's revelation gave hackers a window to exploit the vulnerability before half a billion people updated WinRAR.
McAfee said it observed the vulnerability being exploited in the U.S. a week after it was publicly revealed.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
It also noted the piracy connection: "One recent example piggybacks on a bootlegged copy of Ariana Grande’s hit album 'Thank U, Next' with a file name of 'Ariana_Grande-thank_u,_next(2019)_[320].rar'."
WinRAR users should update to version 5.70 of the program, and, if possible, refrain from using the tool to open questionable files until after interest in exploiting this vulnerability dies down.
Then maybe they should consider embracing the meme and actually buying the program so security updates like this can continue.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.