Google Reports 5 Percent Of Users Infected By Ad Injectors
Google, working with researchers from the University of California, Berkeley, conducted a study that found 5 percent of users visiting Google sites were infected with Ad Injectors.
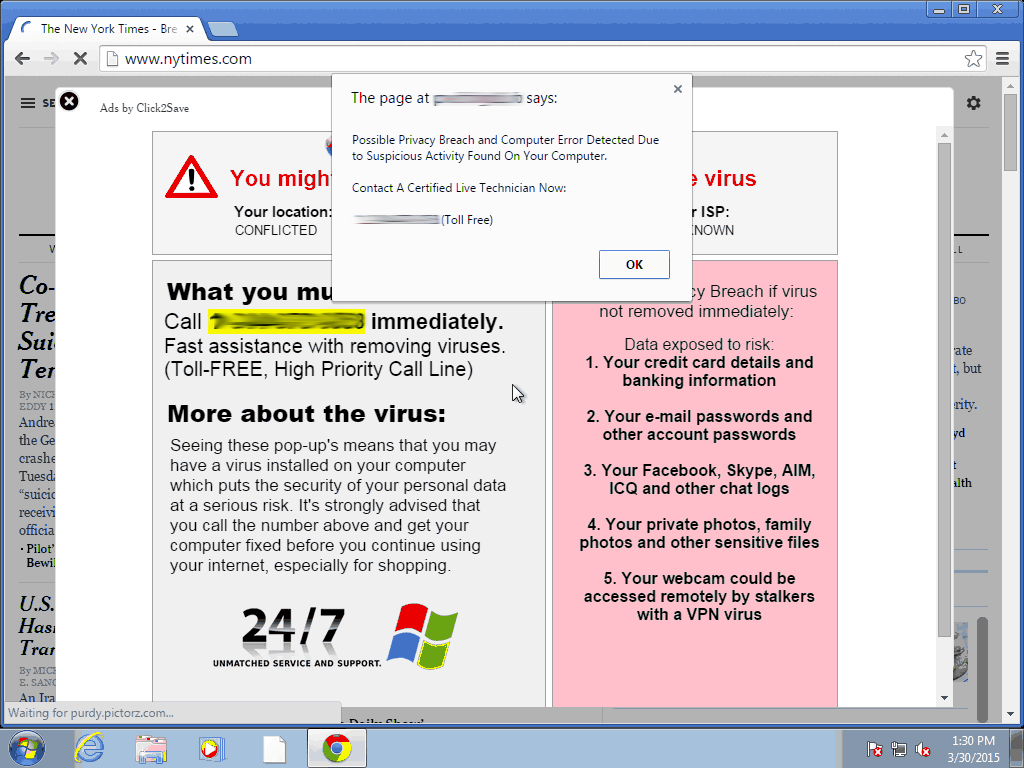
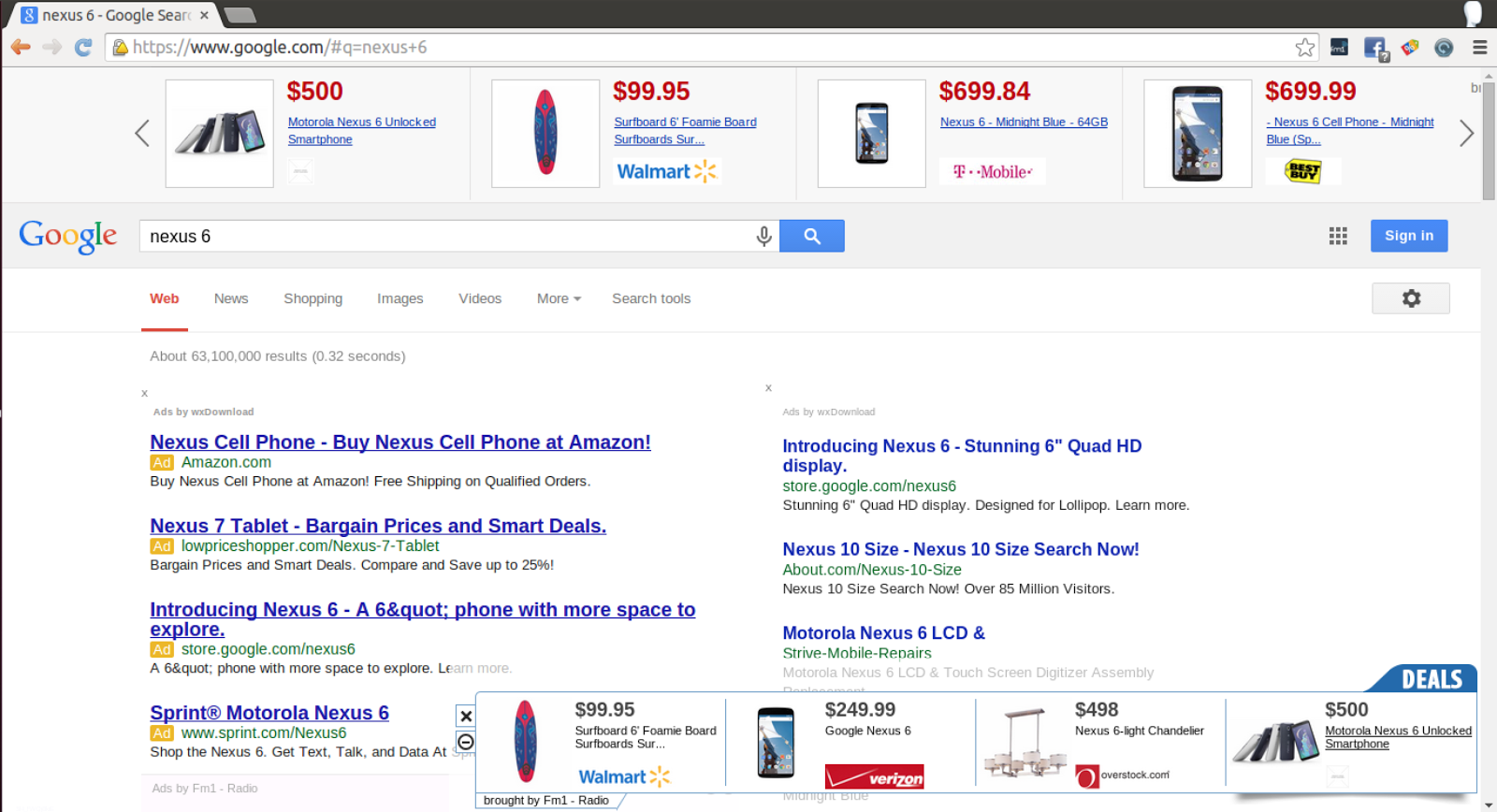
An Ad Injector is a type of adware that can put ads into pages you are viewing, replace existing ads with other ads, and block content you are trying to view. As a result of these annoying pop-ups, Google claimed it has received over 100,000 complaints from users of Google Chrome since the start of 2015.
Google said that this type of software brings a variety of problems for users, advertisers and publishers alike. The user side of the problem is easy to see, as most of us have experienced annoying ads that cover up content and seem to get in the way of our web browsing activities.
For publishers and advertisers, this type of malicious software is an even greater problem. Ad Injectors covering up content and bothering users can drive people away. Because most websites make their living off of advertising, this can drive profits down and cost sites a great deal of money.
Advertisers face similar issues, as they rely on those advertisements to help increase sales.
In the study, Google used 100 million pageviews on Google sites across Firefox, Chrome, and Internet Explorer on many platforms globally. According to the findings, Ad Injectors were found on all OSes, as well as all three web browsers. More than 5 percent of users were infected with at least one ad injector, while half of that 5 percent had at least two, and a third of that 5 percent had at least four.
The researchers took a closer look at Google Chrome extensions as well and found that 34 percent were outright malware, and 192 extensions that affected 14 million users were disabled by Google.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
In response to this research, Google is working to improve its policies and security in an attempt to reduce malicious software in its browser.
Users who suspect they might be infected with such software should take additional steps to secure their browser, such as updating security software and utilizing security extensions.
Follow Michael Justin Allen Sexton @LordLao74. Follow us @tomshardware, on Facebook and on Google+.
-
whiteodian I think I'm infected here on Tom's. Every time I move my mouse around on this page, annoying pop-ups appear all over the place and block the content of the article I am trying to read. They say AdChoices on them and are super obnoxious. I don't mind the right 1/3 of my screen having ads, but the pop-up ones drive me nuts. Also, on my phone, when I scroll the Tom's articles, I get to this point where the browser hardly moves at all until I scroll up past this annoying ad. I only have this issue on Tom's so I think the website must be infested.Reply -
LightSwordM First, you should see if they are any malicious software installed on your computer. Second, if you do, use CCleaner to do the job for you(uninstalling them). Third, if there arent any, Tom Hardware is really infested!Reply -
sykozis The last malware infection I got, came from ads on this site. The number of ads displayed is ridiculous. According to ABP, it's currently blocking 12 ads while Disconnect claims to be blocking an additional 5 ads. That's a total of 17 ads being blocked, just to make this post from the forum....and I still had an ad from Pagefair being displayed.Reply -
Kept getting this issue with extensions in Chrome on my Win7 laptop, even after deleting the files, running CC Cleaner, running extensions in developer mode, etc...Reply
I ended up just deleting Chrome altogether and use Firefox and Comodo browsers now (only) and have ZERO issues with the laptop.
This issue has not affected/appeared in my Win8.1 desktop at all and use Chrome on it almost exclusively. -
pjmelect The easy way to get rid of these Ad injectors is to reset your browser, for Chrome follow these instructions.Reply
http://www.tomsguide.com/us/reset-google-chrome-how-to,news-18821.html -
knowom ReplyFirst, you should see if they are any malicious software installed on your computer. Second, if you do, use CCleaner to do the job for you(uninstalling them). Third, if there arent any, Tom Hardware is really infested!
I always use the registry cleaner as well immediately after uninstalling a program with CCleaner.
Another thing regarding CCleaner it's also great for clearing web browser settings that try to force users into clicking on a link to install software which is rather handy. -
knowom How many of those Ad's did "Google" include of it's own? AdWords is just as much guilty of the same ad infection rate crime if not the biggest culprit of them all.Reply -
Solandri Reply
If you've signed into a Google profile with Chrome, resetting it isn't enough. Even reinstalling it isn't enough. Its config and extensions get sync'ed to the cloud, and will auto-infest Chrome when you reinstall it (or install it on a different computer) and sign in again.15589992 said:The easy way to get rid of these Ad injectors is to reset your browser, for Chrome follow these instructions.
http://www.tomsguide.com/us/reset-google-chrome-how-to,news-18821.html
You need to wipe your sync'ed profile in order to permanently eradicate the malware.
Completely uninstall and reinstall Chrome. Then, before you login to Chrome for the first time, disable sync of the item you think is causing the corruption.
Chrome -> Settings -> Advanced Sync Settings.
If you're unsure which item is causing the corruption, you'll have to figure it out through the process of elimination. If you're OK with losing all your sync'ed data, you can just disable everything, no need to find the culprit.
Now, login to Chrome and delete the sync'ed data from Google's Servers.
http://www.howtogeek.com/103655/how-to-delete-your-google-chrome-browser-sync-data/?PageSpeed=noscript -
buhusky This is easy to fix. Install Adblock Plus and also enable click-to-play in Chrome. Takes less than 60 seconds and inconvenience factor is very, very lowReply -
qlum Usually adwcleaner does a great job of cleaning the mess but personally I am kind of supprised that its only 5% that is infectedReply