Gigabyte Gets Hacked, Attackers Steal 112GB of Data Plus AMD and Intel Info
Lots of potential harm for the company
Taiwanese computer hardware giant Gigabyte suffered a ransomware attack (via The Record) by the RansomEXX hacking group. Not only did the group manage to get into the Gigabyte headquarters server, but they have stolen as much as 112GB of confidential data.
The hack took place last week and was perpetrated by RansomEXX, a group of hackers specializing in creating ransomware attacks that target high-profile companies — in this case, Gigabyte. As Gigabyte works with a lot of confidential data, such as new products and hardware, it would seem that the attackers targeted Gigabyte based on the amount of potential data which could be used for payment or leaked to the public.
According to the report, attackers stole as much as 112GB of confidential data, which includes motherboard designs, sensitive encryption keys, UEFI BIOS versions for yet-unreleased products, TPM data, and much more. Gigabyte is now in danger of all of this information making its way to the public domain. To keep that from happening, the hackers are requesting a ransom, as they're threatening to leak the data to the public and compromise Gigabyte. The data is thought to include details about the upcoming Zen 4 architecture.
The leaked documents are supposed to carry a lot of information including American Megatrends Debug documentation, Intel Ice Lake-D SKU stack update, Intel "Potential Issues" document, and AMD revisions guide amongst many others. Screenshots from private website, seen by The Record, can be seen below, with the message from the attackers.
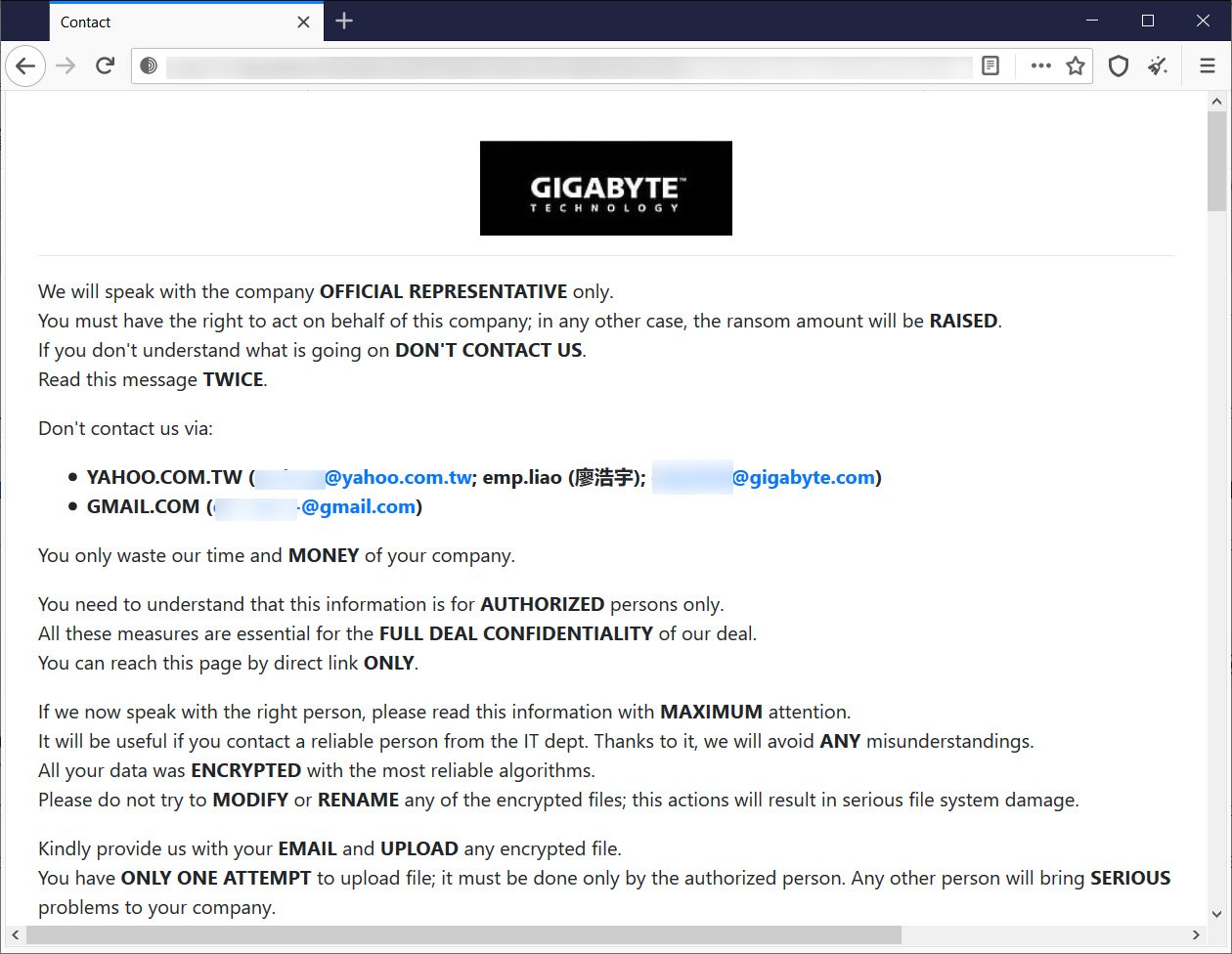
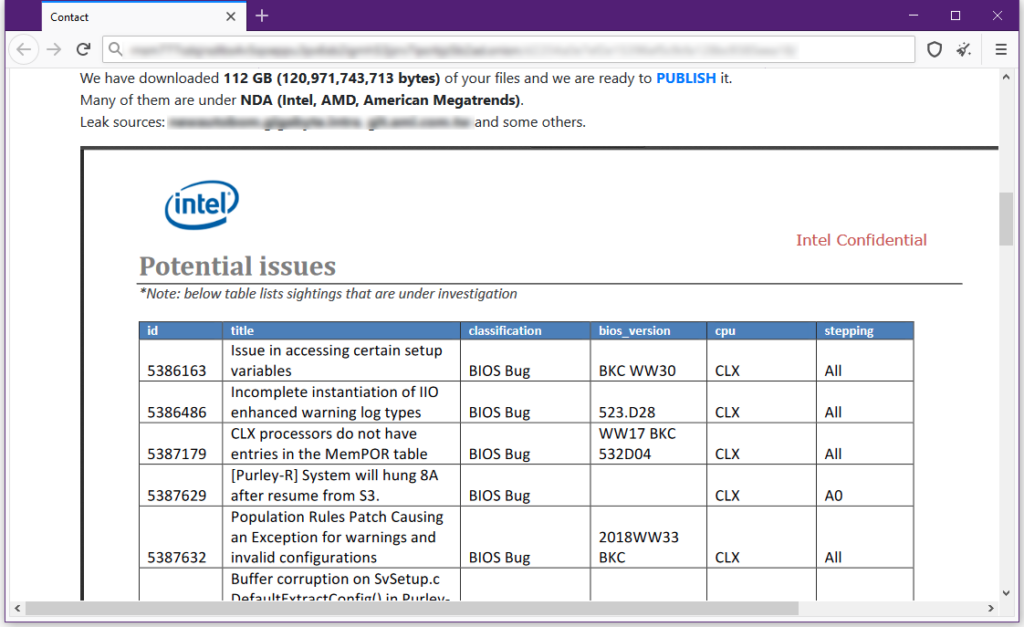
Gigabyte has not commented on this case yet and has not mentioned any talks with the ransomware hackers. The company only issued a statement that notes that the affected servers in its HQ have been isolated, and the authorities have been called to deal with the case. Of course, paying the ransom doesn't even guarantee the data won't be leaked, which is why most companies don't play ball with extortionary tactics.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
-
jamiewhite To my knowledge, this is the second Taiwanese electronics manufacturer that has been hacked in as many years. I see a pattern forming…Reply -
spentshells I knew something was up with their website a few days ago, all the contact us and certain information links were unavailable from all pages.Reply -
waltc3 GB should tell the hackers to go jump...;) I would. Screw your ransom. These guys will be caught and when they do I would not want to trade places with them. US GB site seems unscathed.Reply -
Co BIY At a high-profile high-tech company there was probably inside assistance - and also probably big country state sponsorship of the attack.Reply
I doubt ransom was the goal. Strategic info and IP are the targets worth going for at a company like Gigabyte where the defenses were probably better than business average. But ransom demands muddy the water.
Search "maskirovka" - A stratagem heavily used by at least two large powers in Asia. -
jeremyj_83 Worst part of this is GB could pay the ransom and the data could still be released. The biggest problem with digital data is that as soon as it leaves the primary location it can now be copied endless times and you can never get rid of it.Reply -
GenericUser Replyjeremyj_83 said:Worst part of this is GB could pay the ransom and the data could still be released. The biggest problem with digital data is that as soon as it leaves the primary location it can now be copied endless times and you can never get rid of it.
My understanding is that they generally tend not to do that, since it lowers their credibility for future ransoms.
If you know the attackers are going to release your stuff regardless if you pay up or not, then why pay?