Researcher Clones Politician's Fingerprint From Public Photos
A little more than a year ago, just after Apple introduced its fingerprint-based TouchID authentication system, hackers (the good kind) from the Computer Chaos Club (CCC) announced that they could already bypass Apple's system by copying the physical fingerprints of people.
At the time, the fingerprint was photographed from a glass, and then cloned. This method has been mostly dismissed as being not too dangerous, because who's going around collecting people's glass fingerprints (other than perhaps spy agencies collecting fingerprints of important targets)?
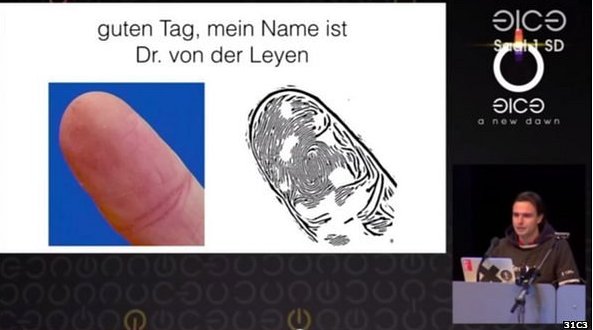
Jan Krissler, a member of the CCC, recently announced a new method of collecting and cloning fingerprints merely from publicly available photos, which could make fingerprint-based authentication systems far less secure than they've been so far.
The researcher proved this was possible by cloning the fingerprint of the German Minister of Defense, Ursula von der Leyen. He used commercially available software such as VeriFinger and a photo of the minister's hand from a recent conference.

As long as the systems that used fingerprint-based authentication are physical, such as a phone or a door, then those who steal and clone people's fingerprints should still face major hurdles because they will need physical access to those systems to make any sort of fingerprint clone.
However, if we start using fingerprints for authenticating to websites, that could be much more dangerous, because then malicious hackers could log in to those sites with cloned fingerprints. They could get those fingerprints simply by analyzing online photos of millions of people.
Even if websites eventually adopt fingerprint authentication, they will at least need to tie that authentication to a physical object that you own, whether it's your phone or PC. Then hackers would not only need to impersonate your fingerprint, but also hack into your phone or PC. That's not impossible, but it should drastically reduce the attack vector.
Stay On the Cutting Edge: Get the Tom's Hardware Newsletter
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
There are new methods of biometric authentication being developed for business customers, such as finger vein recognition, an authentication system that only works when a "live" finger is used, so despite its current flaws, biometric authentication may still prove useful in the future.
Follow us @tomshardware, on Facebook and on Google+.
-
punahou1 Politicians fingerprints are easy to obtain - just keep their glass from the cocktail party like they do in the movies LOL.Reply -
InvalidError People leave their fingerprints in hundreds if not thousands of places every day. I would consider fingerprints as INHERENTLY UNSAFE as far as biometric authentication is concerned. At the very least, you need a method to confirm that the fingerprint is a genuine biological article still attached to its original owner.Reply
Some "professional" fingerprint scanners can be fooled by a black-and-white laser-printed copy.
The biggest security issue with biometrics is that once they have been compromised, you are screwed since there is no easy way to change them and for the most part, there is no easy way to protect them either.
